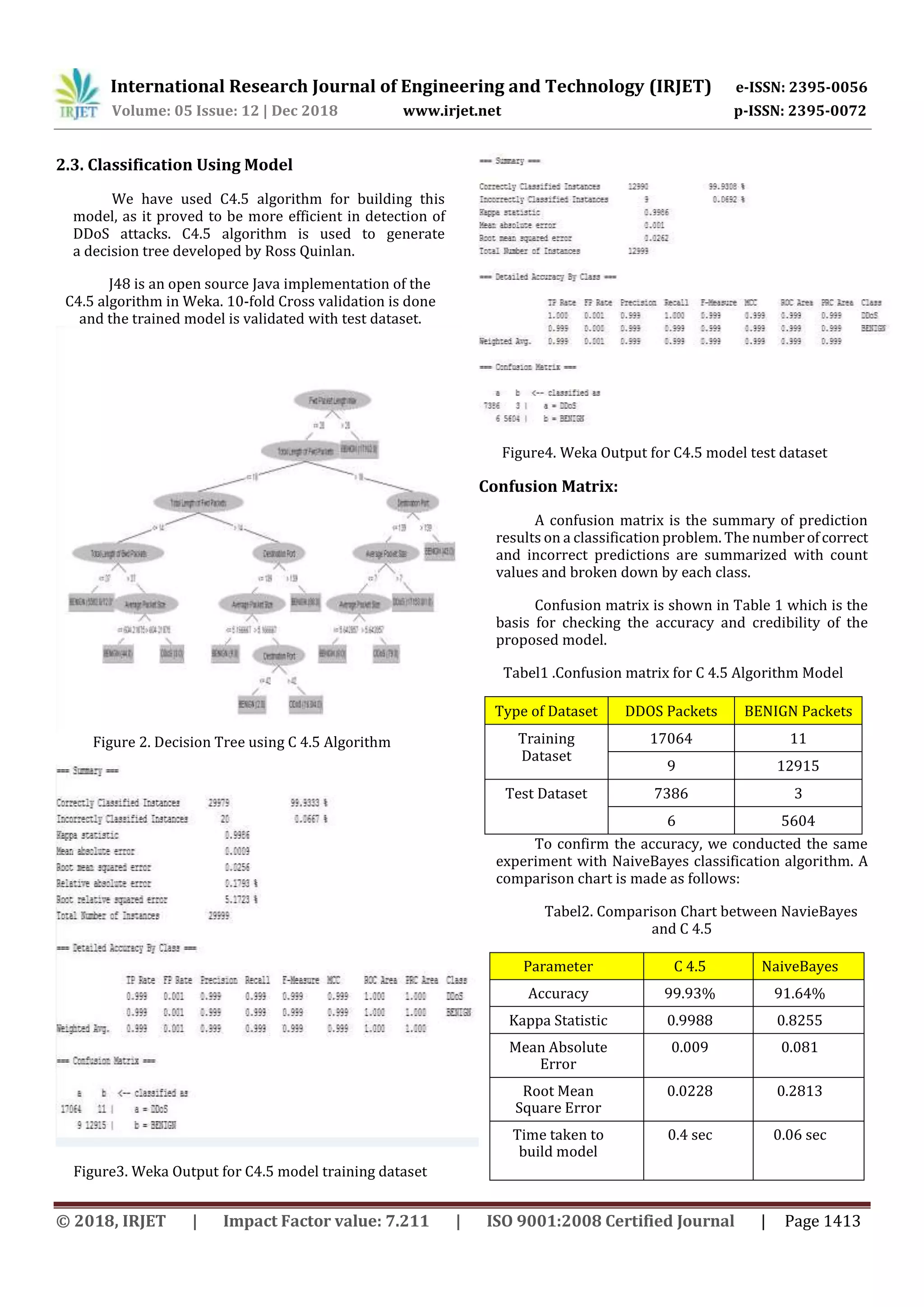
This document proposes a machine learning model using the C4.5 decision tree algorithm to detect DDOS attacks. It trains the model on DDOS attack samples from the CICIDS2017 dataset, dividing the samples into training and test data. The Weka data mining tool is used to build the model with attribute filtering and 10-fold cross-validation. The trained model is then validated on the test data to accurately differentiate between benign and DDOS flooding traffic. This combined signature-based and anomaly-based detection approach can effectively detect complex DDOS attacks.


![International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056 Volume: 05 Issue: 12 | Dec 2018 www.irjet.net p-ISSN: 2395-0072 © 2018, IRJET | Impact Factor value: 7.211 | ISO 9001:2008 Certified Journal | Page 1412 measure of abnormality and randomness. If the samples taken to analyze are from a single group, then entropy is observed to be lesser in comparison with patterns taken from multiple groups. Headers present in the sampled data are analyzed to determine theIPandportsbeforecomputing their entropy. The Detection systems aremadeinsucha way that it detects DDOS attack, in case the pattern under observation exceeds the entropy by a fixed threshold. 2. RELATED WORKS Machine learning techniques are frequently used for anomaly detection. They have received considerable attention among the intrusion detection researchers to address the weaknesses of knowledge based detection techniques. Another experiment developed on three intrusion detection models based onMulti-LayerPerceptron (MLP), C 4.5, and SVM classifiers showed that C 4.5 is the best method in terms of detection accuracy and minimum training time [2]; it achieved the accuracy rate of (99.05%). For this reason, we choose the C4.5 algorithm to detect the DDoS attacks in our proposed model. We compared the output accuracy with Naivebayes algorithm. The model proposed using C 4.5 decision tree algorithm can provide encouraging results, when combined with signature based DDOS detection systems. C 4.5 Algorithm: C 4.5 is extension of ID3 algorithm. It tries to find simple and small decision trees. C 4.5 builds decision trees from a set of training data on basis of information entropy. Entropy ) = - Iterating over all possible values of ), the conditional probability: It uses the fact that each attribute of the data can be used to make a decision that splits the data into smaller subsets. C4.5 examines the normalized information gain ratio that results from choosing an attribute for splitting the data. The attributewiththehighestinformationgainratio is the one used to make the decision.[4] Given a learning set S and a non class attribute X, the Gain Ratio is defined as: Figure1: Combined model for DDOS Detection 2.1. Input DDoS attack Data The input DDoS sample is taken from Intrusion Detection Evaluation Dataset (CICIDS2017)[1]. It contains benign and the most up-to-date common attacks, which resembles the true real-world data. The data is captured over a period of five days with diversified attacks. Low Orbit Ion Canon (LOIC) tool is used for DDoS attack generation. The incidents are more than 2 million, making the dataset comprehensive. As this dataset is huge, we choose random subset from the available data. The experiment is repeated with random input, so that the results are not biased. 2.2. Pre-processing and supervised filtering The input dataset contains a total of 78 attributes. Pre- processing is done in Weka with supervised attribute filter. This will ensure greater accuracy and less processing time for building the model. Key Chosen attributes of dataset: Maximum Packet length in Forward Direction Total Length of packet in Forward direction Total Length of packet in Backward direction Average packet size Destination port As a standard practice, training and test datasets are divided in 70:30 ratio. This dataset is taken randomly from original data and experiment is repeated to validate the consistency.](https://image.slidesharecdn.com/irjet-v5i12264-190107054458/75/IRJET-DDOS-Detection-System-using-C4-5-Decision-Tree-Algorithm-3-2048.jpg)
![International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056 Volume: 05 Issue: 12 | Dec 2018 www.irjet.net p-ISSN: 2395-0072 © 2018, IRJET | Impact Factor value: 7.211 | ISO 9001:2008 Certified Journal | Page 1414 Area under ROC, C.4.5 Model Area under ROC, Naviebayes Model 3. CONCLUSION AND FUTURE SCOPE C 4.5 DecisionTreealgorithmprovided99.93%accuracy in differentiating DDoS attack and benign traffic. Even though, the build time is more compared to Naviebayes, the accuracy level is improved significantly with C4.5 decision tree algorithm. The attribute filtration plays a major role for high accuracy and increased build speed. Combination of signature plus anomaly based model can increase the reliability in DDoS detection. This model may be used for identification of bot participating in DDoS attack so that those IP addresses could be blocked. Finally, as a future work, we are planning to develop a prototype system based on deep learning so that, better detection capabilities can be inherited by processing huge real-time streaming data. REFERENCES [1]. Iman Sharafaldin, Arash Habibi Lashkari and Ali A. Ghorbani., “Toward Generating a New Intrusion Detection Dataset and Intrusion Traffic Characterization”, 4th International Conference on Information Systems Security and Privacy (ICISSP), Purtogal, January 2018 [2] Ismanto, Heru & Wardoyo, Retantyo., Comparison of running time between C4.5 and k-nearest neighbor (k-NN) algorithm on deciding mainstay area clustering. International Journal of Advances in Intelligent Informatics. 2. 1. 10.26555/ijain.v2i1.49. [3] Marwane Zekri, Said El Kafhali, Noureddine Aboutabit and Youssef Saadi., “DDoS Attack Detection using Machine Learning Techniques in Cloud Computing Environments”, 3rd International Conference of Cloud Computing Technologies and Applications (CloudTech), October 2017 [4]. Wei Wang, 2, Sylvain Gombault, Thomas Guyet., “Towards fast detecting intrusions: using key attributes of network traffic”, Third International Conference onInternet Monitoring and Protection, pp.86-91, 2008 [5]. Agrawal, S. and Rajput, R. S., “Denial of Services Attack Detection using Random Forest Classifier with Information Gain”, International Journal ofEngineeringDevelopment and Research, September 2017](https://image.slidesharecdn.com/irjet-v5i12264-190107054458/75/IRJET-DDOS-Detection-System-using-C4-5-Decision-Tree-Algorithm-5-2048.jpg)