Imagine every device on the internet as a house. For you to send a letter to a friend living in one of these houses, you need their home address. In the digital world, this home address is what we call an IP (Internet Protocol) Address. It's a unique string of numbers separated by periods (IPv4) or colons (IPv6) that identifies each device connected to the internet or a local network.
Here's the definition:
What is an IP Address?
An IP address, or Internet Protocol address, is a unique string of numbers assigned to each device connected to a computer network that uses the Internet Protocol for communication. It serves as an identifier that allows devices to send and receive data over the network, ensuring that this data reaches the correct destination.
Types of IP Address
IP addresses can be classified in several ways based on their structure, purpose, and the type of network they are used in. Here's a breakdown of the different classifications of IP addresses:
1. Based on Addressing Scheme (IPv4 vs. IPv6)
IPv4:
This is the most common form of IP Address. It consists of four sets of numbers separated by dots. For example, 192.158.1.38. Each set of numbers can range from 0 to 255. This format can support over 4 billion unique addresses. Here's how the structure is broken down:
- Four Octets: Each octet represents eight bits, or a byte, and can take a value from 0 to 255. This range is derived from the possible combinations of eight bits (2^8 = 256 combinations).
- Example of IPv4 Address: 192.168.1.1
- 192 is the first octet
- 168 is the second octet
- 1 is the third octet
- 1 is the fourth octet
Each part of the IP address can indicate various aspects of the network configuration, from the network itself to the specific device within that network. In most cases, the network part of the address is represented by the first one to three octets, while the remaining section identifies the host (device).
 IPv4 Address Format
IPv4 Address FormatIPv6:
IPv6 addresses were created to deal with the shortage of IPv4 addresses. They use 128 bits instead of 32, offering a vastly greater number of possible addresses. These addresses are expressed as eight groups of four hexadecimal digits, each group representing 16 bits. The groups are separated by colons.
- Example of IPv6 Address: 2001:0db8:85a3:0000:0000:8a2e:0370:7334
- Each group (like 2001, 0db8, 85a3, etc.) represents a 16-bit block of the address.
For detailed information, refer to this article - IPv4 vs. IPv6
2. Based on Usage (Public vs. Private)
Public IP Addresses
A Public IP address is assigned to every device that directly accesses the internet. This address is unique across the entire internet. Here are the key characteristics and uses of public IP addresses:
- Uniqueness: Each public IP address is globally unique. No two devices on the internet can have the same public IP address at the same time.
- Accessibility: Devices with a public IP address can be accessed directly from anywhere on the internet, assuming no firewall or security settings block the access.
- Assigned by ISPs: Public IP addresses are assigned by Internet Service Providers (ISPs). When you connect to the internet through an ISP, your device or router receives a public IP address.
- Types: Public IP addresses can be static (permanently assigned to a device) or dynamic (temporarily assigned and can change over time).
Example Use: Public IP addresses are typically used for servers hosting websites, email servers, or any device that needs to be accessible from the internet. For instance, if you host a website on your own server at home, your ISP must assign a public IP address to your server so users around the world can access your site.
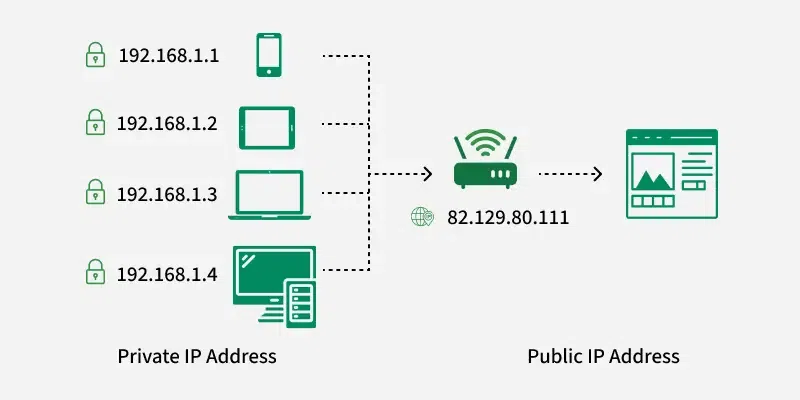
Private IP Addresses
Private IP addresses are used within private networks (such as home networks, office networks, etc.) and are not routable on the internet. This means that devices with private IP addresses cannot directly communicate with devices on the internet without a translating mechanism like a router performing Network Address Translation (NAT). Key features include:
- Not globally unique: Private IP addresses are only required to be unique within their own network. Different private networks can use the same range of IP addresses without conflict.
- Local communication: These addresses are used for communication between devices within the same network. They cannot be used to communicate directly with devices on the internet.
- Defined ranges: The Internet Assigned Numbers Authority (IANA) has reserved specific IP address ranges for private use:
- IPv4: 10.0.0.0 to 10.255.255.255, 172.16.0.0 to 172.31.255.255, 192.168.0.0 to 192.168.255.255
- IPv6: Addresses starting with FD or FC
Example Use: In a typical home network, the router assigns private IP addresses to each device (like smartphones, laptops, smart TVs) from the reserved ranges. These devices use their private IPs to communicate with each other and with the router. The router uses NAT to allow these devices to access the internet using its public IP address.
3. Based on Assignment Method (Static vs. Dynamic)
Static IP Addresses:
- These are permanently assigned to a device, typically important for servers or devices that need a constant address.
- Reliable for network services that require regular access such as websites, remote management.
Dynamic IP Addresses:
- Temporarily assigned from a pool of available addresses by the Dynamic Host Configuration Protocol (DHCP).
- Cost-effective and efficient for providers, perfect for consumer devices that do not require permanent addresses.
For detailed information, refer to this article - Static vs. Dynamic IP Address
How Do IP Addresses Work?
Here's how IP addresses work:
1. Unique Identification
Every device connected to a network, such as computers, smartphones, and servers, is assigned an IP address. This address is used to identify the device on the network, similar to how a home address identifies a specific location.
2. Communication Protocol
The Internet Protocol (IP), part of the broader suite of internet protocols, uses these addresses to facilitate the routing of data packets between devices. Each piece of data sent over a network is broken into smaller units called packets. Each packet includes both the sender's and the recipient's IP addresses.
3. Data Routing
When a device sends information to another device over the internet:
- The data is divided into packets.
- Each packet contains the IP address of the device it is destined for.
- Routers within the network read the destination IP address on each packet and determine the best path for the packet to travel. Routers communicate with each other to update and maintain records of the fastest, most efficient routes for data.
4. Local Area Networks (LAN) and Wide Area Networks (WAN)
- LAN: On local networks, IP addresses can be assigned manually by an administrator (static IP) or automatically by a DHCP server. Devices within the same network communicate directly using their local IP addresses.
- WAN: For devices on different networks, the data must travel through multiple routers across the internet. Each router makes independent decisions about the best route for the packets based on the destination IP address.
5. Network Address Translation (NAT)
Most devices on a home or small business network share a single public IP address when accessing the internet, even though each device has its own private IP address within the local network. NAT is a process where multiple local IP addresses are mapped to a single public IP address. This conserves IP addresses and adds a layer of security by hiding internal IP addresses from the external network.
Real World Scenario: Sending an Email from New York to Tokyo
Let's explore how IP addresses work through a real-world example that involves sending an email from one person to another across the globe:
Step 1: Assigning IP Addresses
- Alice in New York wants to send an email to Bob in Tokyo.
- Alice’s laptop has a private IP address (e.g., 192.168.1.5) assigned by her router at home.
- Bob's computer in Tokyo has a private IP address (e.g., 192.168.2.4) assigned by his router at his office.
Step 2: Connection to the Internet
- Both Alice and Bob’s routers have public IP addresses assigned by their Internet Service Providers (ISPs). These public IP addresses are what the devices use to send and receive data over the internet.
Step 3: Sending the Email
- Alice writes her email and hits send.
- Her email service (e.g., Gmail) packages the message and its attachments into data packets. Each packet includes the source IP (Alice’s router's public IP) and the destination IP (Bob’s email server's public IP).
Step 4: Routing the Packets
- The data packets leave Alice’s laptop and travel to her home router. The router notes that the destination IP is outside the local network.
- The router sends the packets to Alice's ISP. The ISP uses routers that examine the destination IP address of the packets and determine the best route to send them toward their destination.
- The packets may pass through several routers around the world — in data centers in countries like Canada, Germany, and finally Japan. Each router along the way reads the destination IP and forwards the packets accordingly.
Step 5: Reaching Bob
- The packets arrive at Bob's email server's ISP in Tokyo and are then forwarded to the server.
- Bob's email server reassembles the packets into the original email message.
Step 6: Bob Accesses the Email
- Bob’s computer requests the email from his server using his local network IP.
- The server sends the email to Bob's computer, allowing him to read the message Alice sent.
Additional Details
- NAT (Network Address Translation): Both Alice and Bob's routers perform NAT, translating the private IP addresses to and from the public IP addresses when interfacing with the internet. This process is crucial for keeping the number of public IPs needed lower and adds a layer of security by masking internal network structures.
- Dynamic IP Addressing: If either Alice or Bob’s public IP is dynamic, it might change if they restart their routers. This doesn’t affect their ongoing activities much because the DNS (Domain Name System) helps update the mapping of domain names (like gmail.com) to the current IP addresses.
This example illustrates the fundamental role of IP addresses and the complex network of routers involved in even the simplest internet activities like sending an email. Each part of the process depends on the IP address to ensure that data finds its way correctly from sender to receiver, no matter where they are in the world.
---> Other Important Things to Know About IP Address
Classes of IPv4 Address
There are around 4.3 billion IPv4 addresses and managing all those addresses without any classification is next to impossible.
Let’s understand it with a simple example. If you have to find a word from a language dictionary, how long will it take just think about it. Usually you will take less than 5 minutes to find that word. You are able to do this because words in the dictionary are organized in alphabetical order. If you have to find out the same word from a dictionary that doesn’t use any sequence or order to organize the words, it will take an eternity to find the word. If a dictionary with one billion words without order can be so disastrous, then you can imagine the pain behind finding an address from 4.3 billion addresses.
For easier management and assignment IP addresses are organized in numeric order and divided into the following 5 classes:
IP addresses are also classified into different classes based on their range and intended use:
- Class A (1.0.0.0 to 127.255.255.255):
- Used for very large networks (like multinational companies).
- Supports up to 16 million hosts per network.
- Example:
10.0.0.1 (Private IP in this class).
- Class B (128.0.0.0 to 191.255.255.255):
- Used for medium-sized networks, such as large organizations.
- Supports up to 65,000 hosts per network.
- Example:
172.16.0.1 (Private IP in this class).
- Class C (192.0.0.0 to 223.255.255.255):
- Used for smaller networks, like small businesses or home networks.
- Supports up to 254 hosts per network.
- Example:
192.168.1.1 (Private IP in this class).
- Class D (224.0.0.0 to 239.255.255.255):
- Reserved for multicast groups (used to send data to multiple devices at once).
- Not used for traditional devices or networks.
- Class E (240.0.0.0 to 255.255.255.255):
- Reserved for experimental purposes and future use.
| IP Class | Address Range | Maximum number of networks |
|---|
| Class A | 1-126 | 126 (27-2) |
| Class B | 128-191 | 16384 |
| Class C | 192-223 | 2097152 |
| Class D | 224-239 | Reserve for multitasking |
| Class E | 240-254 | Reserved for Research and development |
Special IP Addresses
There are also some special-purpose IP addresses that don't follow the usual structure:
- Loopback Address:
- The loopback address
127.0.0.1 is used to test network connectivity within the same device (i.e., sending data to yourself). - Often called "localhost."
- Broadcast Address:
- The broadcast address allows data to be sent to all devices in a network. For a typical network with the IP range
192.168.1.0/24, the broadcast address would be 192.168.1.255.
- Multicast Address:
- Used to send data to a group of devices (multicast). For example,
233.0.0.1 is a multicast address.
How to Look Up IP Addresses?
In Windows
- Open the Command Prompt.
- Type
ipconfig and press Enter. - Look for your IP under your network connection.
On Mac
- Open System Preferences > Network.
- Select your active connection.
- You’ll see your IP address in the connection details.
On iPhone
- Go to Settings > Wi-Fi.
- Tap the (i) icon next to your network.
- Find your IP under "IP Address."
IP Address Security Threats
IP addresses are essential for connecting devices on the internet, but they also come with various security risks. Understanding these threats can help you protect your network and personal information more effectively. Here are some common IP address security threats:
- IP Spoofing: Hackers use this technique to bypass security measures, launch attacks, or gain unauthorized access to systems. By pretending to be a trusted IP address, attackers can trick networks into granting them access or allowing malicious activities.
- Distributed Denial of Service (DDoS) Attacks: This happens by overloading a website or service with too much traffic. Many hacked devices send lots of requests to a target all at once, making the website or service crash. This means real users can’t access it which can cause crashing of site, businesses to lose money and many more.
- Man-in-the-Middle (MitM) Attacks: Eavesdropping or altering messages between two people without letting them know is MitM attack. Attackers intercept the communication between two parties and can steal sensitive information like passwords or credit card details by targeting the IP addresses involved.
- Port Scanning: It is a technique used to identify open ports and services running on a device's IP address. Hackers use port scanners to find vulnerabilities in network services, which they can then exploit to gain unauthorized access or deploy malware. Regularly monitoring and securing open ports is essential to prevent such attacks.
How to Protect and Hide Your IP Address?
- VPN (Virtual Private Network): A VPN hides your IP by masking it with the VPN server’s IP, giving you privacy. Your internet traffic passes through the VPN server, masking your real IP address with the server’s IP. This makes it difficult for others to track your online activities or identify your location.
- Proxy Server: Routes your data through a different server, hiding your real IP. When you use a proxy, your requests go through the proxy server, which hides your real IP address by replacing it with its own.
- Tor Browser: Encrypts and bounces your data around multiple servers for anonymity. This multi-layered routing makes it extremely difficult to trace your IP address or monitor your online activities.
- Enable Your Firewall: A firewall is a security system that monitors and controls incoming and outgoing network traffic. It can block unauthorized access to your device, making it harder for attackers to target your IP address.
Conclusion
IP addresses are essential for connecting devices over the internet. While they help identify and communicate with other devices, it’s important to protect your IP to keep your information safe and private. IP addresses also come with challenges such as privacy risks and vulnerability to cyberattacks. Understanding both the benefits and drawbacks of IP addresses helps us appreciate their importance in the digital world while enabling the need for effective protection measures.
Similar Reads
CCNA Tutorial for Beginners This CCNA Tutorial is well-suited for the beginner as well as professionals, and It will cover all the basic to advanced concepts of CCNA like Components of Computer Networking, Transport Layer, Network Layer, CCNA training, Cisco Networking, Network Design, Routing and Switching, etc. which are req
8 min read
Basics of Computer Networking
Components of Computer Networking
NIC Full Form - Network Interface CardNIC stands for Network Interface Card. NIC is additionally called Ethernet or physical or network card. NIC is one of the major and imperative components of associating a gadget with the network. Each gadget that must be associated with a network must have a network interface card. Even the switches
4 min read
What is a Network Switch and How Does it Work?The Switch is a network device that is used to segment the networks into different subnetworks called subnets or LAN segments. It is responsible for filtering and forwarding the packets between LAN segments based on MAC address. Switches have many ports, and when data arrives at any port, the destin
9 min read
What is Network Hub and How it Works?Hub in networking plays a vital role in data transmission and broadcasting. A hub is a hardware device used at the physical layer to connect multiple devices in the network. Hubs are widely used to connect LANs. A hub has multiple ports. Unlike a switch, a hub cannot filter the data, i.e. it cannot
6 min read
Introduction of a RouterNetwork devices are physical devices that allow hardware on a computer network to communicate and interact with one another. For example Repeater, Hub, Bridge, Switch, Routers, Gateway, Router, and NIC, etc. What is a Router?A Router is a networking device that forwards data packets between computer
12 min read
Types of Ethernet CableAn ethernet cable allows the user to connect their devices such as computers, mobile phones, routers, etc, to a Local Area Network (LAN) that will allow a user to have internet access, and able to communicate with each other through a wired connection. It also carries broadband signals between devic
5 min read
Transport Layer
Transport Layer responsibilitiesThe transport Layer is the second layer in the TCP/IP model and the fourth layer in the OSI model. It is an end-to-end layer used to deliver messages to a host. It is termed an end-to-end layer because it provides a point-to-point connection rather than hop-to-hop, between the source host and destin
5 min read
Introduction of Ports in ComputersA port is basically a physical docking point which is basically used to connect the external devices to the computer, or we can say that A port act as an interface between the computer and the external devices, e.g., we can connect hard drives, printers to the computer with the help of ports. Featur
3 min read
What is TCP (Transmission Control Protocol)?Transmission Control Protocol (TCP) is a connection-oriented protocol for communications that helps in the exchange of messages between different devices over a network. It is one of the main protocols of the TCP/IP suite. In OSI model, it operates at the transport layer(Layer 4). It lies between th
5 min read
TCP 3-Way Handshake ProcessThe TCP 3-Way Handshake is a fundamental process that establishes a reliable connection between two devices over a TCP/IP network. It involves three steps: SYN (Synchronize), SYN-ACK (Synchronize-Acknowledge), and ACK (Acknowledge). During the handshake, the client and server exchange initial sequen
6 min read
User Datagram Protocol (UDP)User Datagram Protocol (UDP) is a Transport Layer protocol. UDP is a part of the Internet Protocol suite, referred to as UDP/IP suite. Unlike TCP, it is an unreliable and connectionless protocol. So, there is no need to establish a connection before data transfer. The UDP helps to establish low-late
10 min read
Network Layer
IPv4 Addressing
Subnetting
Data Link Layer
Physical Layer
Cisco Networking Devices
Network Devices (Hub, Repeater, Bridge, Switch, Router, Gateways and Brouter)Network devices are physical devices that allow hardware on a computer network to communicate and interact with each other. Network devices like hubs, repeaters, bridges, switches, routers, gateways, and brouter help manage and direct data flow in a network. They ensure efficient communication betwe
9 min read
Collision Detection in CSMA/CDCSMA/CD (Carrier Sense Multiple Access/ Collision Detection) is a media access control method that was widely used in Early Ethernet technology/LANs when there used to be shared Bus Topology and each node ( Computers) was connected by Coaxial Cables. Nowadays Ethernet is Full Duplex and Topology is
7 min read
Collision Domain and Broadcast Domain in Computer NetworkPrerequisite - Network Devices, Transmission Modes The most common network devices used are routers and switches. But we still hear people talking about hubs, repeaters, and bridges. Do you ever wonder why these former devices are preferred over the latter ones? One reason could be: 'because they ar
5 min read
Difference between layer-2 and layer-3 switchesA switch is a device that sends a data packet to a local network. What is the advantage of a hub? A hub floods the network with the packet and only the destination system receives that packet while others just drop due to which the traffic increases a lot. To solve this problem switch came into the
5 min read