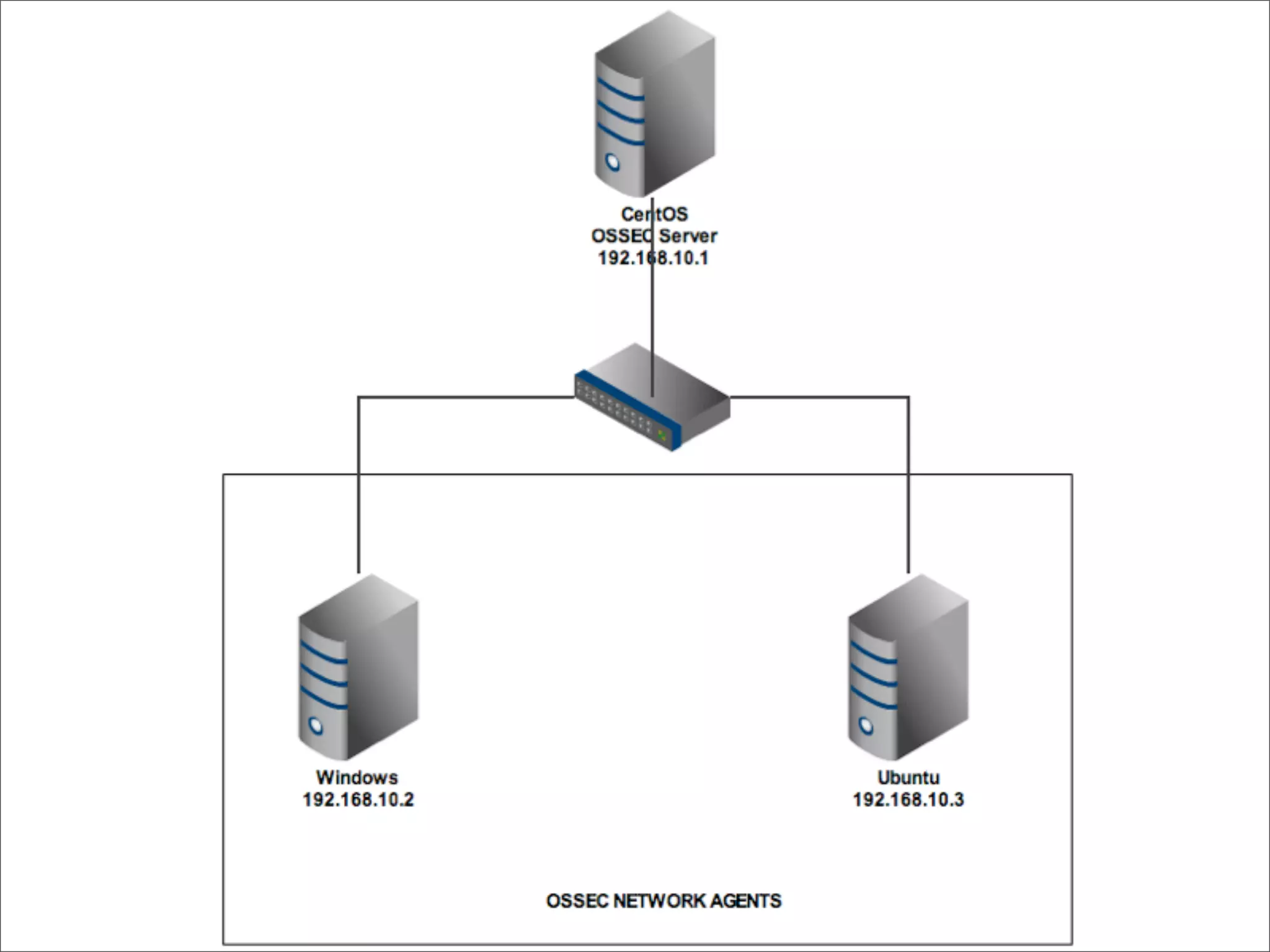
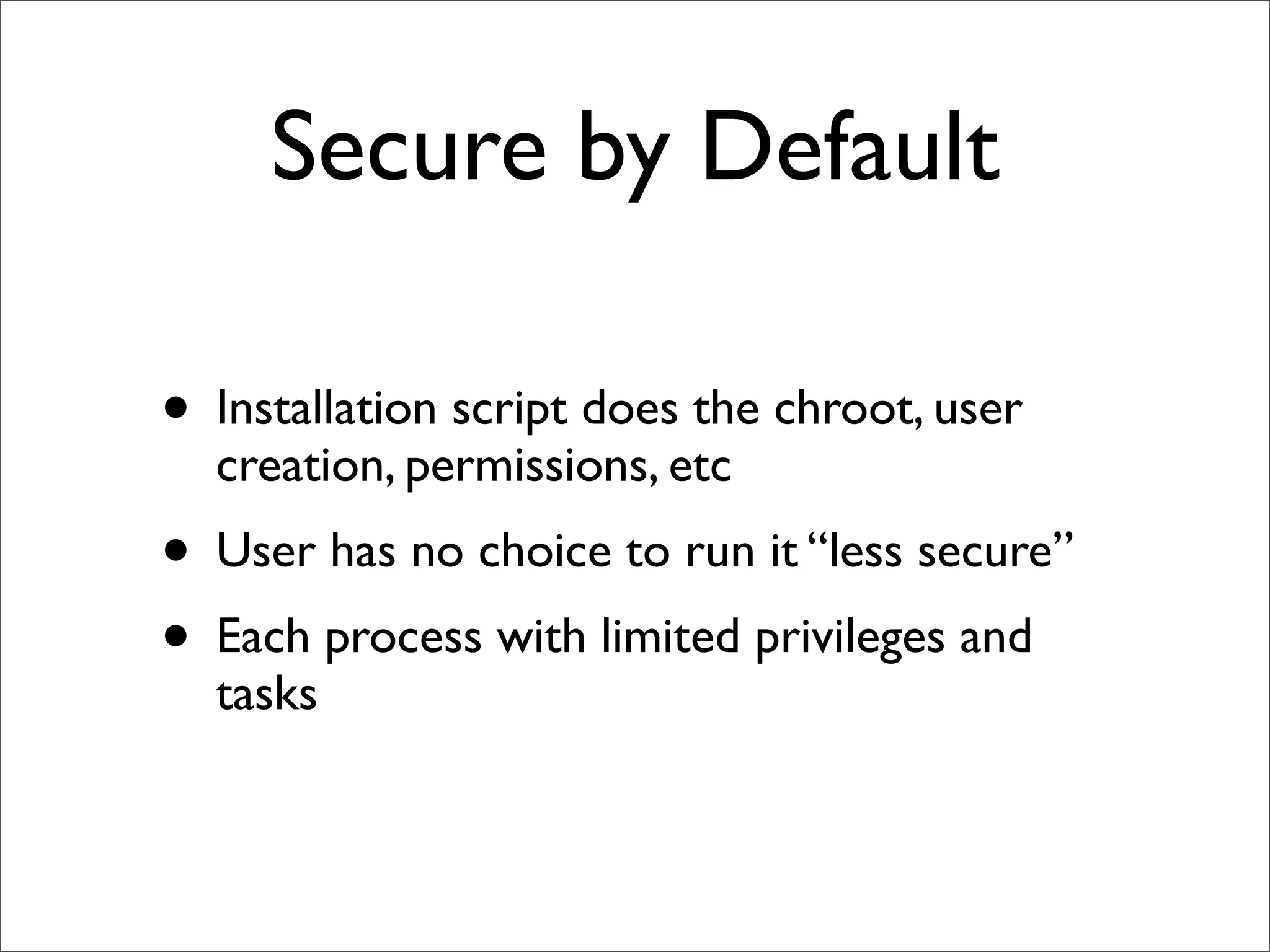
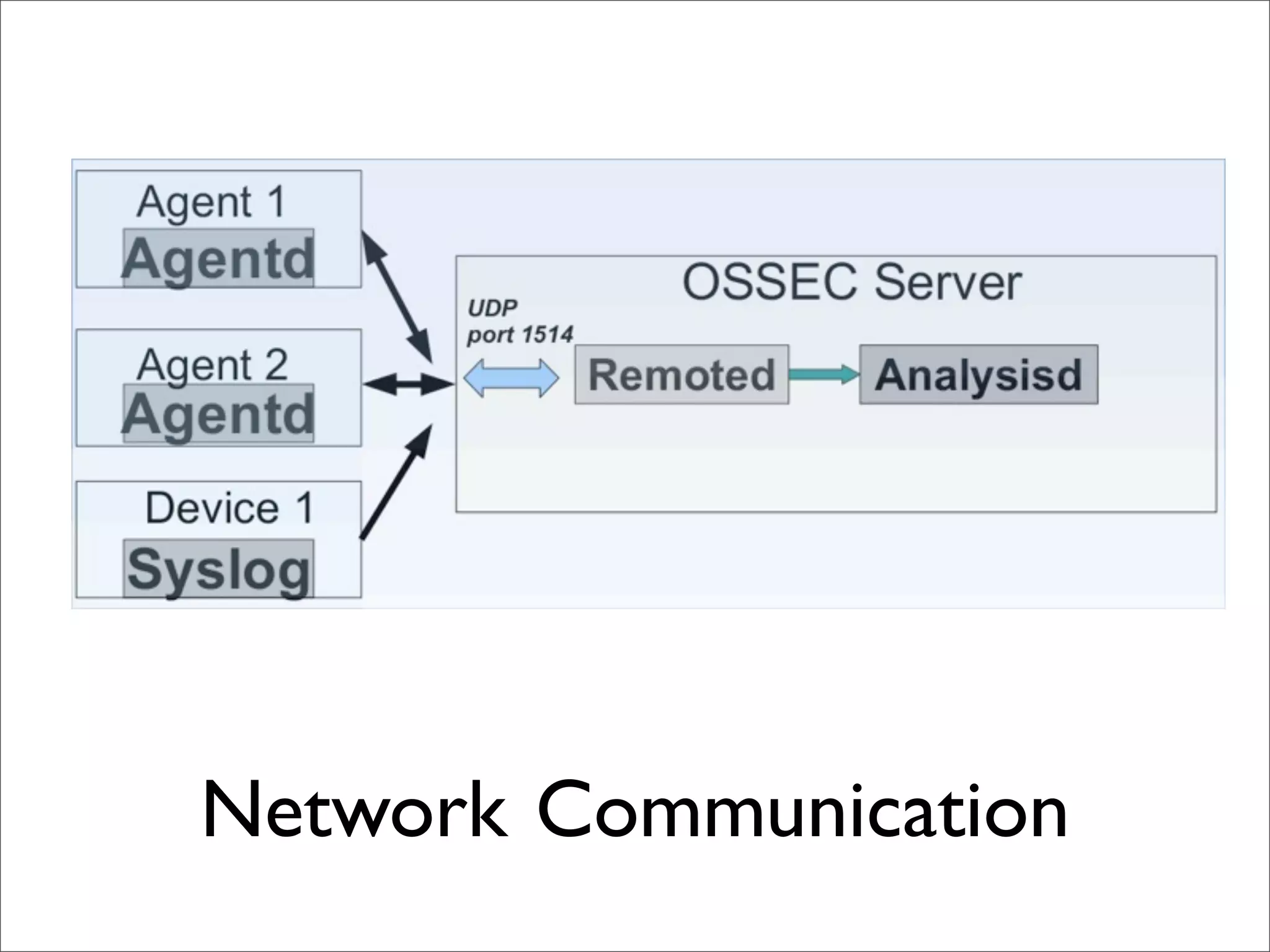
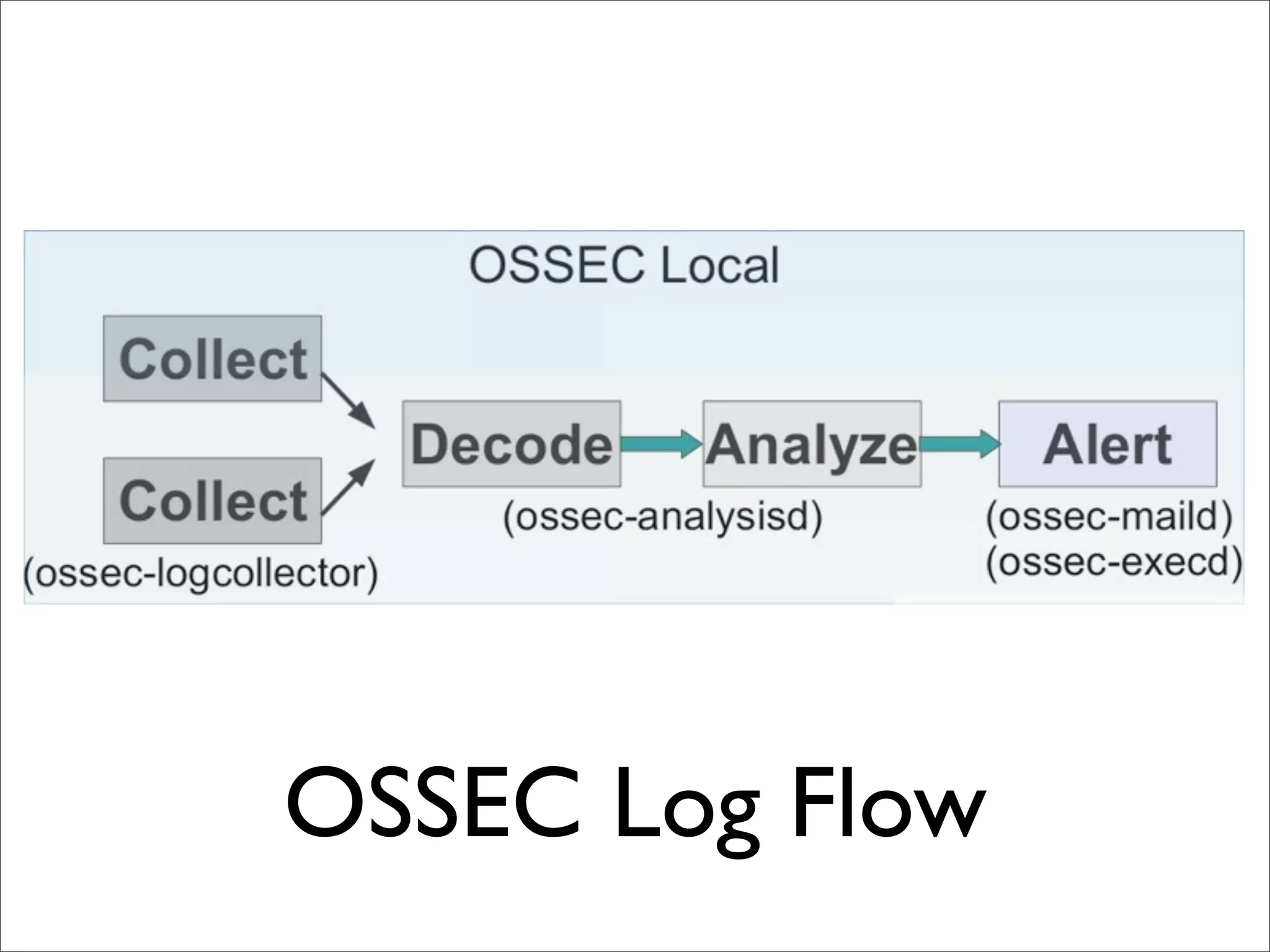
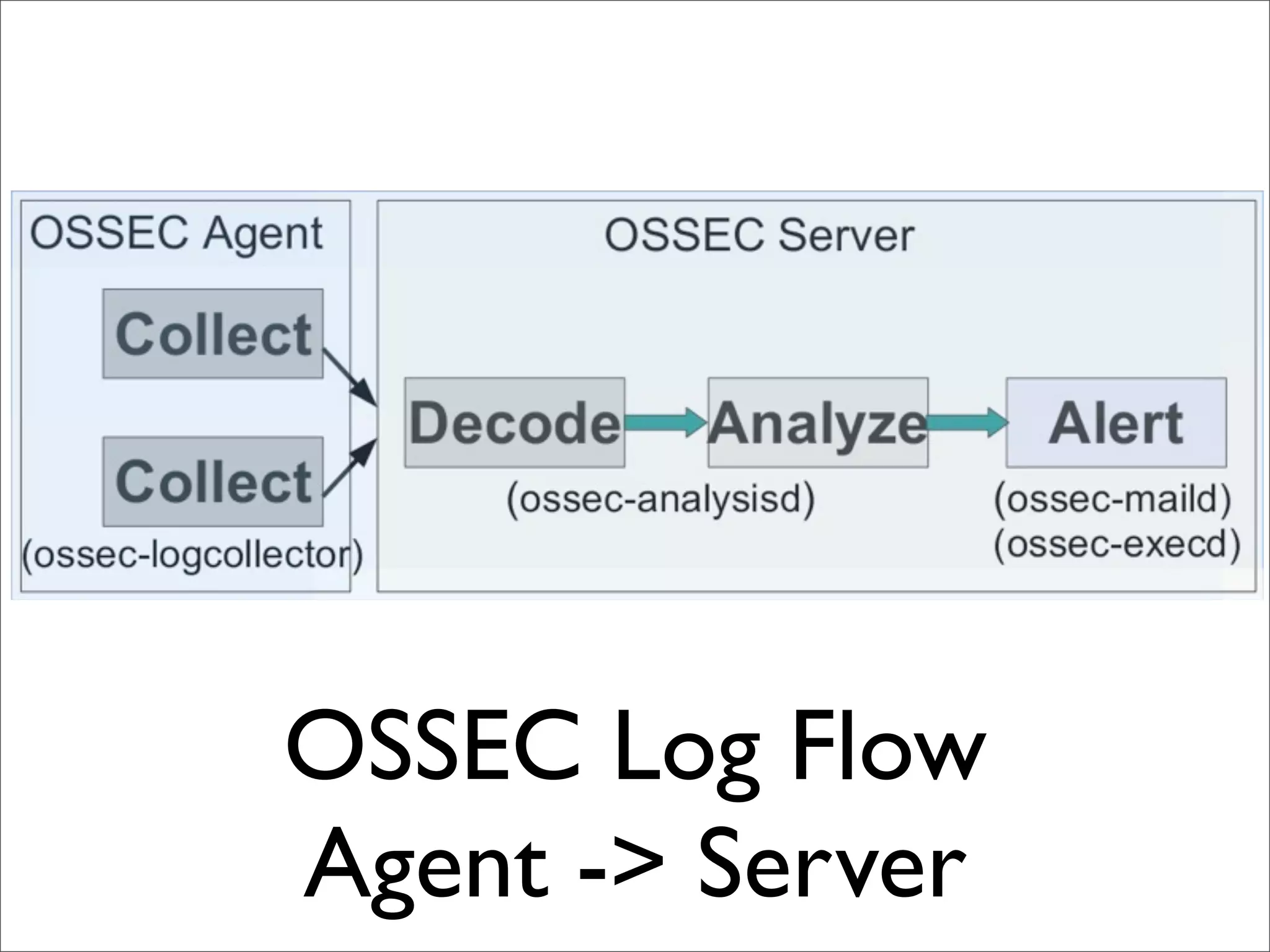
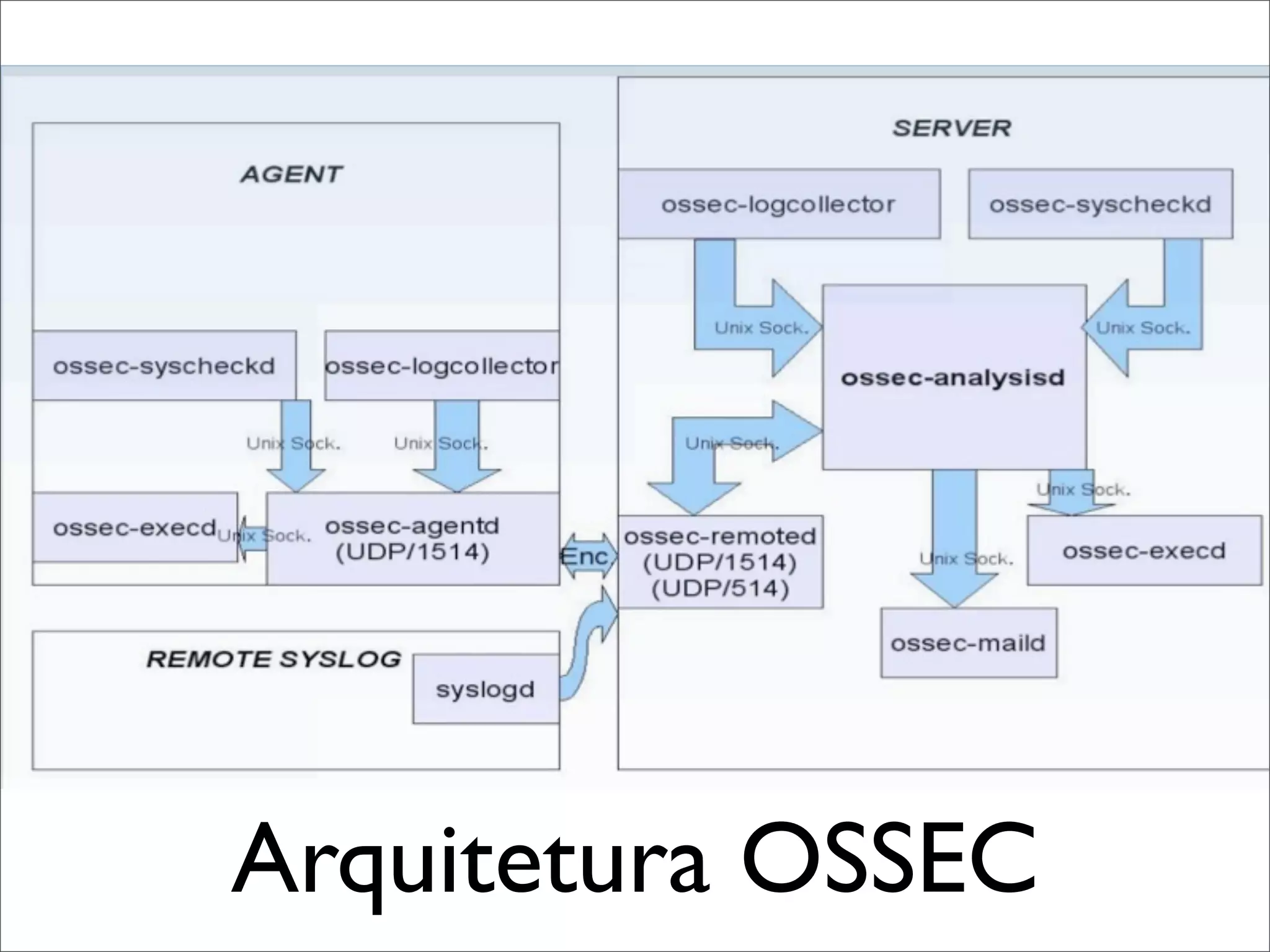
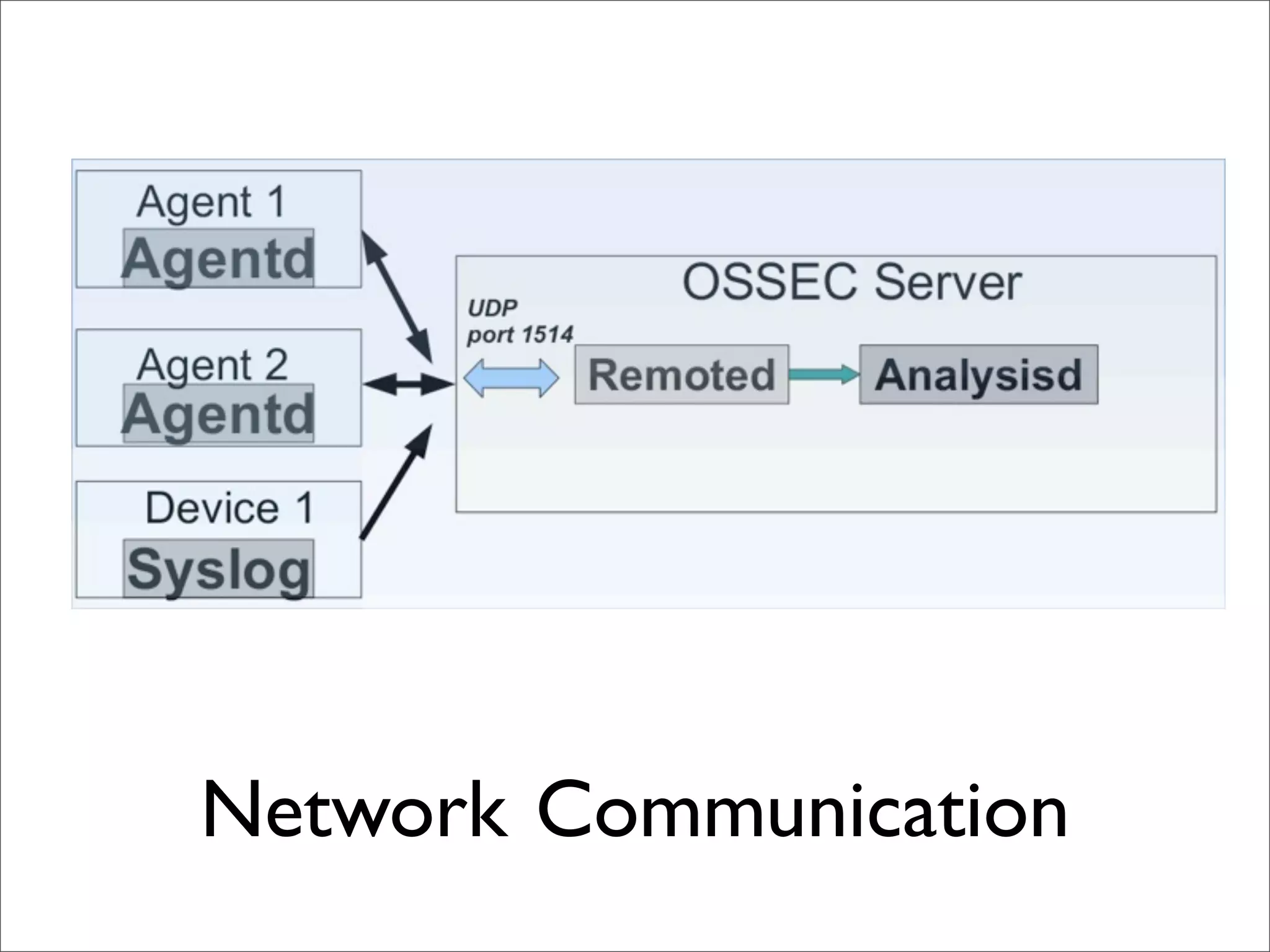
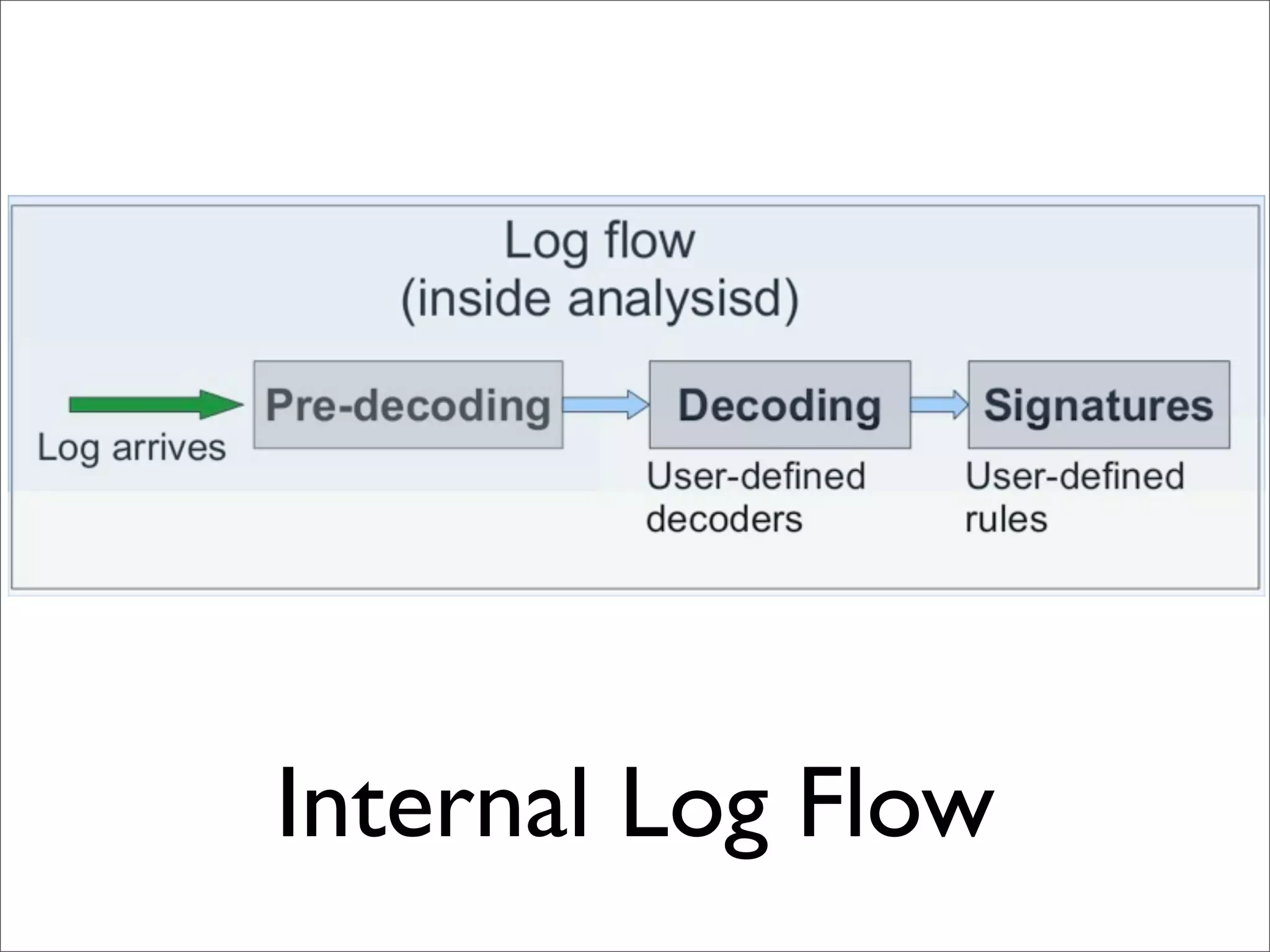
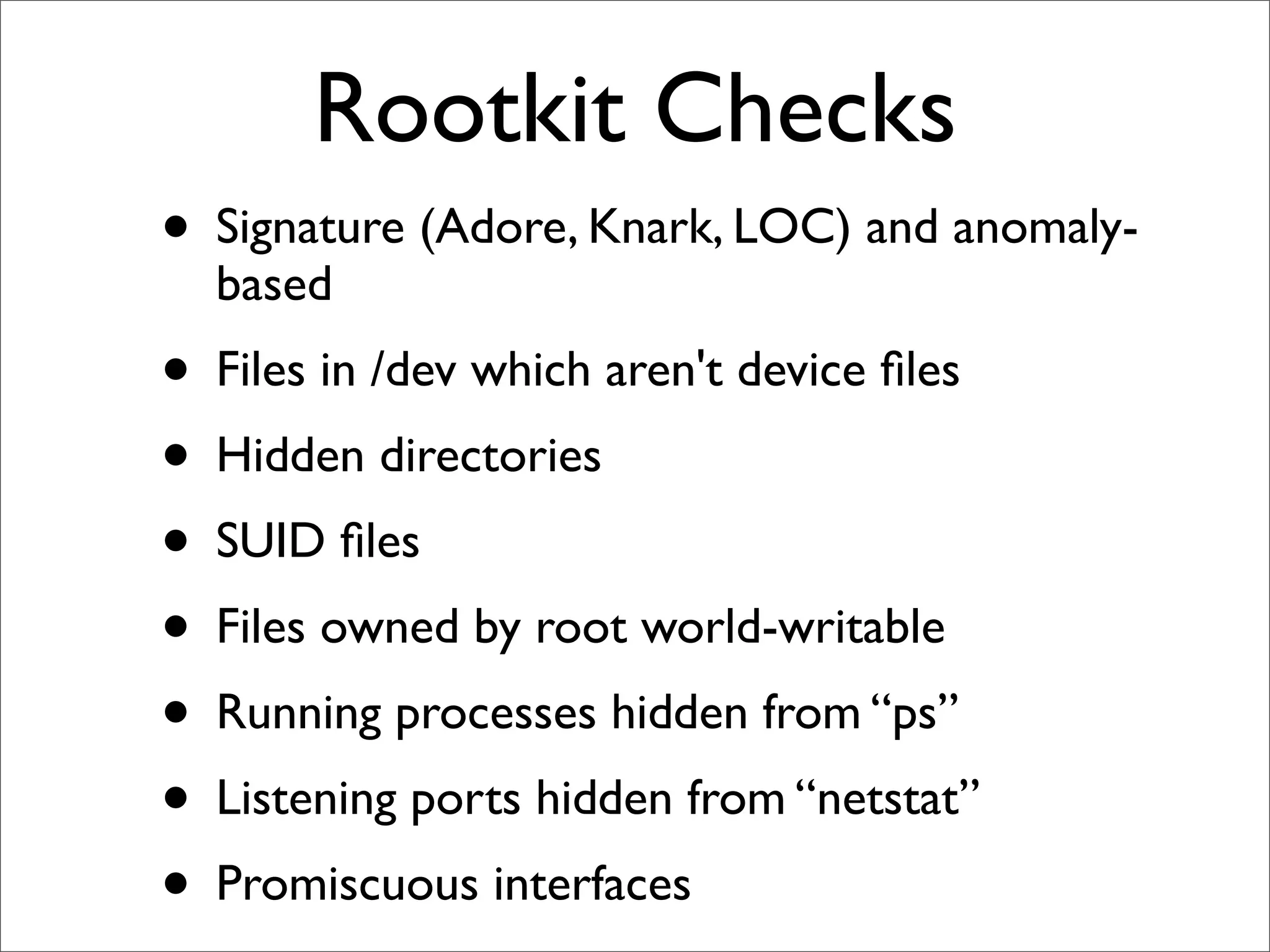
This document provides an overview of implementing the OSSEC HIDS (Host-based Intrusion Detection System). It discusses OSSEC's architecture, features like log analysis, integrity monitoring, rootkit detection, policy auditing and alerts. It also covers installing and configuring OSSEC servers and agents, as well as customizing configuration and rule files. Challenges of deploying OSSEC at large scale are also mentioned.

































![Auth Logs • Brute force attempts followed by a success Rule: 5720 (level 10) > 'Multiple SSHD authentication failures.' Src IP: 125.192.xx.xx Feb 11 09:31:58 wpor sshd[4565]: Failed password for root from 125.192.xx.xx port 42976 ssh2 Feb 11 09:31:58 wpor sshd[4565]: Failed password for admin from 125.192.xx.xx port 42976 ssh2 Feb 11 09:31:58 wpor sshd[4565]: Failed password for admin from 125.192.xx.xx port 42976 ssh2 Rule: 40112 (level 12) > 'Multiple authentication failures followed by a success.' Src IP: 125.192.67.136 User: admin Feb 11 09:31:58 wpor sshd[7235]: Accepted password for admin from 125.192.xx.xx port 42198 ssh2](https://image.slidesharecdn.com/implementandoossec-101212182718-phpapp01/75/Implementing-ossec-54-2048.jpg)