Basics of Computer Networking
Last Updated : 08 Jul, 2025
A computer network is a collection of interconnected devices that share resources and information. These devices can include computers, servers, printers, and other hardware. Networks allow for the efficient exchange of data, enabling various applications such as email, file sharing, and internet browsing.
Basic Terminologies of Computer Networks
- Network: A group of connected computers and devices that can communicate and share data with each other.
- Node: Any device that can send, receive, or forward data in a network. This includes laptops, mobiles, printers, earbuds, servers, etc.
- Networking Devices: Devices that manage and support networking functions. This includes routers, switches, hubs, and access points.
- Transmission Media: The physical or wireless medium through which data travels between devices. Wired media: Ethernet cables, optical fiber. Wireless media: Wi-Fi, Bluetooth, infrared
- Service Provider Networks: Networks offered by external providers that allow users or organizations to lease network access and capabilities. This includes internet providers, mobile carriers, etc.
We will be discussing more terms like Protocol, IP Address, DNS, etc below in this article.
How Does a Computer Network Work?
Basics building blocks of a Computer network are Nodes and Links. A Network Node can be illustrated as Equipment for Data Communication like a Modem, Router, etc., or Equipment of a Data Terminal like connecting two computers or more. Link in Computer Networks can be defined as wires or cables or free space of wireless networks.
The working of Computer Networks can be simply defined as rules or protocols which help in sending and receiving data via the links which allow Computer networks to communicate. Each device has an IP Address, that helps in identifying a device.
.jpg)
Types of Computer Network Architecture
Computer Network falls under these broad Categories:
- Client-Server Architecture: Client-Server Architecture is a type of Computer Network Architecture in which Nodes can be Servers or Clients. Here, the server node can manage the Client Node Behaviour.
- Peer-to-Peer Architecture: In P2P (Peer-to-Peer) Architecture, there is not any concept of a Central Server. Each device is free for working as either client or server.
Network Devices
An interconnection of multiple devices, also known as hosts, that are connected using multiple paths for the purpose of sending/receiving data or media. Computer networks can also include multiple devices/mediums which help in the communication between two different devices; these are known as Network devices and include things such as routers, switches, hubs, and bridges.
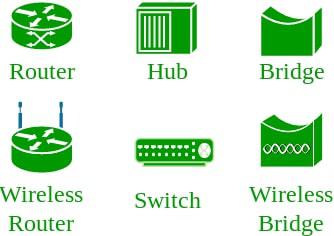 Network Devices
Network DevicesNetwork Topology
The Network Topology is the layout arrangement of the different devices in a network. Some types of network topologies are,
- Bus Topology: In bus topology all devices are connected to a single central cable called a bus.
- Star Topology: In star topology all devices are connected to a central node called hub or switch.
- Ring Topology: In ring topology devices are connected in a circular loop with each device connected to two others. Data travels in one direction (or sometimes both) passing through each device until it reaches its destination.
- Mesh Topology: In mesh topology every device is connected to every other device in the network.
- Tree Topology: Tree topology is the combination of star and bus topology. Tree topology is good for organizing large networks and allows for easy expansion.
- Hybrid Topology: Hybrid topology is the combination of two or more different topologies (like star and mesh).
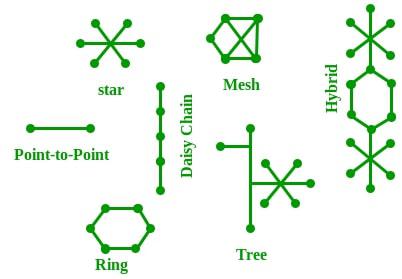 Network Topology
Network TopologyOSI Model
OSI stands for Open Systems Interconnection. It is a reference model that specifies standards for communications protocols and also the functionalities of each layer. The OSI has been developed by the International Organization For Standardization and it is 7 layer architecture. Each layer of OSI has different functions and each layer has to follow different protocols. The 7 layers are as follows:
Network Protocols
A protocol is a set of rules or algorithms which define the way how two entities can communicate across the network and there exists a different protocol defined at each layer of the OSI model. A few such protocols are TCP, IP, UDP, ARP, DHCP, FTP, and so on.
- Transmission Control Protocol/Internet Protocol (TCP/IP): TCP/IP is the foundational protocol suite of the internet, enabling reliable communication. TCP Ensures data is delivered reliably and in order and IP routes data packets to their destination based on IP addresses.
- Hypertext Transfer Protocol (HTTP) and HTTPS: HTTP and HTTPS protocols used for transmitting web pages. In HTTP communication is unsecured and in HTTPS secured communication using SSL/TLS encryption.
- Simple Mail Transfer Protocol (SMTP): SMTP protocol used to send email. SMTP protocol works with other protocols like POP3 and IMAP for email retrieval.
- File Transfer Protocol (FTP): FTP protocol used for transferring files between computers. Includes commands for uploading, downloading, and managing files on a remote server.
- Dynamic Host Configuration Protocol (DHCP): DHCP protocol automatically assigns IP addresses to devices on a network. Reduces manual configuration and IP address conflicts.
- Domain Name System (DNS): DNS Translates human-friendly domain names into IP addresses. Ensures seamless navigation on the internet.
Unique Identifiers of Network
Hostname: Each device in the network is associated with a unique device name known as Hostname. Type “hostname” in the command prompt(Administrator Mode) and press ‘Enter’, this displays the hostname of your machine.
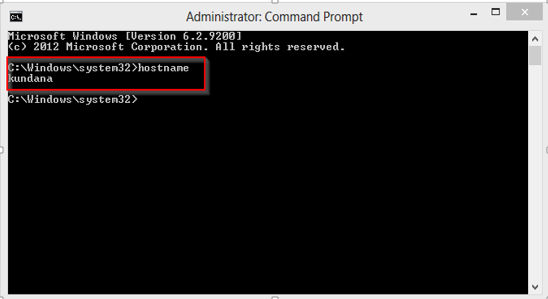 HostName
HostName
IP Address (Internet Protocol address): Also known as the Logical Address, the IP Address is the network address of the system across the network. To identify each device in the world-wide-web, the Internet Assigned Numbers Authority (IANA) assigns an IPV4 (Version 4) address as a unique identifier to each device on the Internet. The length of an IPv4 address is 32 bits, hence, we have 232 IP addresses available. The length of an IPv6 address is 128 bits.
In Windows Type “ipconfig” in the command prompt and press ‘Enter’, this gives us the IP address of the device. For Linux, Type “ifconfig” in the terminal and press ‘Enter’ this gives us the IP address of the device.
MAC Address (Media Access Control address): Also known as physical address, the MAC Address is the unique identifier of each host and is associated with its NIC (Network Interface Card). A MAC address is assigned to the NIC at the time of manufacturing. The length of the MAC address is: 12-nibble/ 6 bytes/ 48 bits Type “ipconfig/all” in the command prompt and press ‘Enter’, this gives us the MAC address.
Port: A port can be referred to as a logical channel through which data can be sent/received to an application. Any host may have multiple applications running, and each of these applications is identified using the port number on which they are running.
A port number is a 16-bit integer, hence, we have 216 ports available which are categorized as shown below:
| Port Types | Range |
|---|
| Well known Ports | 0 – 1023 |
| Registered Ports | 1024 – 49151 |
| Ephemeral Ports | 49152 - 65535 |
Number of ports: 65,536
Range: 0 – 65535
Type “netstat -a” in the command prompt and press ‘Enter’, this lists all the ports being used.
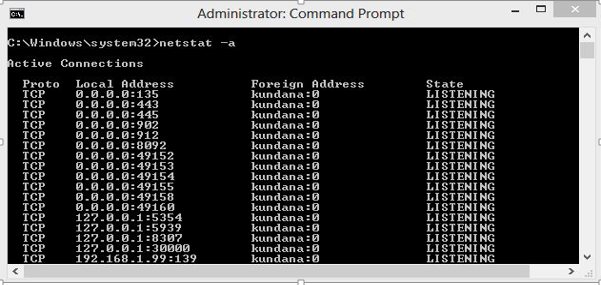 List of Ports
List of PortsSocket: The unique combination of IP address and Port number together is termed a Socket.
DNS Server: DNS stands for Domain Name System. DNS is basically a server that translates web addresses or URLs (ex: www.google.com) into their corresponding IP addresses. We don’t have to remember all the IP addresses of each and every website. The command ‘nslookup’ gives you the IP address of the domain you are looking for. This also provides information on our DNS Server. \
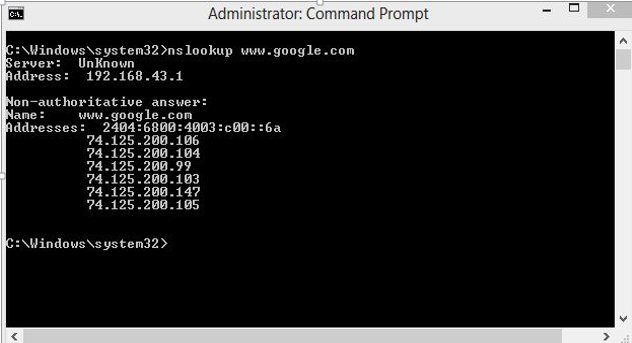 Domain IP Address
Domain IP AddressARP: ARP stands for Address Resolution Protocol. It is used to convert an IP address to its corresponding physical address(i.e., MAC Address). ARP is used by the Data Link Layer to identify the MAC address of the Receiver’s machine.
RARP: RARP stands for Reverse Address Resolution Protocol. As the name suggests, it provides the IP address of the device given a physical address as input. But RARP has become obsolete since the time DHCP has come into the picture.
The Domain Name System (DNS) is a critical component of computer networking. It converts easily recognizable domain names, such as www.example.com, into numerical IP addresses that computers use to identify each other on the network.
How DNS Works?
DNS works efficiently, translating user-friendly domain names into IP addresses, allowing seamless navigation on the internet. Below step by step working of DNS:
- User Input: When a user enters a domain name in a browser, the system needs to find its IP address.
- DNS Query: The user's device sends a DNS query to the DNS resolver.
- Resolver Request: The DNS resolver checks its cache for the IP address. If not found, it forwards the request to the root DNS server.
- Root DNS Server: The root DNS server provides the address of the TLD (Top-Level Domain) server for the specific domain extension (e.g., .com).
- TLD DNS Server: The TLD server directs the resolver to the authoritative DNS server for the actual domain.
- Authoritative DNS Server: The authoritative DNS server knows the IP address for the domain and provides it to the resolver.
- Response to User: The resolver stores the IP address in its cache and sends it to the user's device.
- Access Website: With the IP address, the user's device can access the desired website.
Please refer How DNS works for more details.
Network Security
Ensuring the security of a network is crucial to protect data and resources from unauthorized access and attacks. Key aspects of network security include:
- Firewalls: Devices or software that monitor and control incoming and outgoing network traffic based on security rules.
- Encryption: The process of encoding data to prevent unauthorized access. Commonly used in VPNs, HTTPS, and secure email.
- Intrusion Detection Systems (IDS): Tools that monitor network traffic for suspicious activity and potential threats.
- Access Control: Mechanisms that restrict access to network resources based on user identity and role.
- Regular Updates and Patching: Keeping software and hardware up to date to protect against vulnerabilities.
Characteristics of Computer Networks
Computer networks are systems that connect multiple devices to facilitate communication, resource sharing, and data transfer. They possess several key characteristics that ensure efficient and secure operations. These characteristics include Security, Reliability, Scalability, Performance, Fault Tolerance, and hardware and software support. Please refer Characteristics of Computer Networks for more details.
Similar Reads
Basics of Computer Networking A computer network is a collection of interconnected devices that share resources and information. These devices can include computers, servers, printers, and other hardware. Networks allow for the efficient exchange of data, enabling various applications such as email, file sharing, and internet br
10 min read
Types of Network Topology Network topology refers to the arrangement of different elements like nodes, links, or devices in a computer network. Common types of network topology include bus, star, ring, mesh, and tree topologies, each with its advantages and disadvantages. In this article, we will discuss different types of n
11 min read
Transmission Modes in Computer Networks (Simplex, Half-Duplex and Full-Duplex) Transmission modes also known as communication modes, are methods of transferring data between devices on buses and networks designed to facilitate communication. They are classified into three types: Simplex Mode, Half-Duplex Mode, and Full-Duplex Mode. In this article, we will discuss Transmission
6 min read
Manchester Encoding in Computer Network Manchester encoding is a synchronous clock encoding technique used by the physical layer of the Open System Interconnection to encode the clock and data of a synchronous bit stream. The idea of RZ and the idea of L are combined in manchester encoding. Different encoding techniques are used in data c
9 min read
Difference between Broadband and Baseband Transmission In communication systems, Broadband and Baseband refer to two different ways of transmitting data. They differ in how data is sent over a communication medium, the frequency range they use, and their applications.Broadband systems use modulation techniques to reduce the effect of noise in the enviro
6 min read
What is OSI Model? - Layers of OSI Model The OSI (Open Systems Interconnection) Model is a set of rules that explains how different computer systems communicate over a network. OSI Model was developed by the International Organization for Standardization (ISO). The OSI Model consists of 7 layers and each layer has specific functions and re
13 min read
TCP/IP Model The TCP/IP model is a framework that is used to model the communication in a network. It is mainly a collection of network protocols and organization of these protocols in different layers for modeling the network.It has four layers, Application, Transport, Network/Internet and Network Access.While
7 min read
Multiple Access Protocols in Computer Network Multiple Access Protocols are methods used in computer networks to control how data is transmitted when multiple devices are trying to communicate over the same network. These protocols ensure that data packets are sent and received efficiently, without collisions or interference. They help manage t
9 min read
Framing in Data Link Layer Frames are the units of digital transmission, particularly in computer networks and telecommunications. Frames are comparable to the packets of energy called photons in the case of light energy. Frame is continuously used in Time Division Multiplexing process. Framing is a point-to-point connection
6 min read
What is Ethernet? A LAN is a data communication network connecting various terminals or computers within a building or limited geographical area. The connection between the devices could be wired or wireless. Although Ethernet has been largely replaced by wireless networks, wired networking still uses Ethernet more f
9 min read