File Control Filter Driver SDK
Download EaseFilter File Control SDK Setup File Download EaseFilter File Control SDK Zip File
EaseFilter File Control Filter Driver SDK
The EaseFilter File Control SDK is a powerful development toolkit for creating robust, kernel-level file security and data protection solutions on the Windows platform. It includes a high-performance file system filter driver that intercepts and manages all file I/O operations in real time, giving developers deep, granular control far beyond what is possible with standard Windows APIs or Access Control Lists (ACLs).
EaseFilter File Control Filter Driver integrates into the Windows I/O stack, intercepting file system operations before they reach the disk. This allows the driver to:
- Inspect file operations (e.g., CreateFile, ReadFile, WriteFile)
- Deny a request (e.g., return “access denied”)
- Modify data being read or written
- Log user, process, timestamp, and file details

File Access Control With Flexible Filter Rules
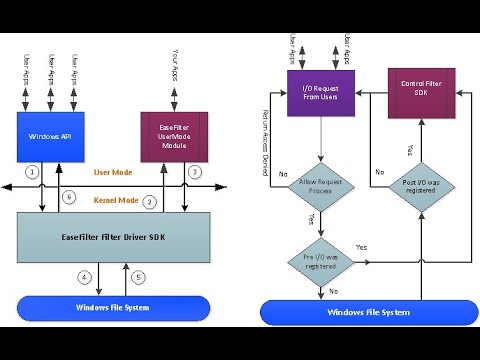
The EaseFilter Control Filter Driver provides a powerful method for intercepting file I/O operations at both the pre-operation and post-operation stages. This dual-layered interception enables comprehensive monitoring and enforcement of file access policies.
The EaseFilter File Control SDK installs a minifilter driver at the kernel level that sits between the Windows I/O Manager and the file system driver. When a process requests file access (e.g., CreateFile, WriteFile, DeleteFile), the request passes through the EaseFilter driver first.
- Pre-Operation Callbacks (PRE-IO): Let you allow, block, or modify the request before it reaches the file system.
- Post-Operation Callbacks (POST-IO): Let you log or audit operations after they occur.
Filter Rule Matching
The intercepted I/O request is compared against user-defined filter rules, which can be based on:
- Include/Exclude File/Folder Path Masks
- Use wildcards to specify which files or folders to monitor or protect. You can also set exclude masks to create exceptions.
- Example:
- C:\Sensitive\*
- *.docx
- D:\Projects\Report_?.pdf
- Include/Exlude Process Name / Path
- You can define specific processes to be included or excluded from the protection policies. This allows you to protect files from malicious software while allowing trusted applications to access them.
- Trusted process verification :
- Verify trusted processes by checking their signed digital certificate signature.
- Verify trusted processes by validating the SHA-256 hash of their binary.
- User or Security Identifier (SID)
- Allow or block based on Windows user accounts or groups.
- Access Type
- Control read, write, delete, or metadata changes separately.
- Time-based Rules
- Limit access to certain hours or dates.
Static File Access Control Using Predefined Filter Rules
The EaseFilter File Control SDK allows you to predefine filter rules with access control flags directly in the filter driver. During pre- and post-operation checks the driver evaluates matching rules and—based on the flags—will allow, deny, or modify file operation behavior.
You can remove specific permissions dynamically by clearing flags using the bitwise AND & ~ operator. Create a FileFilterRule object and assign access control flags as shown below:
FileFilterRule rule = new FileFilterRule(@"c:\protected\*"); // Example: Block delete and rename operations rule.AccessFlag = AccessFlag.ALLOW_MAX_ACCESS & ~AccessFlag.ALLOW_FILE_DELETE & ~AccessFlag.ALLOW_FILE_RENAME; Dynamic File Access Control with Callbacks
Dynamic file access control uses the filter driver’s pre- and post-operation callbacks to make real-time allow/deny/modify decisions. Instead of only relying on static rules, callbacks let your user-mode logic (policy engine, AI service, user input, or a database lookup) evaluate each request at runtime and respond immediately — for example, blocking a write if the process is untrusted or allowing access after an on-the-fly authorization check.
FileFilterRule rule = new FileFilterRule(@"c:\protected\*"); rule.AccessFlag = AccessFlag.ALLOW_MAX_ACCESS; //Register the pre-write callback.
rule.ControlFileIOEventFilter = (ControlFileIOEvents.OnPreFileWrite); rule.OnPreWrite += (sender, e) => { if ( !IsTrustedProcess(e.ProcessName)) { e.ReturnStatus = NtStatus.StatusAccessDenied; e.FilterReply.ReturnMessage = "Untrusted process write blocked."; } }; Key Features of the EaseFilter File Control Filter Driver SDK
-
Real-Time File Access Control
Intercept and control file operations in real time, including create, open, read, write, rename, and delete actions. -
User and Process-Based Access Policies
Define granular access control rules based on process names, user identities (SIDs), or security groups. -
Pre-Operation and Post-Operation Filtering
Register callbacks to monitor or control I/O requests before or after they are processed by the Windows file system. -
Custom File Access Blocking
Block unauthorized access to files or directories with custom return statuses and user-defined behavior. -
File Monitoring and Auditing
Capture detailed file I/O activities including timestamps, file names, process info, and user data for audit logs or alert systems. -
Transparent File Encryption Integration
Seamlessly integrate with EEFD for transparent file encryption and decryption, tied to access control policies. -
Tamper-Proof File Protection
Prevent file modification, movement, or deletion, ensuring critical files remain intact and secure. -
Support for Virtual File Systems and Sandbox Environments
Create virtual views of files or redirect file access to secure locations without affecting user applications. -
Low-Level Kernel-Mode Implementation
Built on a Windows file system minifilter driver architecture for high-performance and stable kernel-mode operation. -
Developer-Friendly SDK Interface
Includes a comprehensive API, sample code, and documentation to accelerate development and integration. -
Supports All Major Windows Versions
Compatible with Windows 7 through Windows 11 and Windows Server editions, including both 32-bit and 64-bit architectures. -
Built-In Event Reporting and Callback Handling
Receive real-time notifications and handle I/O events in your own applications for customized workflows.
Common Use Cases
- Custom Endpoint Security Agents: Monitor and block malicious file activity.
- DLP and File Tracking: Log every access and modification.
- Zero-Trust Security: Allow only approved apps/users to access specific files or folders.
- Ransomware Protection: Stop unauthorized encryption or deletion of critical files.
- Audit & Compliance Tools: Capture a full file I/O history for reporting.
EaseFilter File Control SDK + AI
In today’s enterprise environments, data security threats are increasingly sophisticated. Traditional rule-based file access controls are no longer enough — organizations need adaptive, context-aware security that can evaluate each file operation in real time. This is where EaseFilter File Control SDK combined with AI becomes a powerful solution.
By integrating an AI decision engine, you can move past static filter rules and add adaptive, context-aware protection. AI integration gives your Windows applications the intelligence to secure sensitive files dynamically. AI models can:
- Detect unusual file access patterns. Identify anomalies such as mass reads/writes, atypical time-of-day access, or sudden spikes in activity.
- Identify potentially malicious processes. Correlate process behavior, provenance, and reputation to flag risky executables.
- Make decisions based on context, behavior, and history. Combine user role, past access patterns, file sensitivity, and temporal context to allow, block, or escalate.
C# – AI-Driven File Access Control
FileFilterRule rule = new FileFilterRule(@"c:\protected\*"); rule.AccessFlag = AccessFlag.ALLOW_MAX_ACCESS; //Register the pre-write callback.
rule.ControlFileIOEventFilter = (ControlFileIOEvents.OnPreFileWrite); rule.OnPreWrite += (sender, e) => { var json = $"{{\"file\":\"{e.FileName}\",\"process\":\"{e.ProcessName}\"}}"; var response = await client.PostAsync("http://localhost:5000/decision", new StringContent(json, Encoding.UTF8, "application/json")); string decision = await response.Content.ReadAsStringAsync(); if (decision.Equals("block", StringComparison.OrdinalIgnoreCase)) { e.BlockAccess = true; Console.WriteLine($"AI blocked: {e.FileName}"); } }; Python – AI Decision Service
@app.route("/decision", methods=["POST"]) def decision(): data = request.get_json() file = data.get("file", "").lower() process = data.get("process", "").lower() if "secret" in file or process in ["malware.exe", "unknown"]: return "block" return "allow" File Control Demo Video