The document provides an overview of blockchain technology, detailing its background, key concepts, and various implementations, particularly focusing on Bitcoin and Ethereum. It highlights the mechanics of decentralized currency, the importance of consensus protocols, and diverse use cases across industries such as health care, finance, and governance. Additionally, it addresses technical aspects like cryptographic methods, mining processes, and the potential advantages of using blockchain for secure and transparent data management.


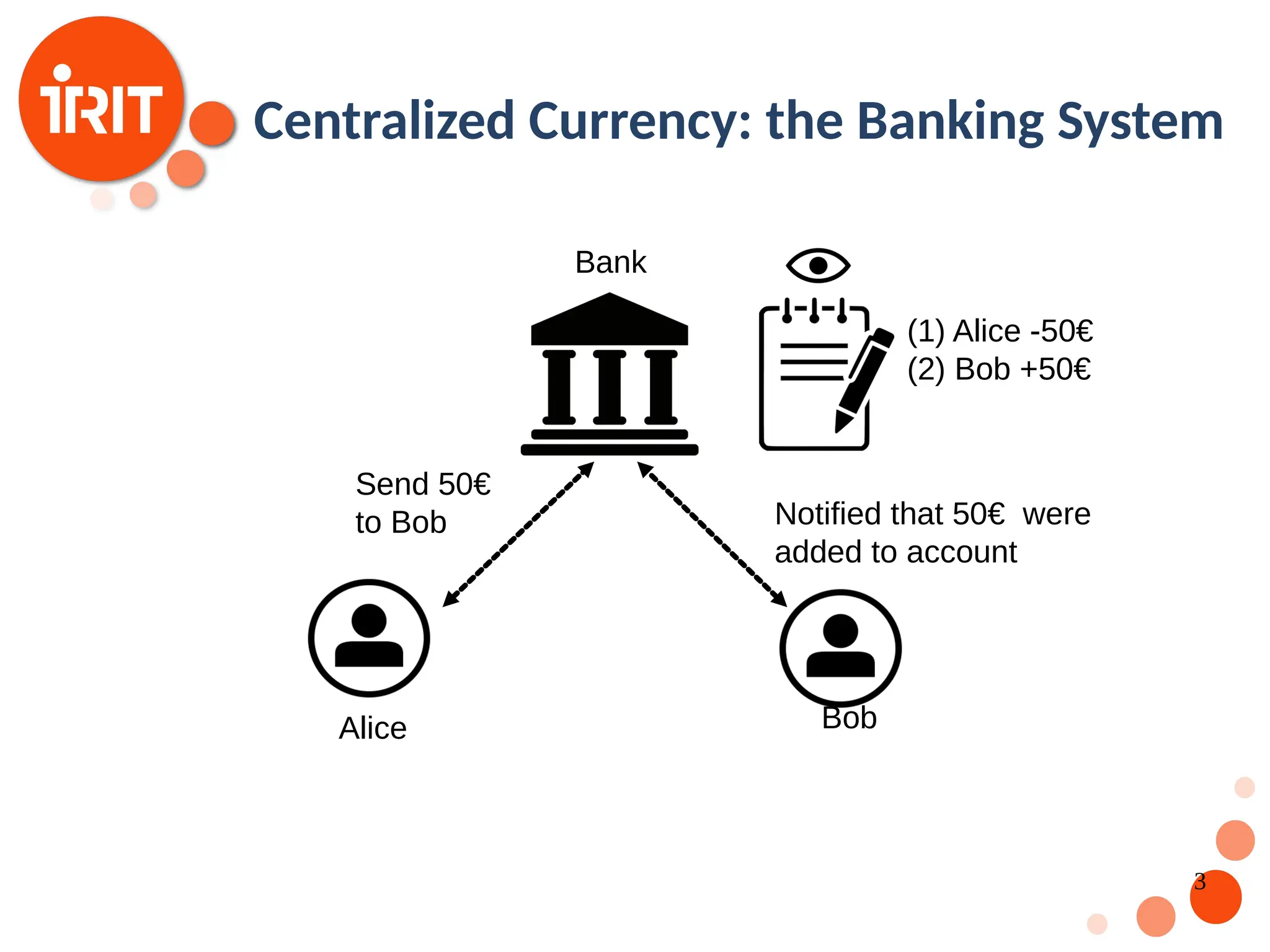
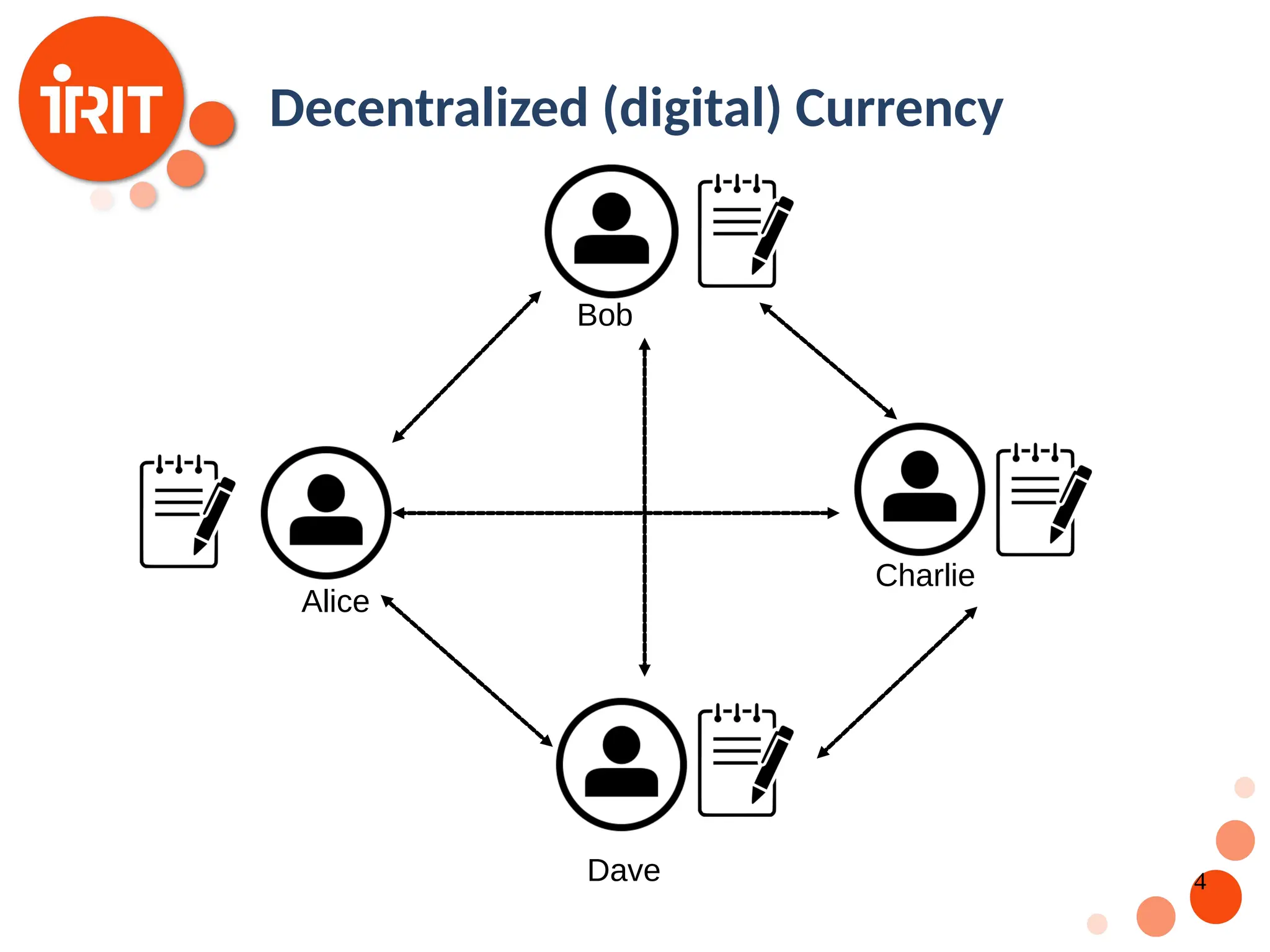


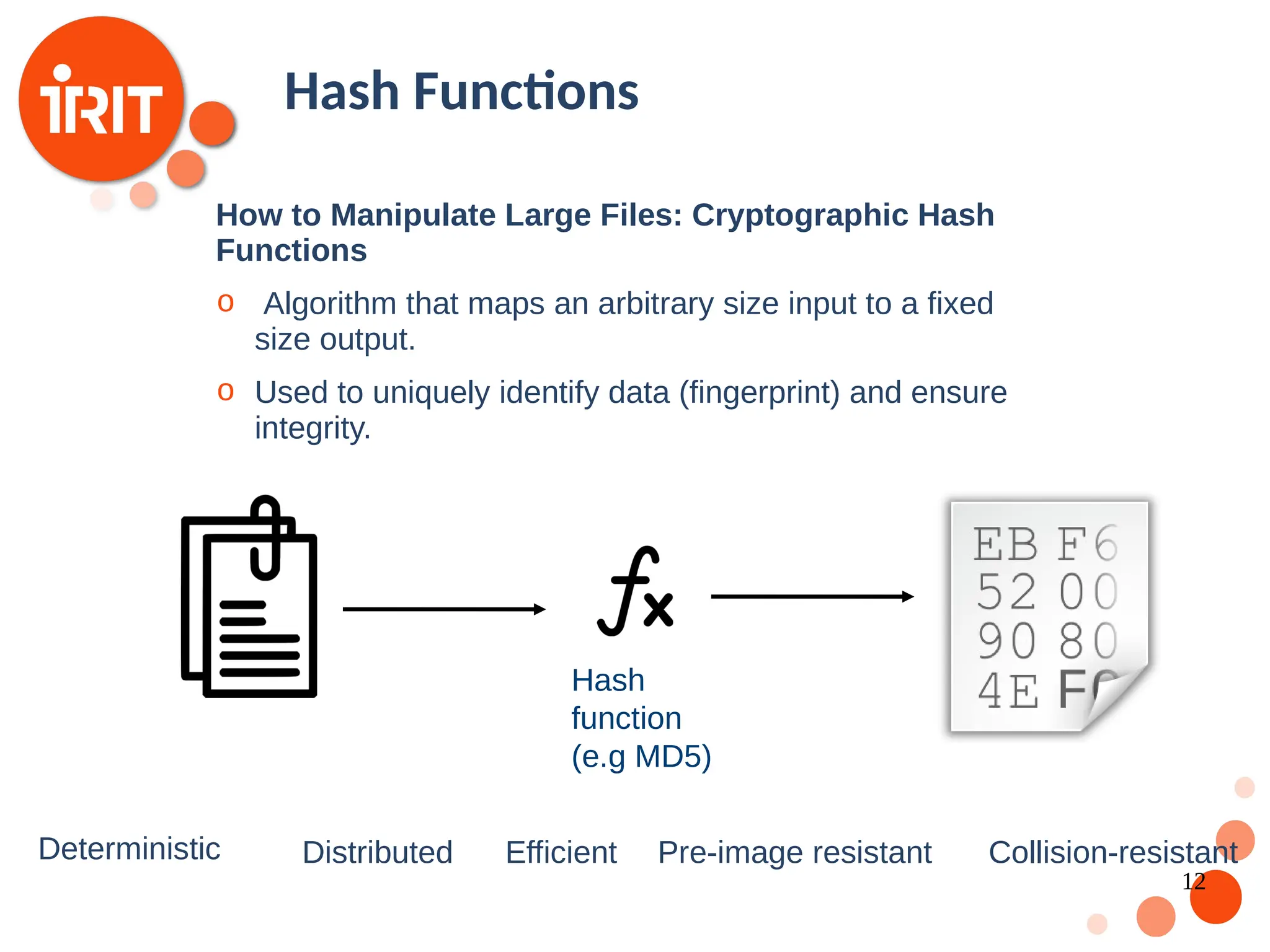
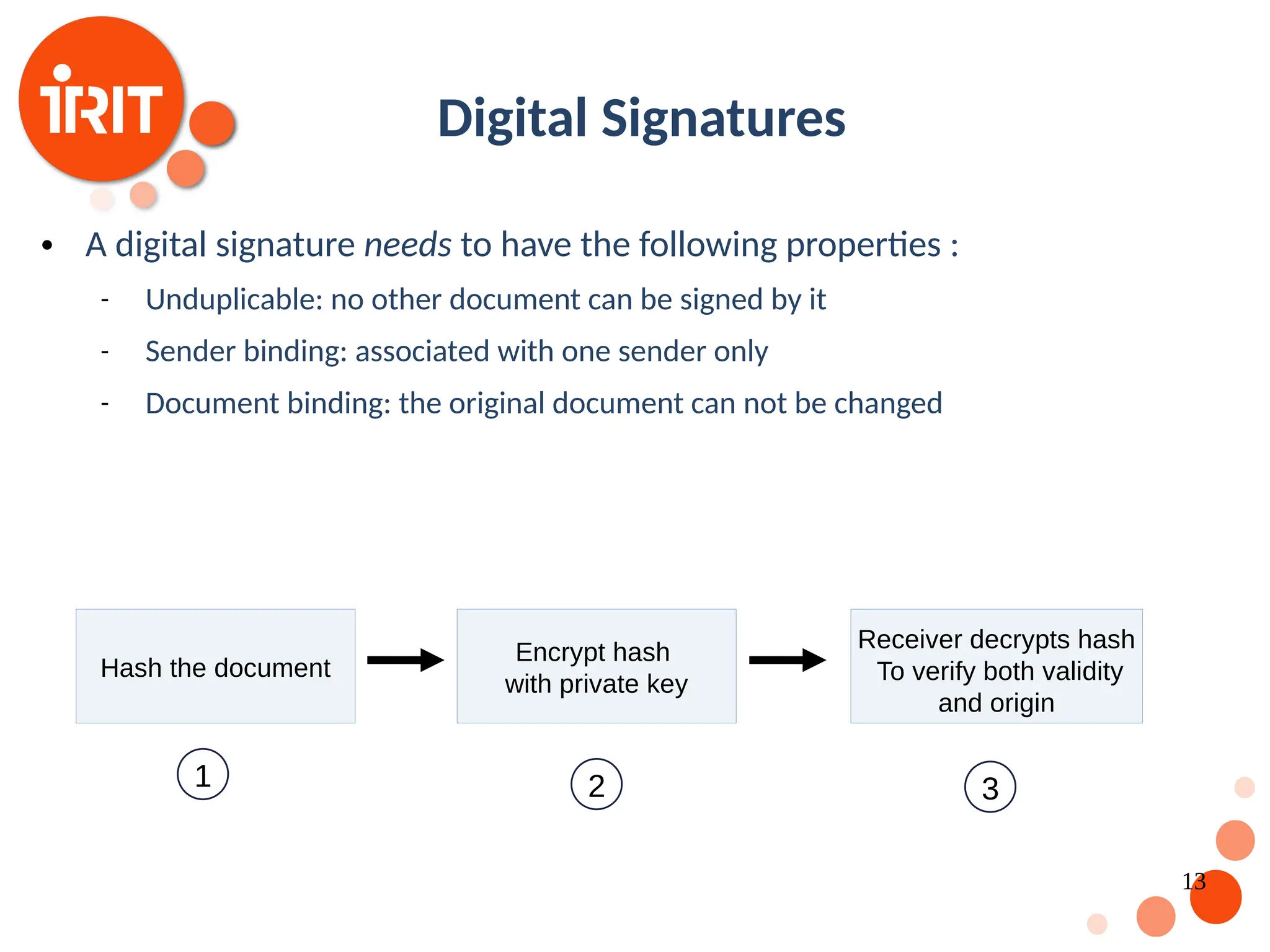
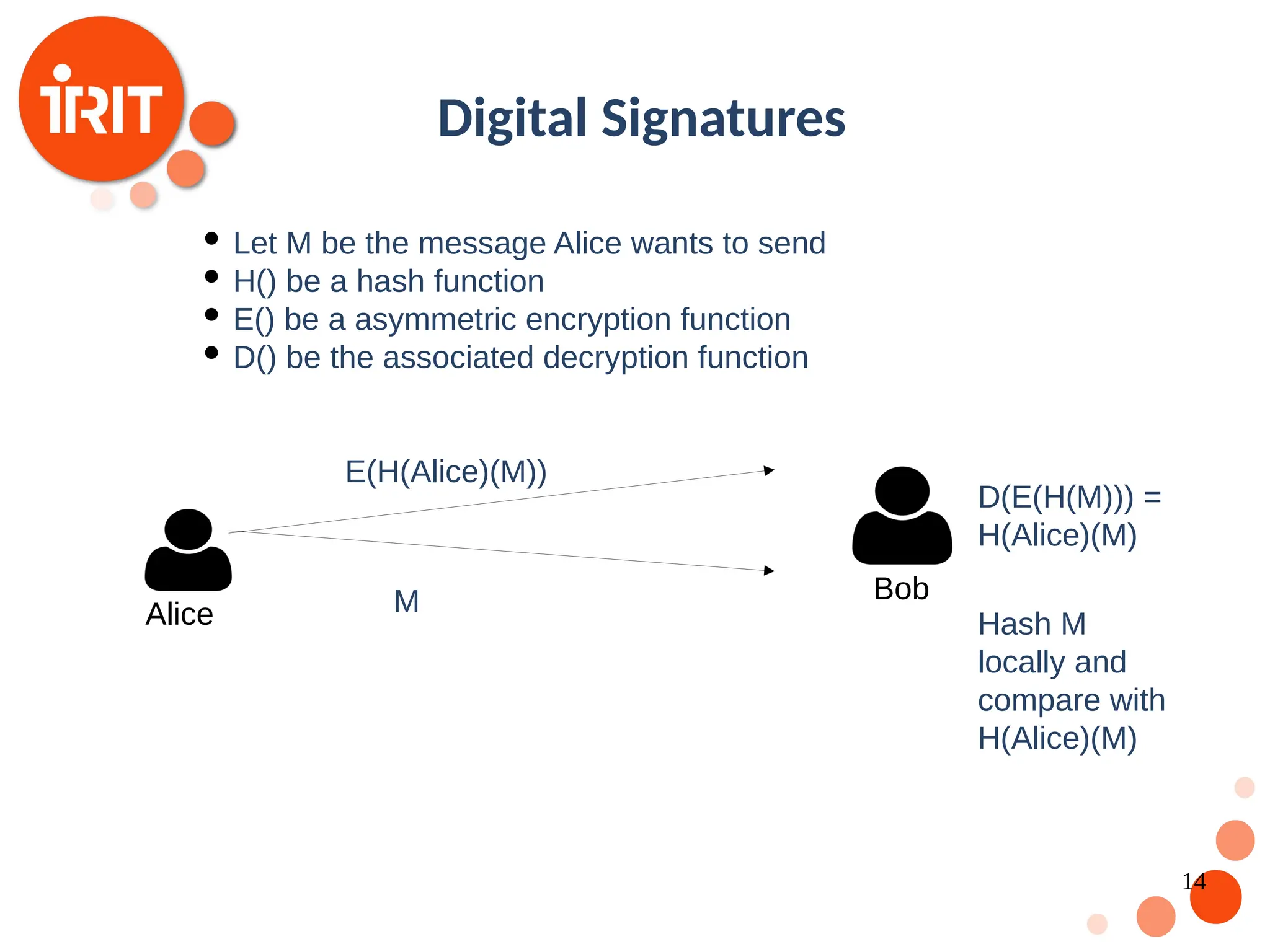
![9 Digital Currencies The idea of a trust-less decentralized currency has been around for decades [Chaum 1989] Motivation: Free of administrative and government control Value based on supply and demand only Challenges: Digital Fingerprint Digital Signatures Consensus](https://image.slidesharecdn.com/2020oer-241207174628-28b962e9/75/Introduction-To-Blockchain-Technology-For-Beginners-9-2048.jpg)

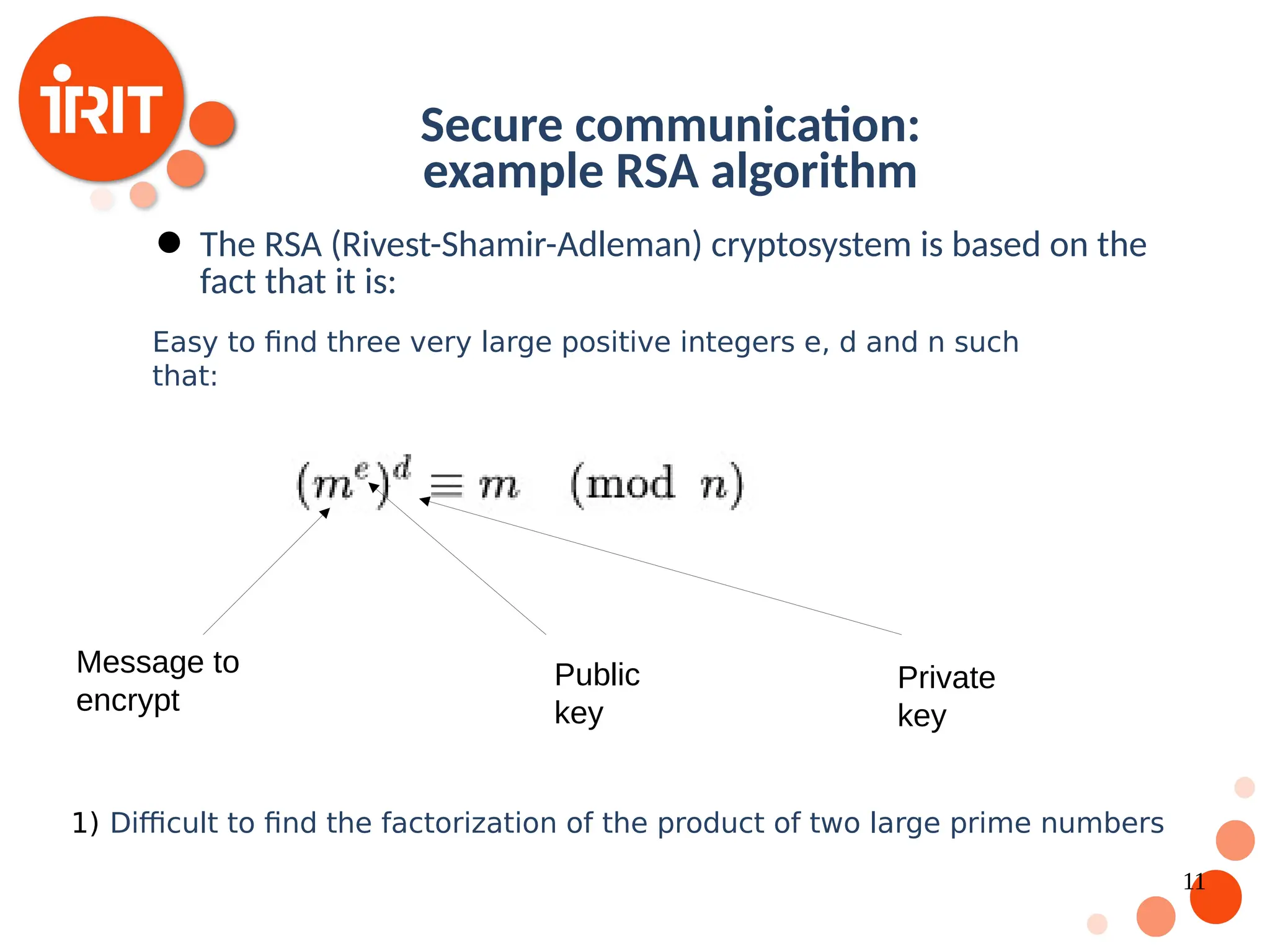


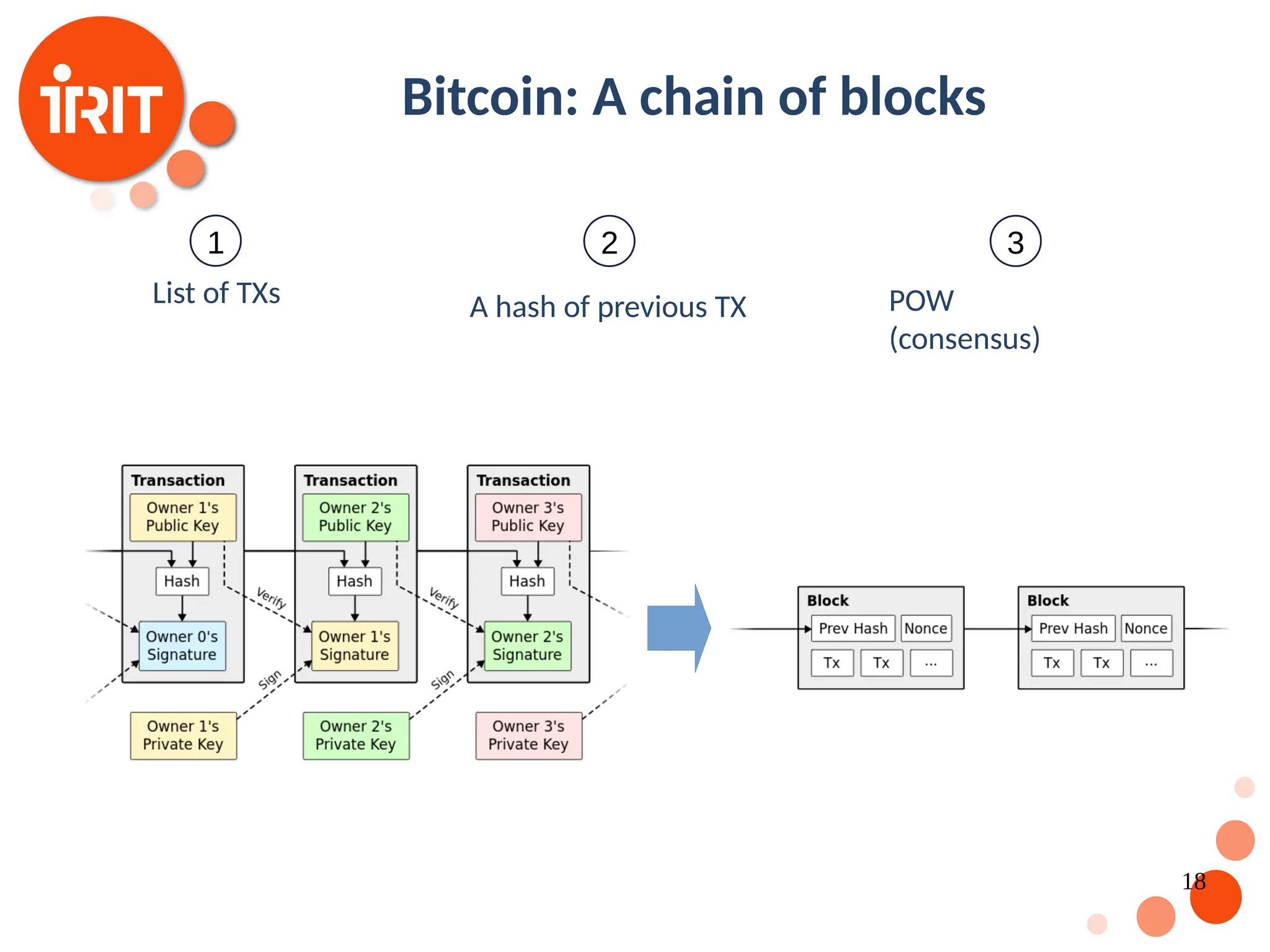
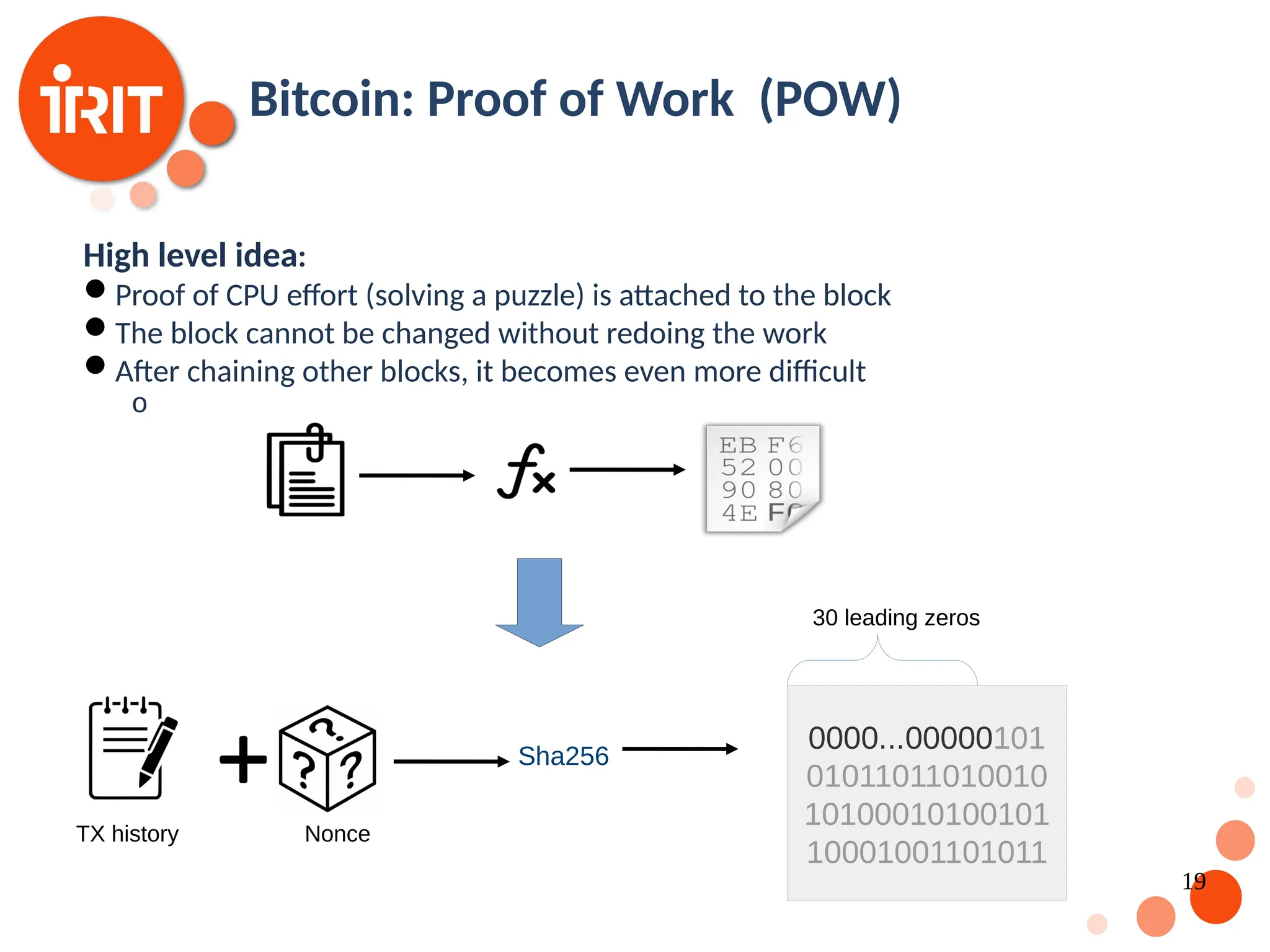
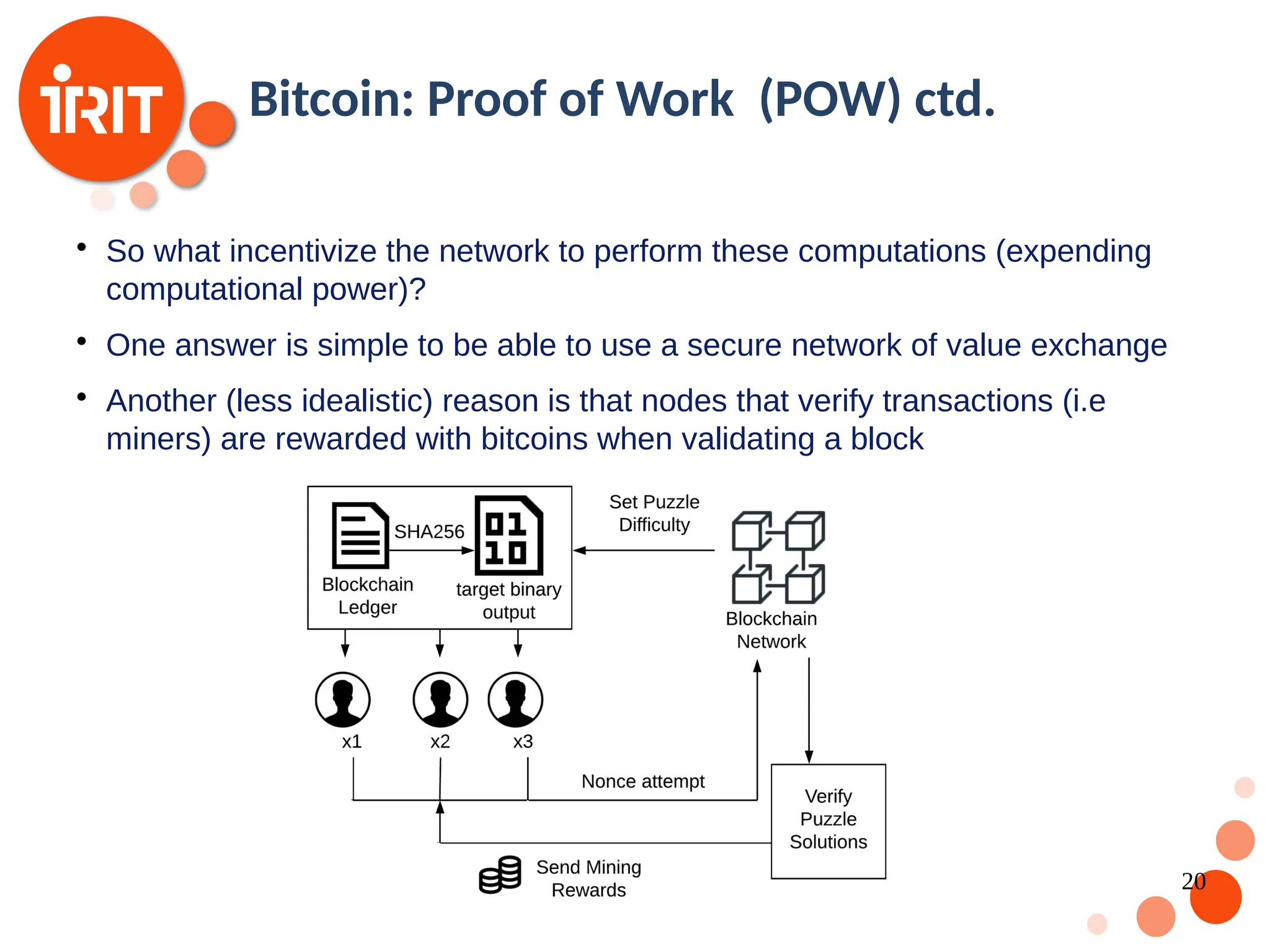
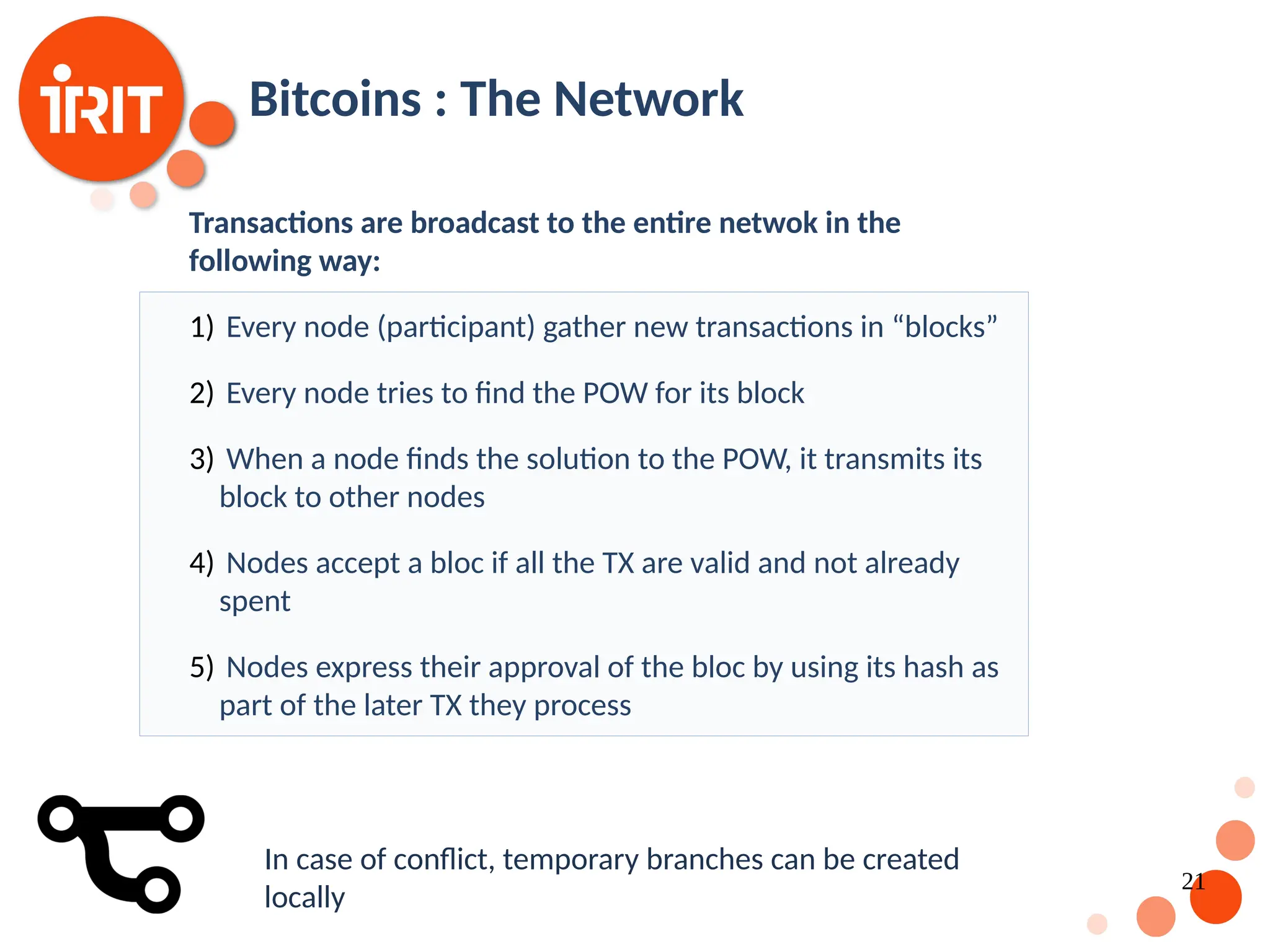
![17 Bitcoin : A first working example Based on established work in cryptography Satoshi Nakamoto published a paper in 2008 [Nakamoto2008] that contributed with the following : A fully functional trustless digital currency system An algorithm which prevents the “double spend” problem. The intuition is that transactions have to be timestamps and trust based on the entire network. Security is guaranteed is the number of honest nodes is larger than the number of malicious nodes](https://image.slidesharecdn.com/2020oer-241207174628-28b962e9/75/Introduction-To-Blockchain-Technology-For-Beginners-17-2048.jpg)



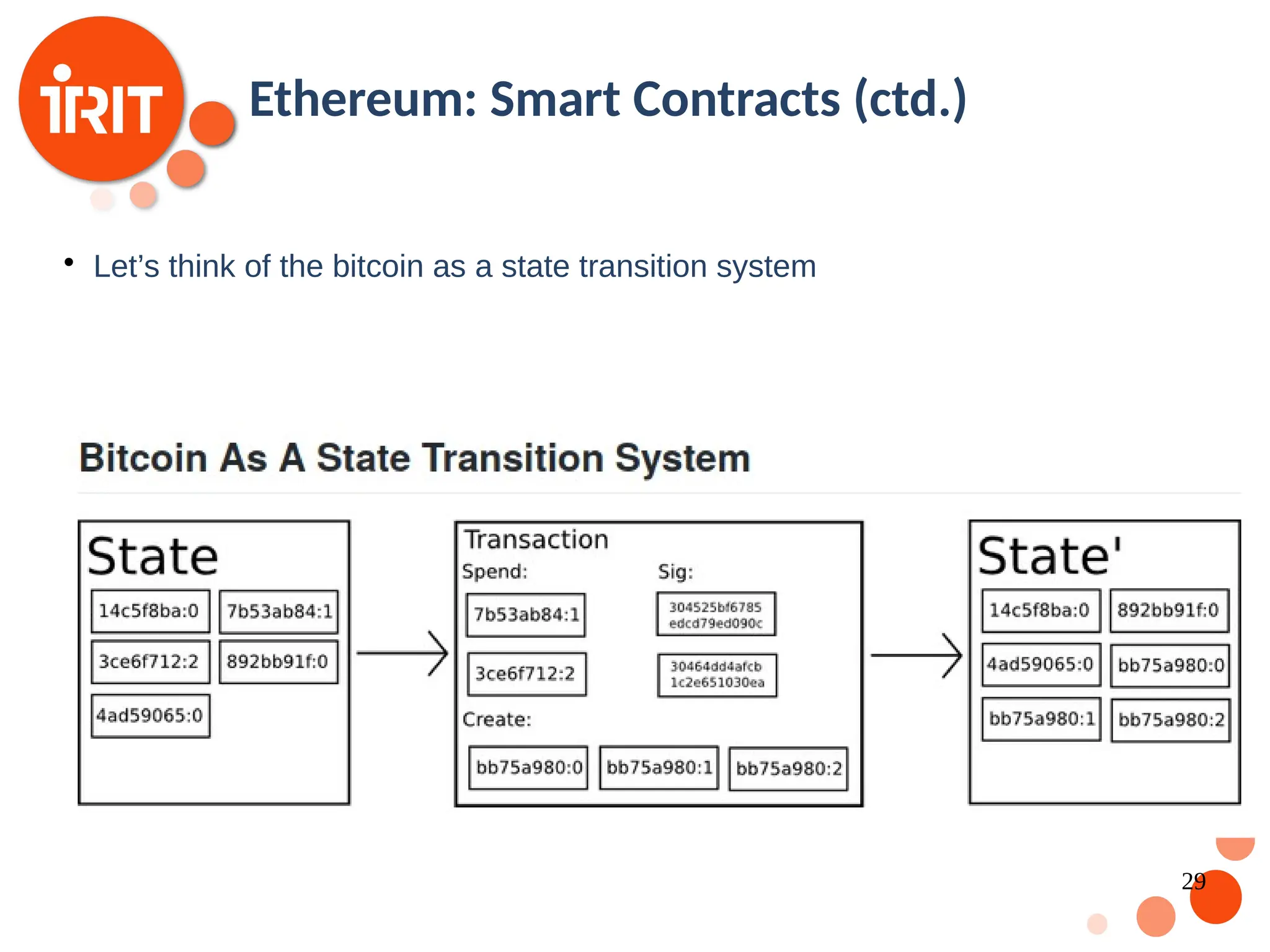
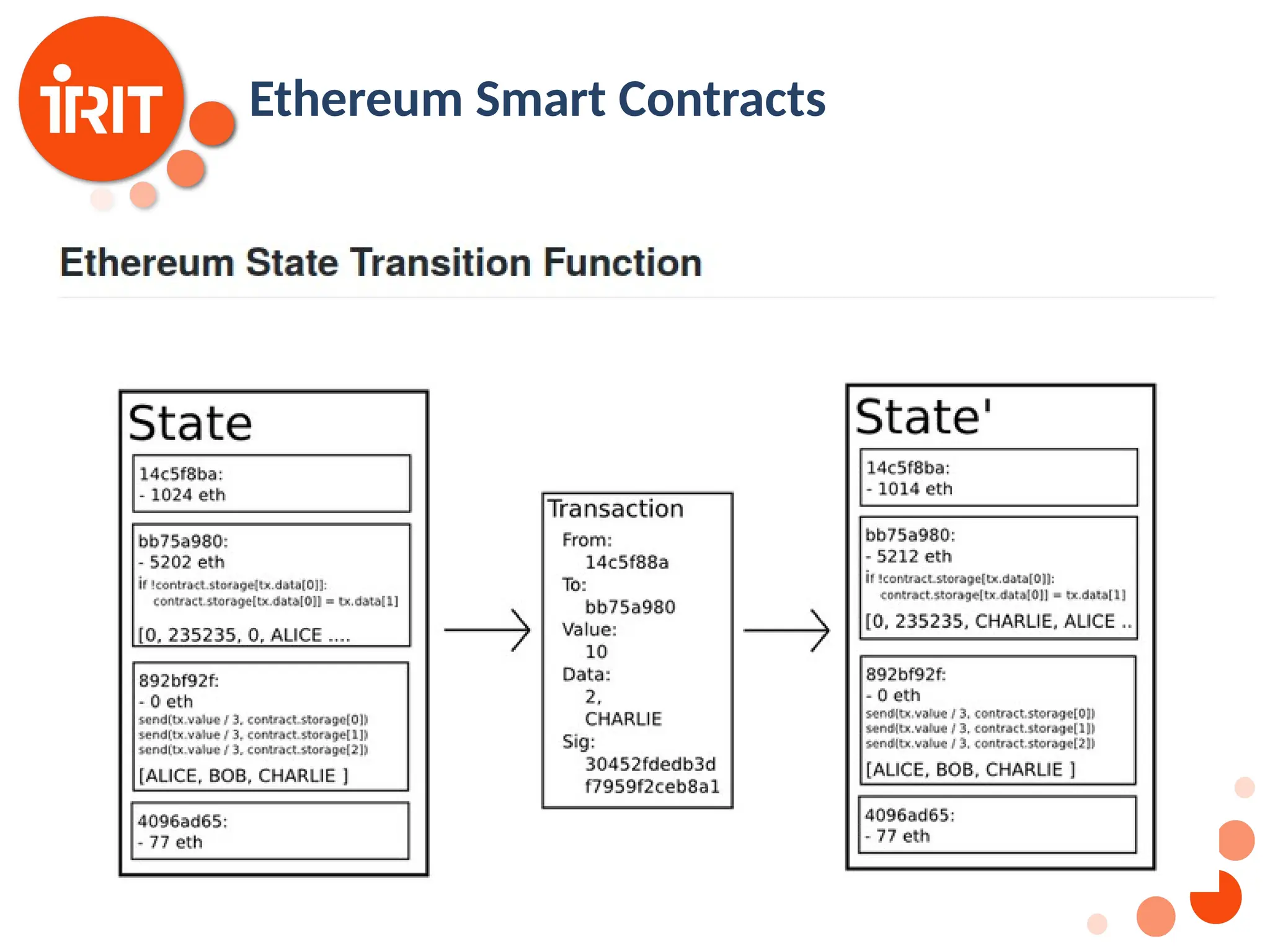
![28 Ethereum: Smart Contracts Bitcoin: Consensus in a network without the need for a trusted third party But consensus is limited to simple transactions More complicated rules such as conditional money transfers or online voting can not be implemented Ethereum: develop the idea further to allow consensus on code [Buterin2014] Bitcoin Ethereum Private keys own simple values (UTXO) All values are owned by a private key Private keys own Accounts There are externally owned accounts and internal accounts (can not be called directly)](https://image.slidesharecdn.com/2020oer-241207174628-28b962e9/75/Introduction-To-Blockchain-Technology-For-Beginners-28-2048.jpg)



![48 [Chaum1988] Chaum, David, Amos Fiat, and Moni Naor. "Untraceable electronic cash." Conference on the Theory and Application of Cryptography. Springer, New York, NY, 1988. [Nakamoto2008] Nakamoto, Satoshi. Bitcoin: A peer-to-peer electronic cash system. Manubot, 2019. [Buterin2014] Buterin, Vitalik. "A next-generation smart contract and decentralized application platform." white paper 3.37 (2014). [Casino2019] Casino, Fran, Thomas K. Dasaklis, and Constantinos Patsakis. "A systematic literature review of blockchain-based applications: current status, classification and open issues." Telematics and Informatics 36 (2019): 55-81 [Fan et al., 2018] Fan, K., Wang, S., Ren, Y., Li, H., and Yang, Y. (2018). MedBlock:Efficient and Secure Medical Data Sharing Via Blockchain. Journal of Medical Systems, 42(8):1–11. References](https://image.slidesharecdn.com/2020oer-241207174628-28b962e9/75/Introduction-To-Blockchain-Technology-For-Beginners-48-2048.jpg)
![49 [Liu et al., 2018] Liu, J., Li, X., Ye, L., Zhang, H., Du, X., and Guizani, M. (2018).BPDS: A Blockchain Based Privacy-Preserving Data Sharing for Electronic Medical Records. 2018 IEEE Global Communications Conference, GLOBECOM 2018 Proceedings [Xia et al., 2017] Xia, Q., Sifah, E. B., Asamoah, K. O., Gao, J., Du, X., and Guizani, M. (2017). MeDShare: Trust-Less Medical Data Sharing among Cloud Service Providers via Blockchain. IEEE Access, 5:14757–14767. [Zhang et al., 2018] Zhang, P., White, J., Schmidt, D. C., Lenz, G., and Rosenbloom,S. T. (2018). FHIRChain: Applying Blockchain to Securely and Scalably Share Clinical Data.Computational and Structural Biotechnology Journal, 16:267– 278. [Zyskind et al., 2015] Zyskind, G., Nathan, O., and Pentland, A. S. (2015). Decentralizing privacy: Using blockchain to protect personal data. In Proceedings - 2015 IEEE Security and Privacy Workshops, SPW 2015, pages 180–184 References (ctd.)](https://image.slidesharecdn.com/2020oer-241207174628-28b962e9/75/Introduction-To-Blockchain-Technology-For-Beginners-49-2048.jpg)