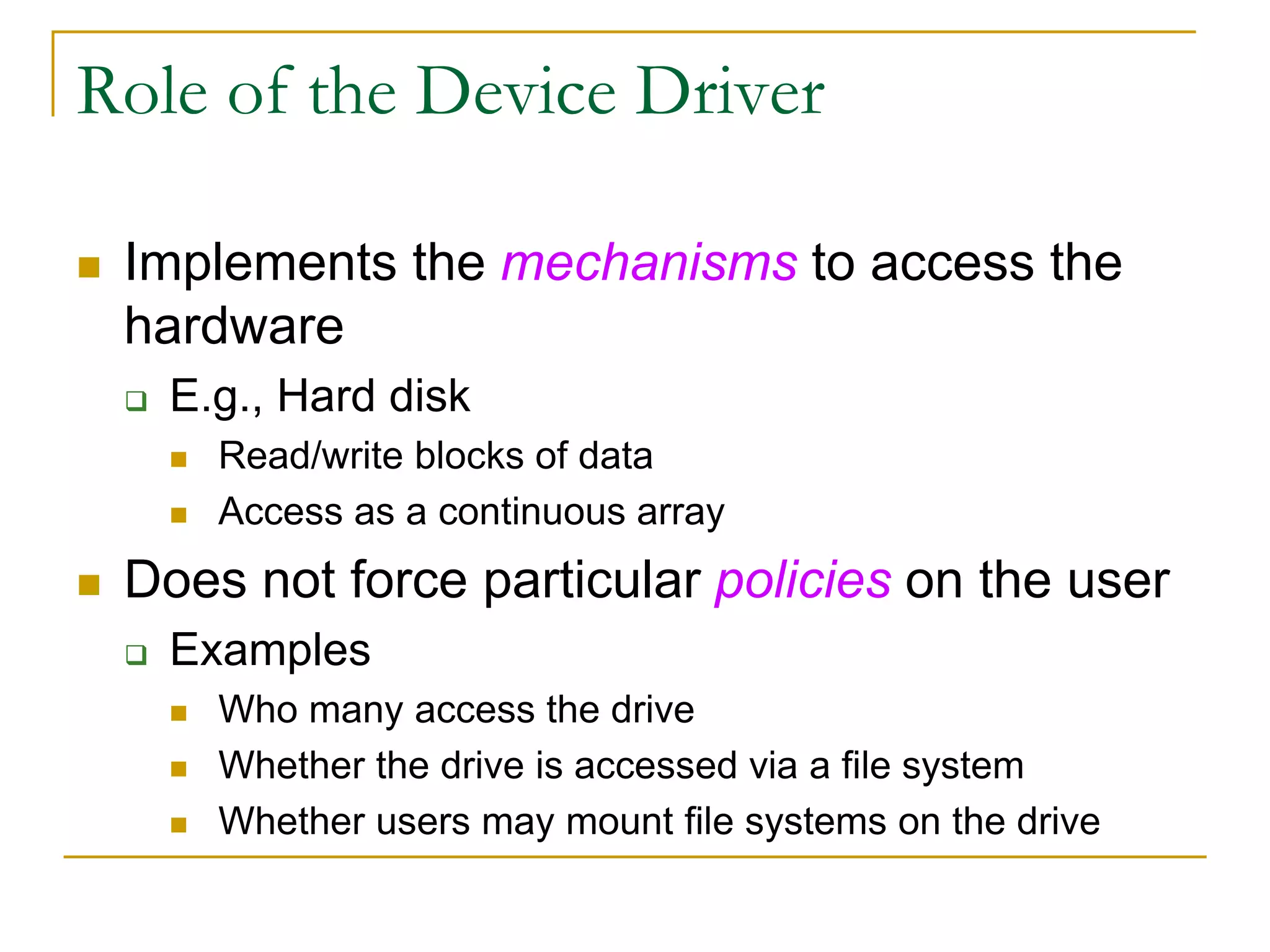
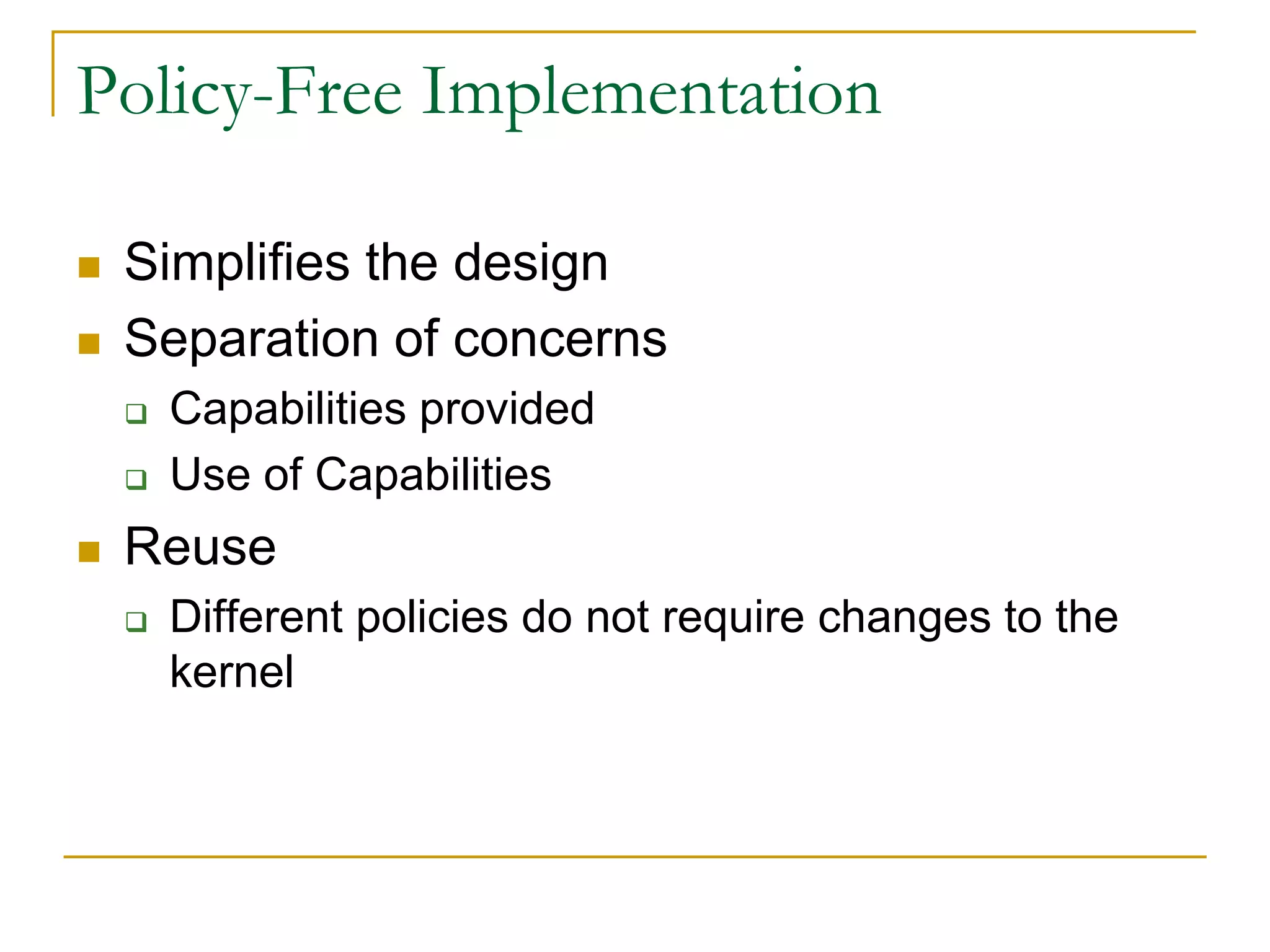
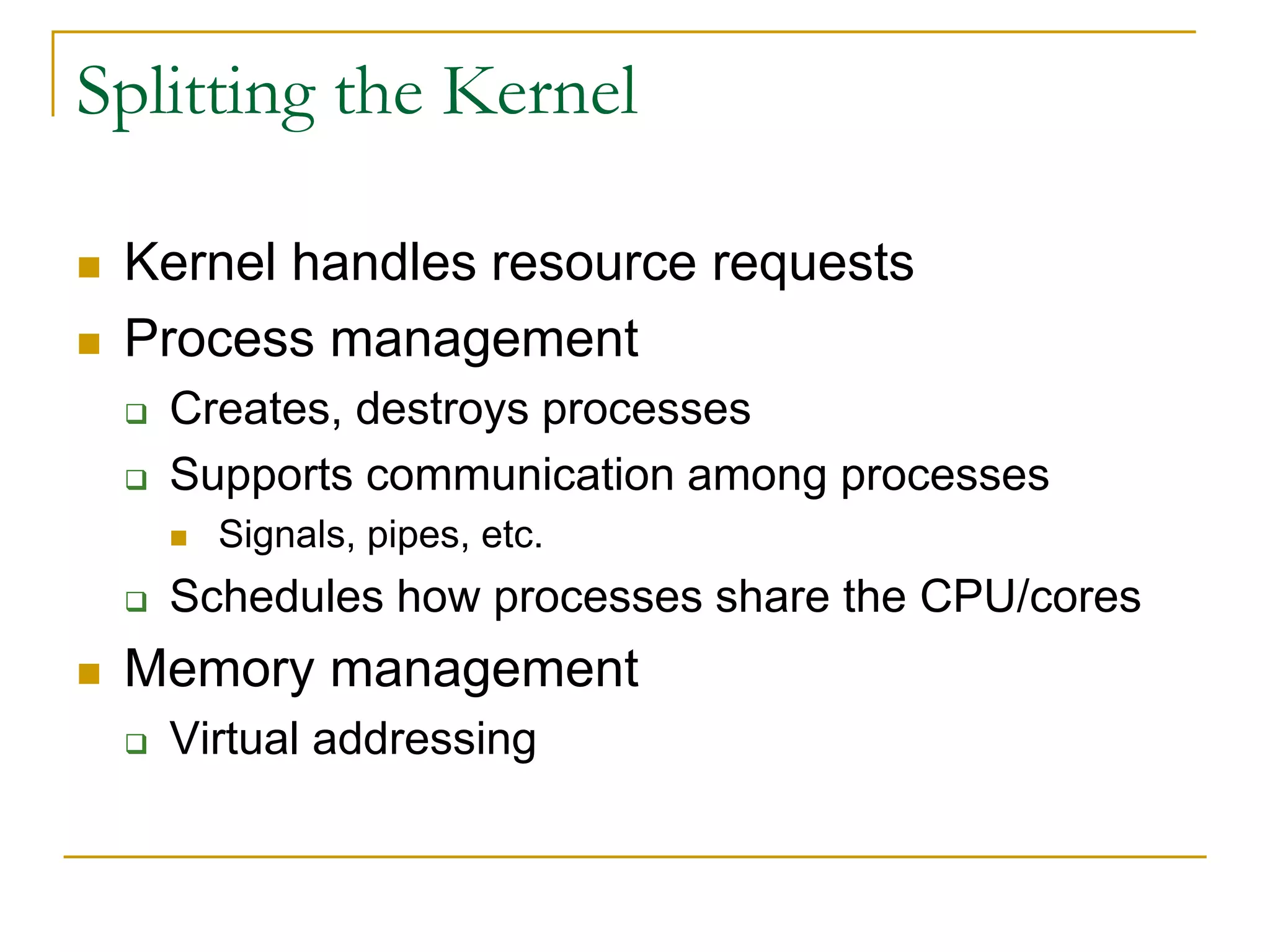
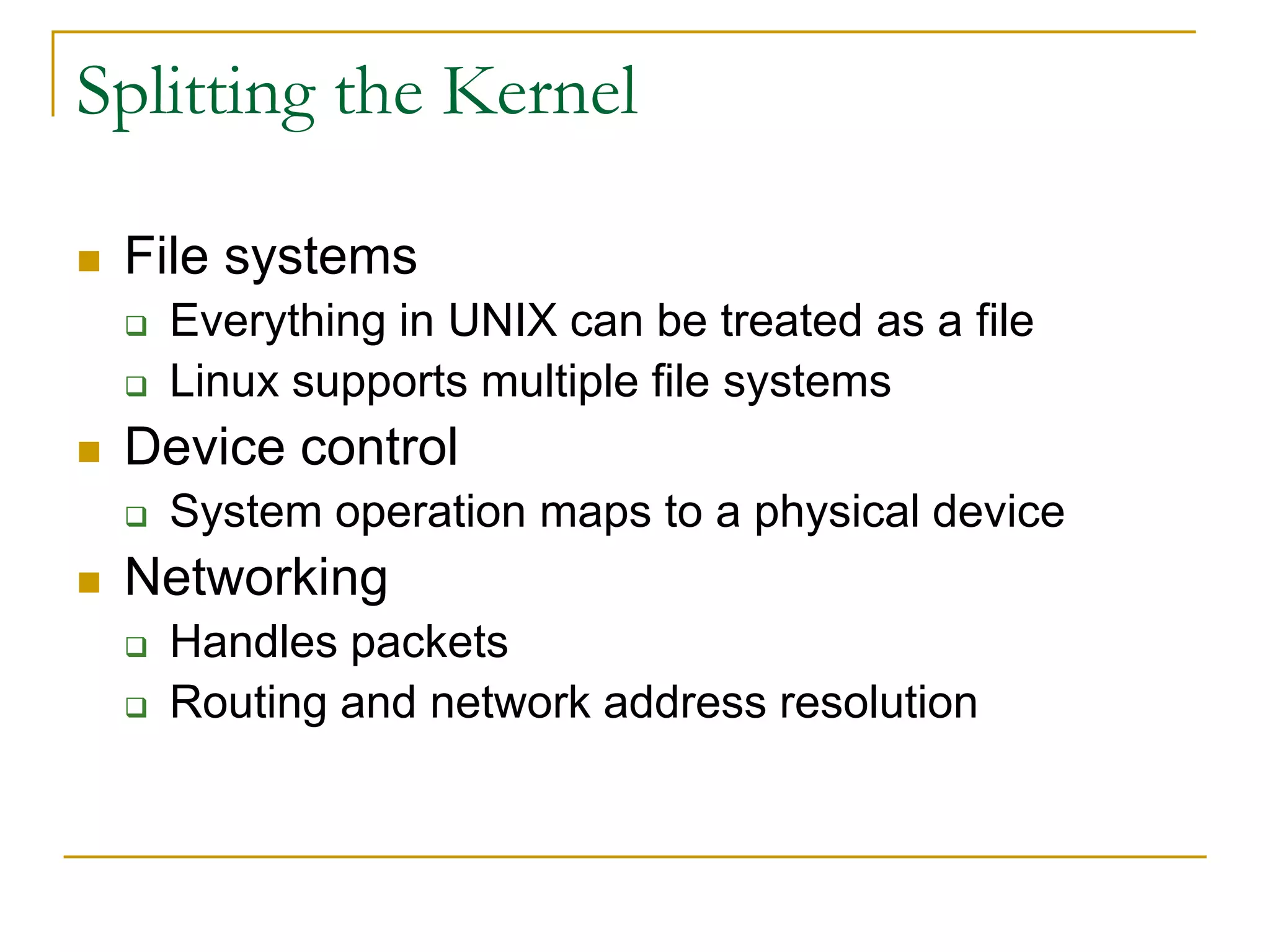
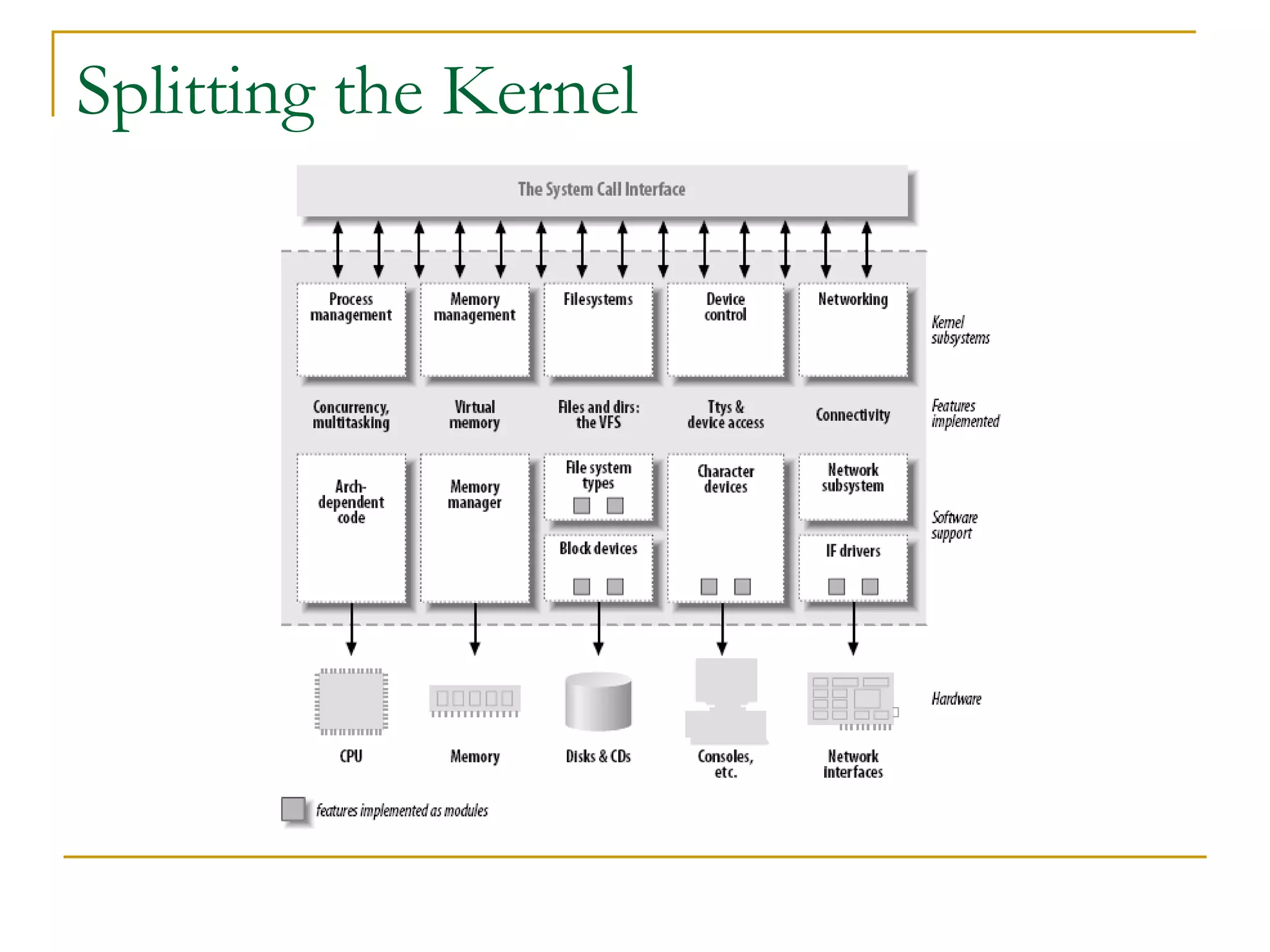
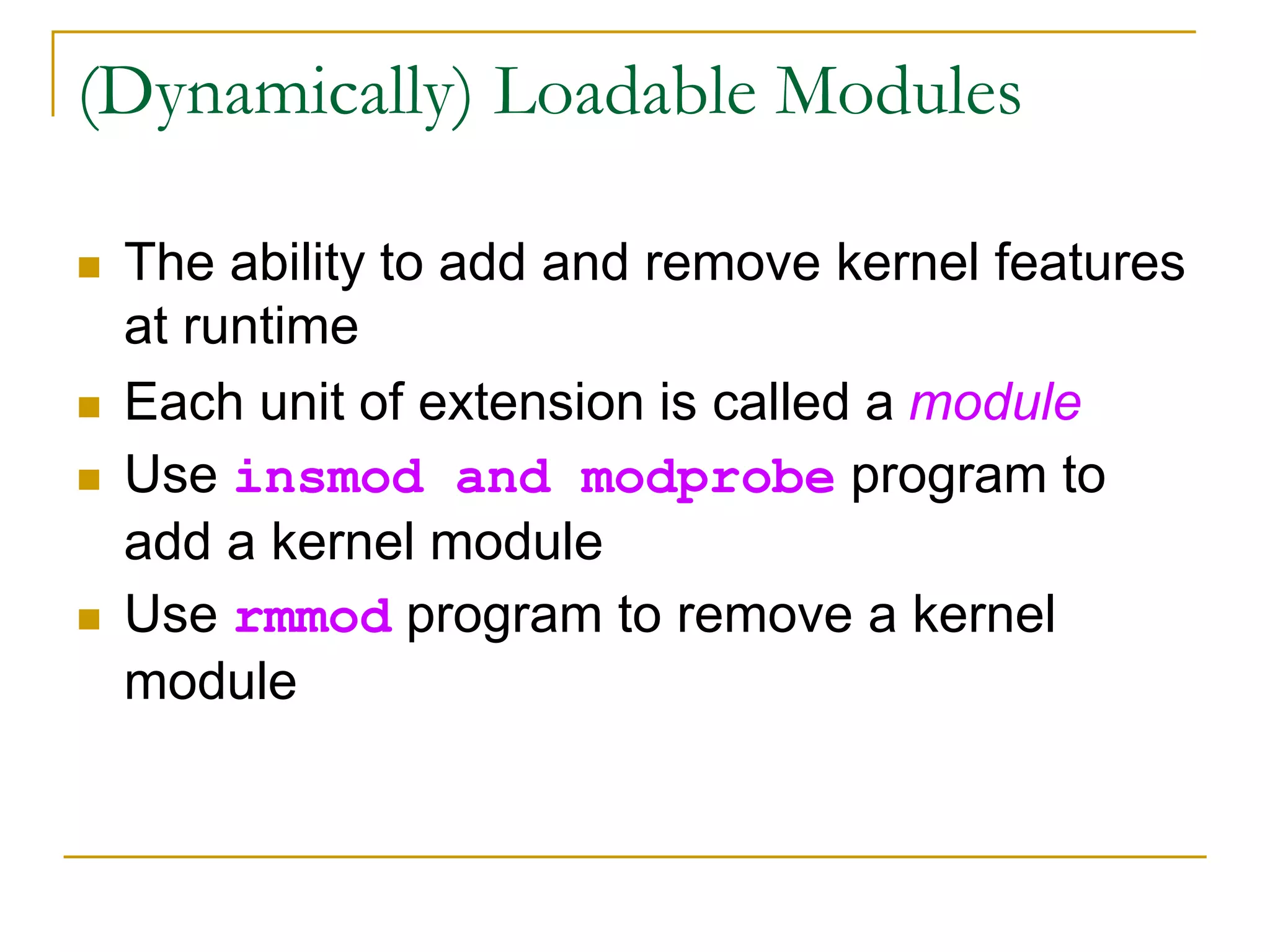
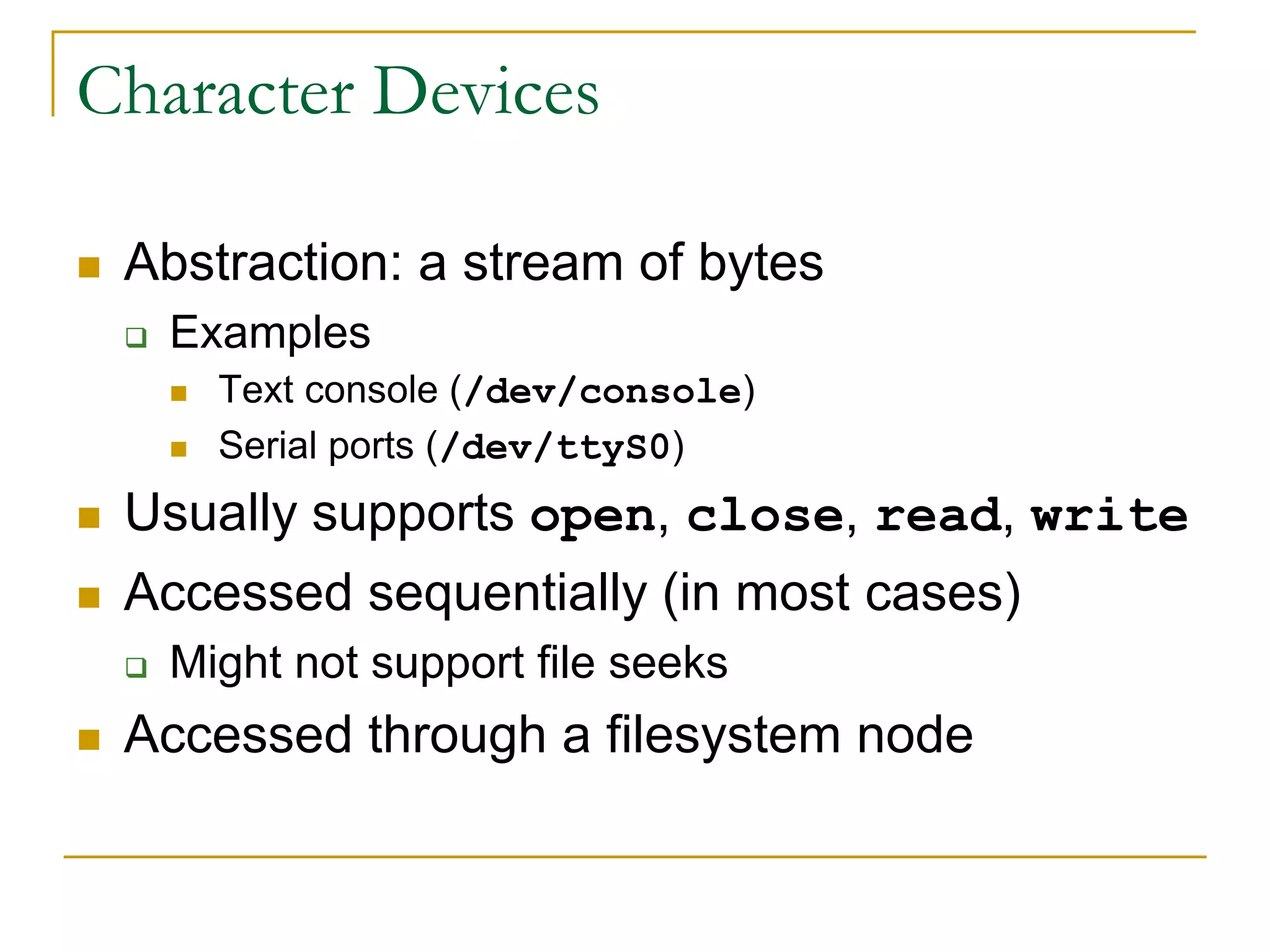
This document provides an introduction to device drivers and how they interface with the Linux kernel. It discusses how device drivers provide a standardized interface to hardware, are loaded dynamically, and implement hardware-specific operations. It also covers different types of devices, modules, and considerations for driver development like security, versioning, licensing and joining the kernel community.