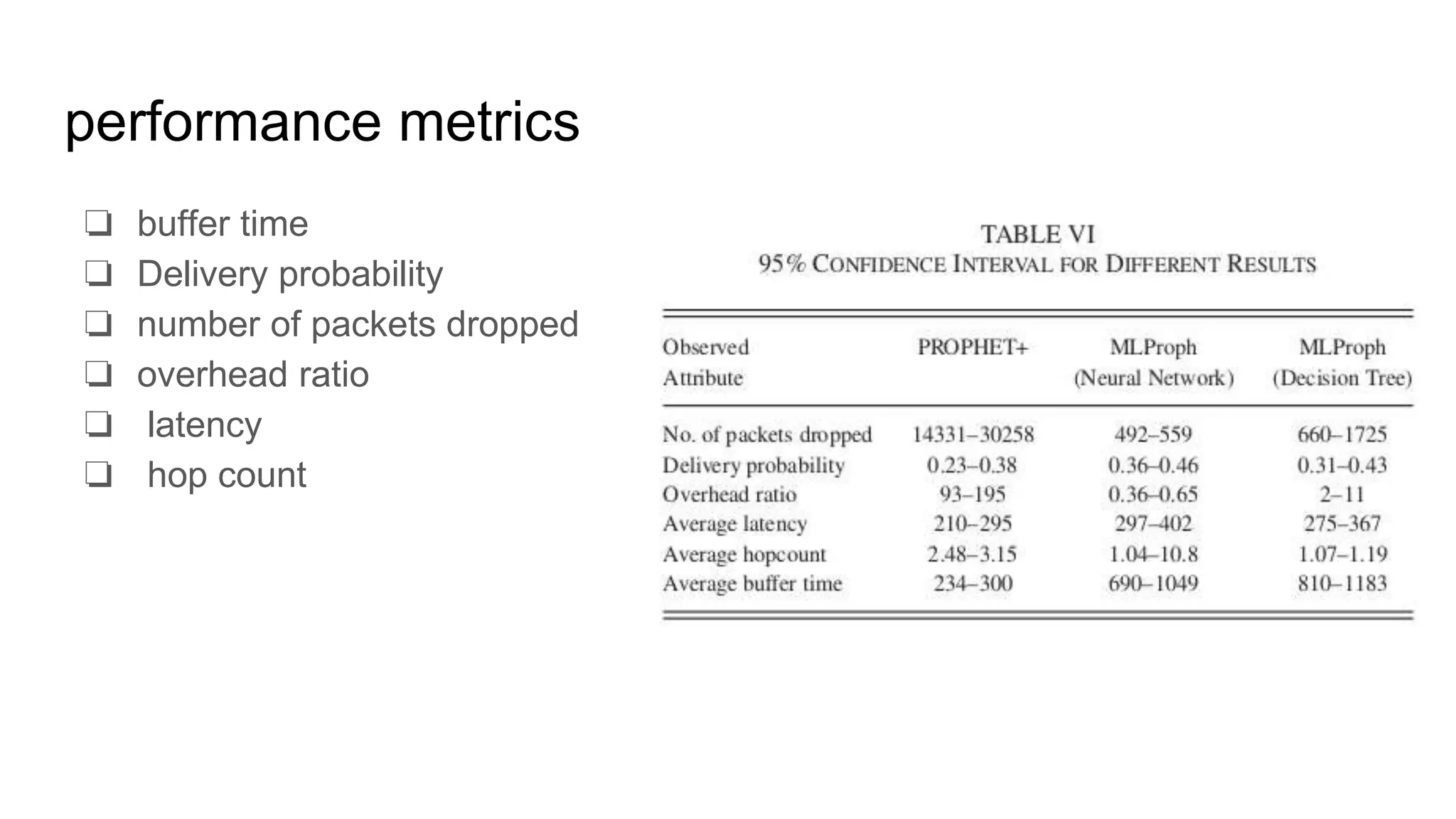
This document presents MLProph, a machine learning-based routing protocol for opportunistic networks. It uses decision trees and neural networks to select the next hop for packet forwarding. Simulation results show that MLProph achieves higher delivery probability and lower packet dropping than the PROPHET+ routing protocol. Future work will involve simulating MLProph using real mobility traces and exploring other machine learning classifiers.






![References [1] L. Lilien, Z. H. Kamal, V. Bhuse, and A. Gupta, “Opportunistic networks: The concept and research challenges in privacy and security,” in Proc. NSF WSPWN, Miami, FL, USA, Mar. 2006, pp. 134–1 [2] C. Boldrini, M. Conti, I. Iacopini, and A. Passarella, “HIBOP: A history based routing protocol for opportunistic networks,” in Proc. IEEE WOWMOM, Espoo, Finland, Jun. 2007, pp. 1–12. [3] A. Vahdat and D. Becker, “Epidemic routing for partially connected ad hoc networks,” Dept. Comput. Sci., Duke Univ., Durham, NC, USA, Tech. Rep. CS-2000-06, 2000. [4] T. K. Huang, C. K Lee, and L.-J. Chen, “PROPHET+: An adaptive prophet-based routing protocol for opportunistic network,” in Proc. 24th IEEE Int. Conf. Adv. Inf. Netw. Appl., Perth, Australia, Apr. 2010, pp. 112–119. [5] S. K. Dhurandher, D. K. Sharma, I. Woungang, and S. Bhati, “HBPR: History based prediction for routing in infrastructure-less opportunistic networks,” in Proc. 27th IEEE Int. Conf. Adv. Inf. Netw. Appl., Barcelona, Spain, Mar. 2013, pp. 931–936. [6] A. Lindgren, A. Doria, and D. Schelen, “Probabilistic routing in intermittently connected networks,” ACM SIGMOBILE Mobile Comp. Commun. Rev., vol. 7, no. 3, pp. 19–20, 2003. [7] S. K. Dhurandher, S. J. Borah, D. K. Sharma, I. Woungang, K. Arora, and D. Agarwal, “EDR: An encounter and distance based routing protocol for opportunistic networks,” in Proc. 30th IEEE Int. Conf. Adv. Inf. Netw. Appl., 2016, pp. 297–302.](https://image.slidesharecdn.com/amachinelearning-basedprotocolforefficientroutinginopportunisticnetworks-180509201430/75/A-machine-learning-based-protocol-for-efficient-routing-in-opportunistic-networks-15-2048.jpg)
![References [8] Y. LeCun, L. Bottou, G. B. Orr, K-R. Muller, “Efficient BackProp,” Neural Networks: Tricks of the Trade, vol. 1524, Lecture Notes Comput. Sci., pp. 9–50, Mar. 2002. [9] R. O. Duda, P. E. Hart, and D. G. Stork, Pattern Classification. Hoboken, NJ, USA: Wiley, Oct. 2012. [10] A. Keranen, “Opportunistic network environment simulator,” Dept. Commun. Netw., Helsinki Univ. Technol., Espoo, Finland, Special Assignment Rep. ONE v. 1.4.1, May 2008. [11] S. Drazin and M. Montag, “Decision tree analysis using Weka,” Machine Learning-Project II, Univ. Miami, Miami, FL, USA, 2012. [Online]. Available: http://www.samdrazin.com/classes/een548/](https://image.slidesharecdn.com/amachinelearning-basedprotocolforefficientroutinginopportunisticnetworks-180509201430/75/A-machine-learning-based-protocol-for-efficient-routing-in-opportunistic-networks-16-2048.jpg)