Amazon VPC - Introduction to Amazon Virtual Private Cloud
Last Updated : 24 Oct, 2025
A VPC is an on-demand, configurable pool of shared cloud resources allocated within a public cloud environment, providing a logically isolated section of that provider's infrastructure. It functions as a private, virtualized network that mirrors a traditional on-premises data center but is endowed with the scalability and agility of the cloud. By creating a VPC, an organization carves out its own secure and private space, transforming the open public cloud into a manageable domain where its data and applications are not commingled with those of other tenants.
This architectural choice yields several strategic benefits:
- Security: The logical isolation of a VPC is its paramount feature. It creates a secure environment with strict access controls, ensuring that resources are shielded from unauthorized access and isolated from other customers of the cloud provider.
- Agility and Scalability: A VPC allows an organization to fully control its virtual network size and deploy or scale cloud resources in real time as needs change, unconstrained by the physical limitations of hardware procurement and installation.
- Availability: VPCs are designed to leverage the cloud provider's underlying infrastructure, which includes fault-tolerant architectures spanning multiple physical data centers, known as Availability Zones. This provides inherent redundancy and high availability for deployed applications.
- Affordability: Organizations gain the functionality of a private cloud without the significant capital expenditure on hardware, maintenance, and labor. They benefit from the public cloud's pay-as-you-go model, while the provider manages the upkeep of the physical servers.
Example
Let's try to understand it by taking an example of the GeeksforGeeks office setup. Just like GeeksforGeeks carefully organizes its departments and controls access, a VPC organizes and secures resources in the AWS cloud.
- The entire GeeksforGeeks office building = VPC (a private space where everything is managed securely)
- Different departments like Editorial, Development, HR = Subnets (some open for external interaction, some private for internal work)
- Security guards at every gate = Security Groups and Firewalls (deciding who can enter or leave)
- The internet connection for employees and visitors = Internet Gateway (allowing public access where needed)
- Private tunnels connecting to partner companies = VPN or Direct Connect (secure, private connections to other trusted networks)
Amazon VPC Architecture Overview
The basic architecture of a properly functioning VPC consists of many distinct services such as Gateway, Load Balancer, Subnets, etc. Altogether, these resources are clubbed under a VPC to create an isolated virtual environment. Along with these services, there are also security checks on multiple levels.
It is initially divided into subnets, connected with each other via route tables along with a load balancer.
.png)
Core Components of Amazon VPC
The following are the components of Amazon VPC:
1. VPC
Virtual Private Cloud is a logically isolated section of the AWS cloud where resources can be launched, secured, and interconnected. Each VPC is defined by an IPv4 CIDR block (for example, 10.0.0.0/16), representing a user-defined address space of up to 65,536 IP addresses. This virtual network mirrors an on-premises data center but inherits the elasticity, scalability, and resilience of AWS’s global infrastructure.
2. Subnets
A Subnet is a segment of a VPC’s IP address range that resides entirely within a single Availability Zone (AZ).
Subnets serve two primary purposes:
- Segmentation: They divide large networks into smaller, isolated zones for better organization and control.
- High Availability: Distributing subnets across multiple AZs ensures fault tolerance and operational continuity.
Subnets are typically categorized as:
- Public Subnets, which route internet-bound traffic through an Internet Gateway (IGW).
- Private Subnets, which are isolated from direct internet access and communicate externally through a NAT Gateway.
This distinction forms the foundation of secure, multi-tier cloud architectures.
3. Route Tables
EachVPC contains an implicit virtual router that relies on Route Tables to direct traffic. Every subnet must be associated with exactly one route table, and each route defines:
- A destination CIDR block (where the traffic is headed).
- A target (where the traffic should be sent, such as an Internet Gateway, NAT Gateway, or another instance).
Route tables determine whether traffic remains internal to the VPC or is sent to external networks. They are the digital roadmap of the cloud network.
4. Network Access Control Lists
Network Access Control Lists (NACLs) are stateless firewalls that govern inbound and outbound traffic at the subnet level. Each VPC comes with a default NACL, which can be modified but not deleted. Unlike Security Groups, NACLs evaluate each packet individually and require explicit rules for both inbound and outbound flows. They are typically used to implement broad subnet-level controls, such as blocking specific IP ranges or enforcing compliance requirements across multiple instances.
5. Internet Gateway(IGW)
An Internet Gateway is a horizontally scaled, redundant component that enables bidirectional communication between public subnets and the internet. By attaching an IGW to a VPC and creating a route (e.g., 0.0.0.0/0) to it in a public subnet’s route table, instances within that subnet can send and receive traffic from the internet. A VPC can have only one attached Internet Gateway at a time. Without an IGW, no instance within the VPC can directly communicate with the public internet.
6. Network Address Translation (NAT)
NAT Gateways allow instances in private subnets to initiate outbound internet connections such as downloading updates or accessing APIs while preventing unsolicited inbound connections. This enables backend systems to communicate securely with external services without compromising isolation. In most architectures, NAT Gateways are deployed in public subnets, serving as controlled egress points for private subnets.
7. Security Groups
While NACLs operate at the subnet level, Security Groups act as stateful firewalls at the instance level. They define granular inbound and outbound rules based on IP ranges, ports, and protocols. Statefulness means that if an instance initiates an outbound connection, the return traffic is automatically allowed simplifying rule management. Security Groups form the first layer of defense for EC2 instances, RDS databases, and other VPC resources.
8. Classless Inter-Domain Routing (CIDR):
CIDR notation defines the IP range of a VPC or subnet, using syntax such as 10.0.0.0/16.
It provides flexibility in assigning and subdividing private address ranges as specified in RFC 1918, which includes:
10.0.0.0 - 10.255.255.255 (10/8)172.16.0.0 - 172.31.255.255 (172.16/12)192.168.0.0 - 192.168.255.255 (192.168/16)
These address blocks ensure isolation within private networks and avoid conflicts with public IP space
Use cases of Amazon VPC
The following are use cases of Amazon VPC:
- Hosting public-facing applications (e.g., web servers, load balancers) within public subnets.
- Deploying multi-tier architectures, where application and database layers reside in private subnets.
- Establishing secure interconnections between VPCs through peering or AWS Transit Gateway.
- Enforcing network security and compliance through traffic isolation, monitoring (VPC Flow Logs), and access control.
Amazon VPC (Virtual Private Cloud) Working
Follow the steps mentioned below to configure Virtual Private Cloud(VPC)
Step 1: Login into AWS Console and navigate to the VPC as shown below.
.webp)
Step 2: After navigating to the AWS VPC now click on create VPC.
-(2).png)
Step 3: Configure all the details required to create as shown in the image below. Some of the most required settings to configure VPC are as follows
- Name of the Network.
- IPv4 CIDR.
- And tags of VPC after that click on create VPC.

Step 4: Virtual Private Cloud created successfully with the required settings.
.webp)
Step 5: Check the VPC dashboard whether the VPC created is available to use as shown in the image below GFG-VPC.
.png)
AWS VPC Console
To create and manage a Virtual Private Cloud (VPC) in AWS, follow these steps:
- Log in to your AWS account.
- Once inside the AWS Management Console, click on the “Services” menu at the top.
- From the list of categories, navigate to “Networking & Content Delivery”.
- Select “VPC” from the options provided.
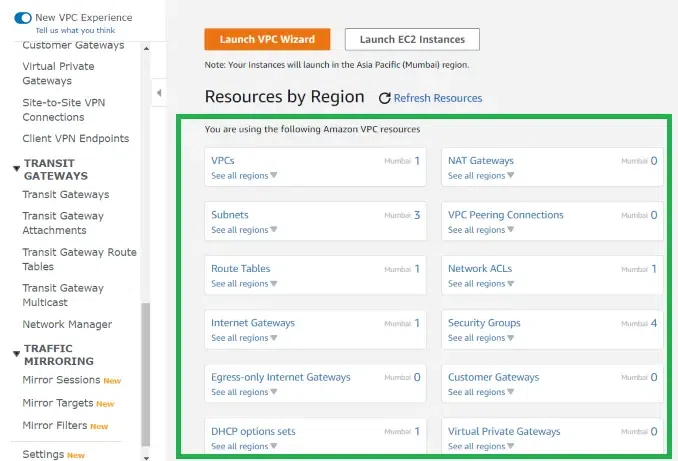
After selecting VPC, you will be redirected to the VPC dashboard. On the left-hand side, the navigation pane displays various options and services related to VPC management.
Refer to the image attached below for a better understanding.
Explore
DevOps Basics
Version Control
CI & CD
Containerization
Orchestration
Infrastructure as Code (IaC)
Monitoring and Logging
Security in DevOps
My Profile