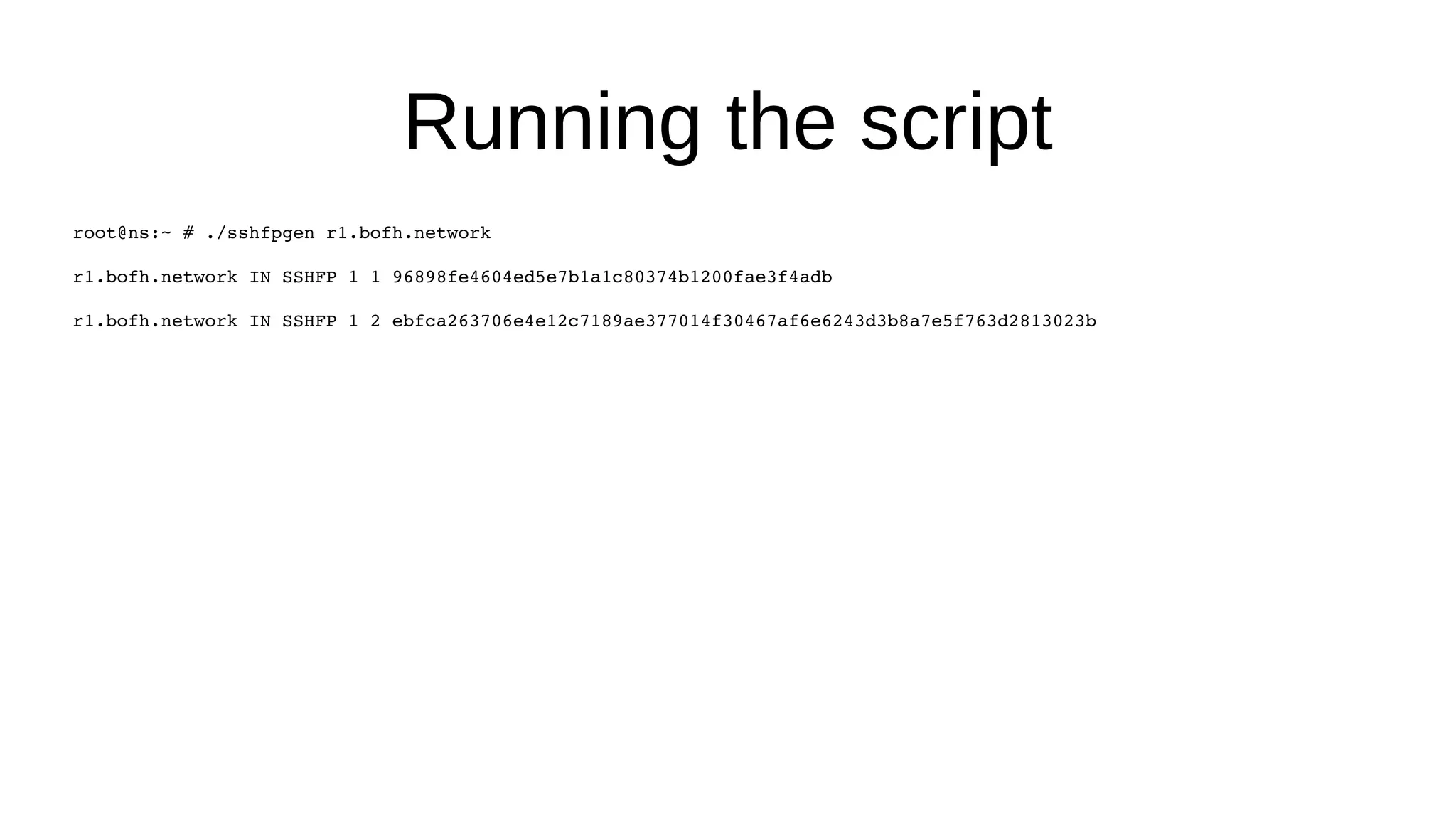
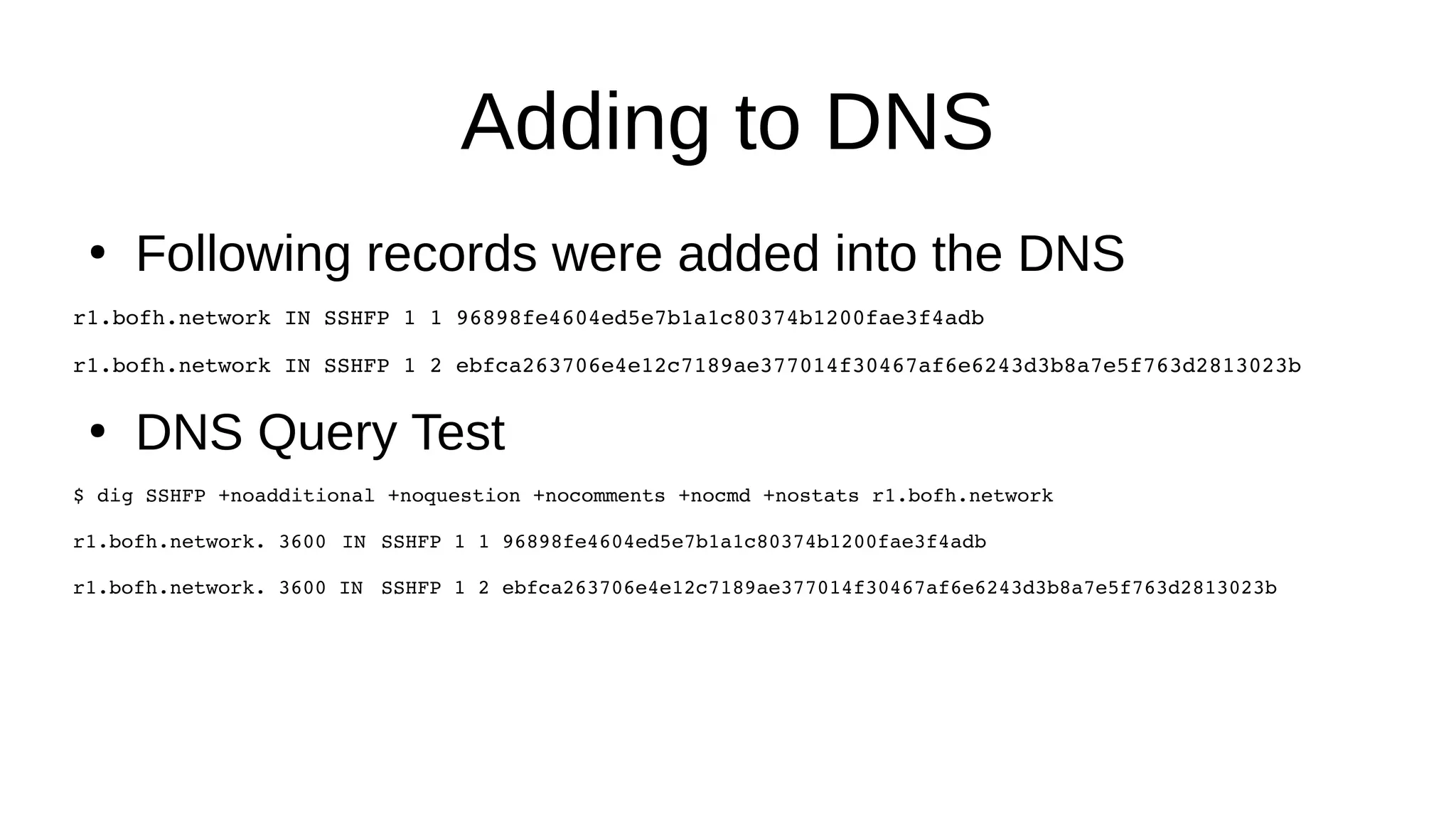
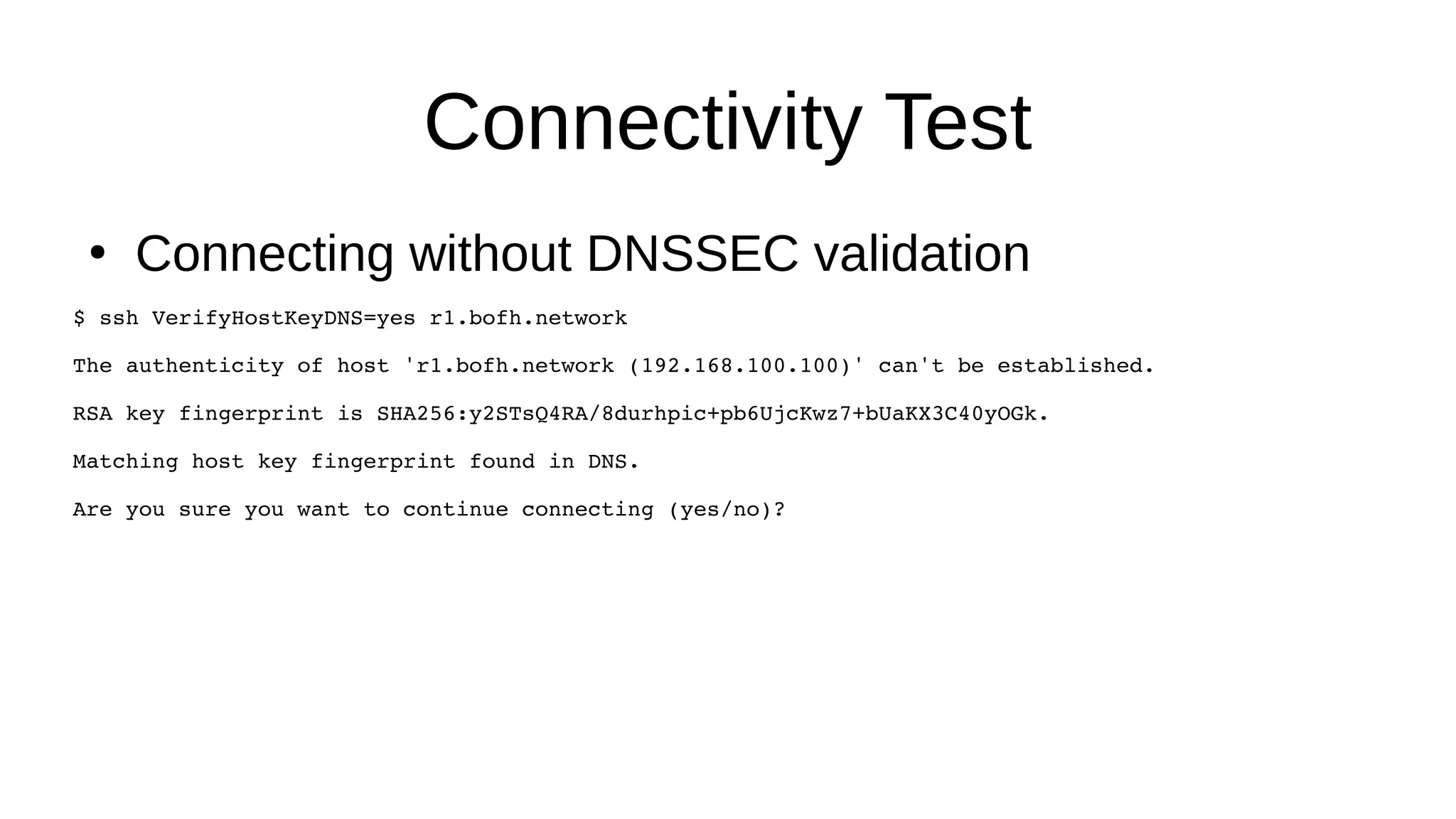
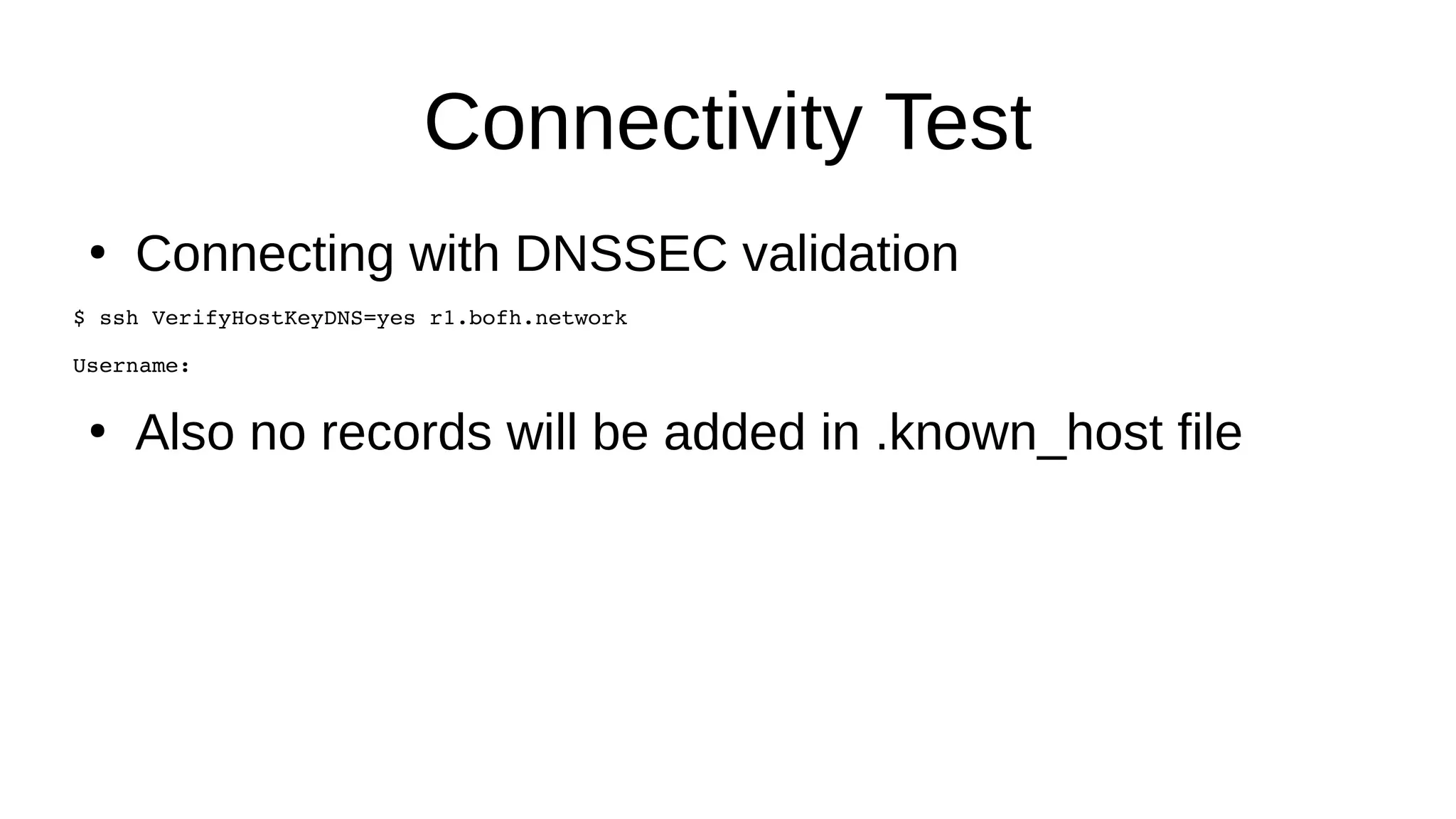
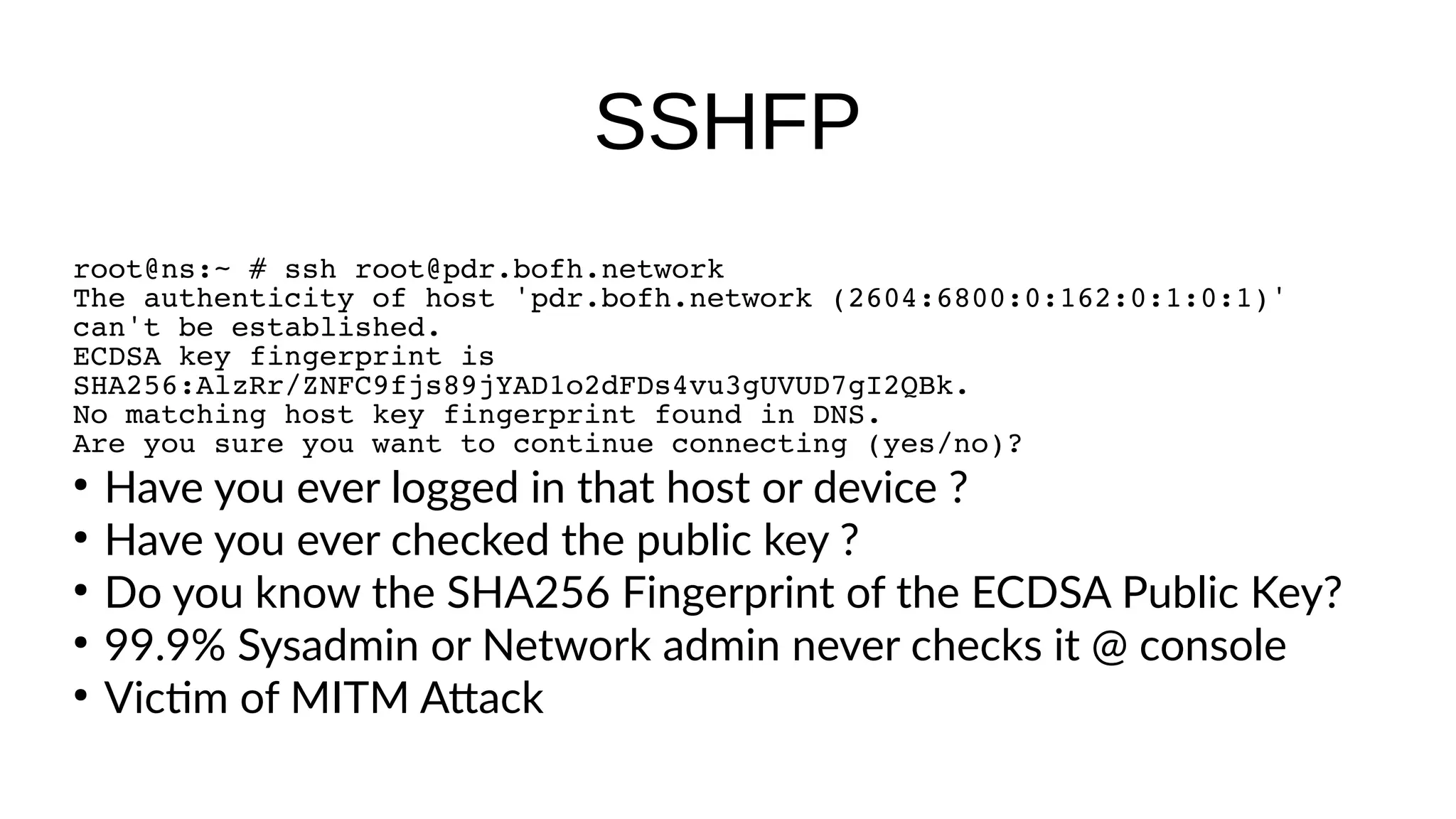
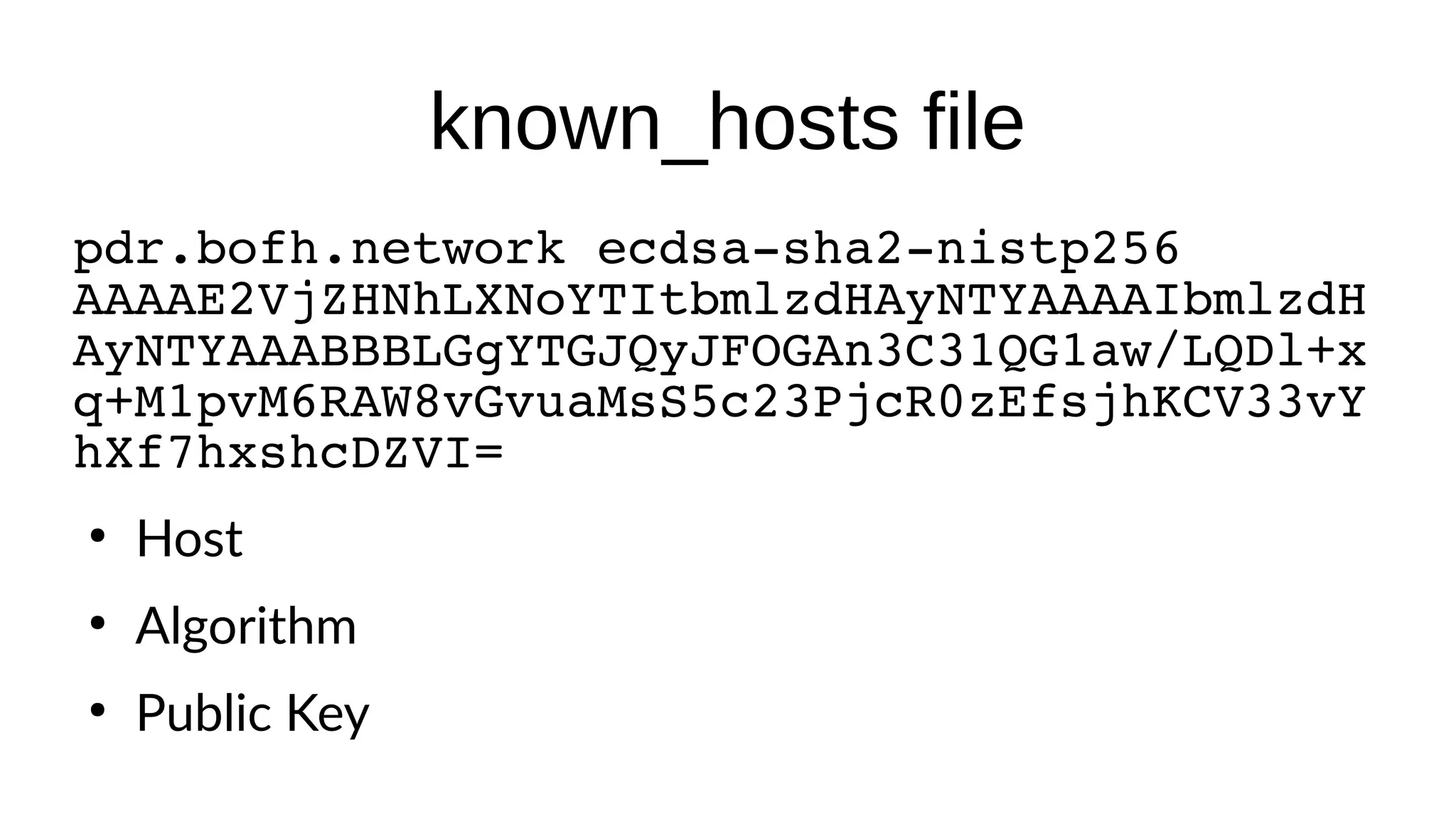
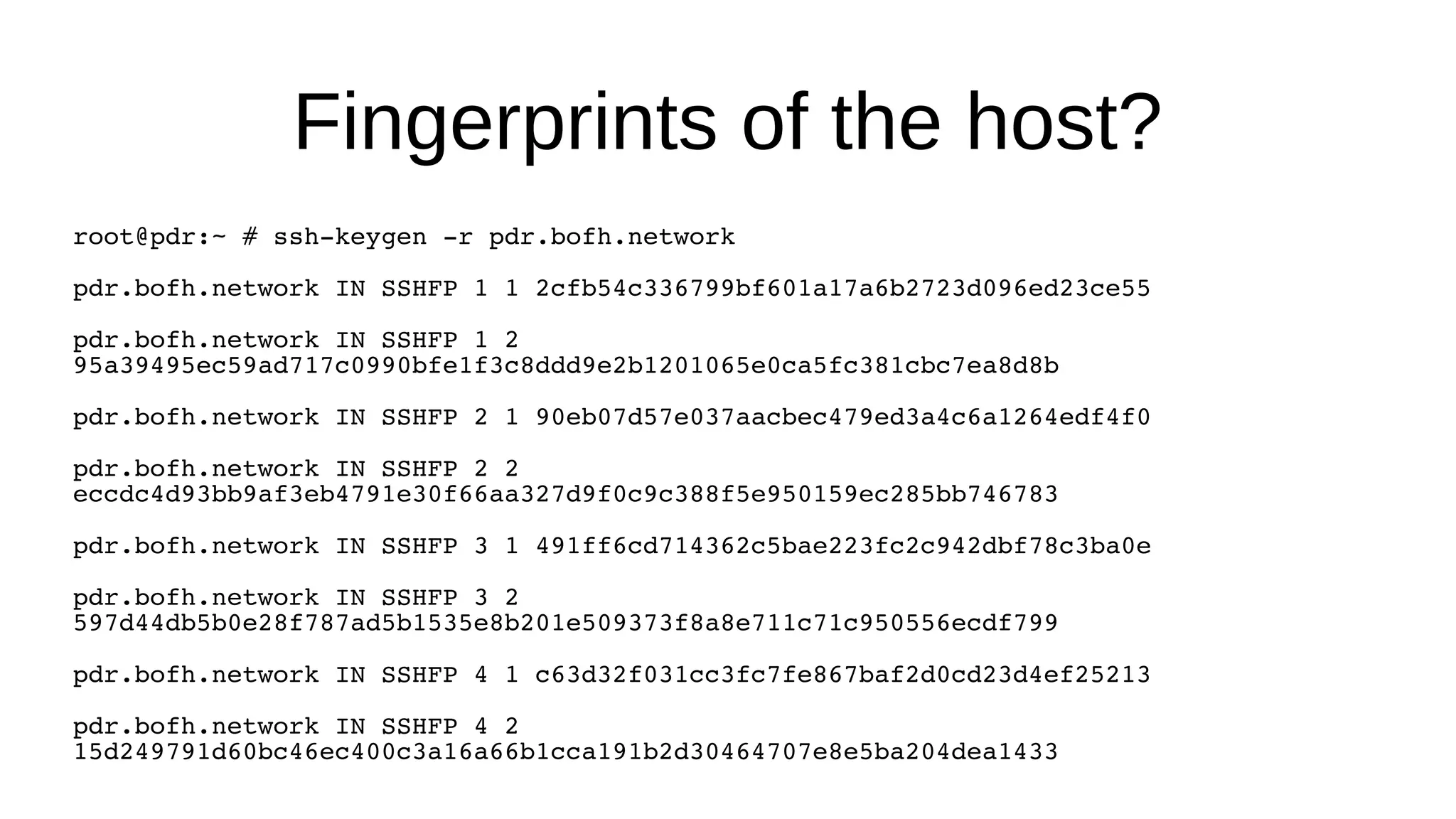
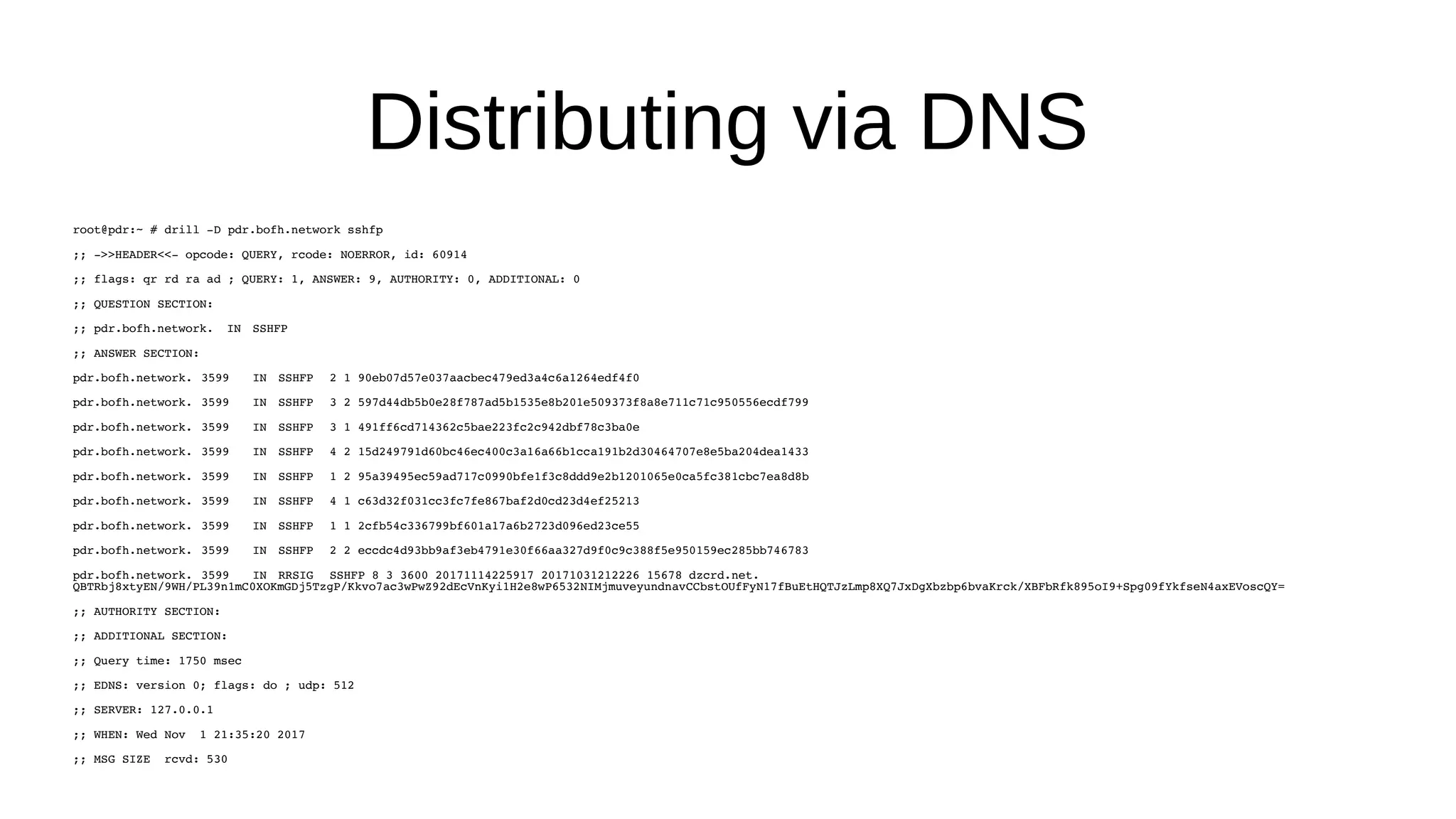
SSHFP records provide a secure method of distributing host public keys via DNS. The document discusses: 1) How SSHFP records store fingerprints of host public keys in DNS to validate connections, rather than distributing keys directly. 2) The process of generating fingerprints from router public keys, creating SSHFP records, and configuring DNS to distribute them securely via DNSSEC. 3) How an SSH client can validate connections to a host by looking up its SSHFP records and fingerprints in DNS, preventing man-in-the-middle attacks.








![If ldns is supported .. ● Need to maintain a trust-anchor ● Run unbound-anchor ● Add to /etc/resolv.conf anchor /etc/unbound/root.key [*BSD] anchor /var/lib/unbound/root.key [Linux]](https://image.slidesharecdn.com/importanceofsshfpandconfiguringsshfpfornetworkdevices-190324211322/75/Importance-of-sshfp-and-configuring-sshfp-for-network-devices-13-2048.jpg)




![Using the script #!/usr/local/bin/bash HOST="${1}" if [[ "$1" == "-h" || "$1" == "--help" ]] then echo "Usage: sshfpgen <hostname>" fi for pubkey in *_key.pub do echo "$HOST IN SSHFP 1 1 $(cut -f2 -d ' ' "$pubkey" | base64 --decode | shasum | cut -f 1 -d ' ')" echo "$HOST IN SSHFP 1 2 $(cut -f2 -d ' ' "$pubkey" | base64 --decode | shasum -a 256 | cut -f 1 -d ' ')" done](https://image.slidesharecdn.com/importanceofsshfpandconfiguringsshfpfornetworkdevices-190324211322/75/Importance-of-sshfp-and-configuring-sshfp-for-network-devices-21-2048.jpg)