Suite
VES APIs

VESauth

VESmail
VESencrypt
Safety and Security
VES establishes a new paradigm in the combination of safety from key loss, and the full security of undiluted end-to-end-encryption (e2ee). In the past, users would have to choose between uncompromised e2ee with no chance of recovering encrypted content if the key is lost, and giving a third party a copy of the encryption key for some safety but at the price of diminished privacy and a substantial risk to security.
With VES, users can maintain the integrity of e2ee security while also having safety from key loss. This unique combination enables e2ee for data-at-rest to be practical for mainstream use, and applicable in places were it currently is not used.
Benchmark safety
Go to the Safety section below to learn more about how VES can reduce the risk of key loss to lower than 1 in 14 trillion! Those odds are much lower than any other key recovery method of which we know. Not only does VES provide safety without compromising security, it can provide a new benchmark in that level of safety too.
Go to the Security section below to learn more about the preservation of e2ee and other security measures of VES.
Simple to create & setup
The easiest and best way to create a VES account is by signing up with a 3rd party app through VESauth. VESauth is present whenever you see the Secured by VESvault logo as you sign up with the app.
Through VESauth, you'll enter your email address and receive a security code with which to create a 4-8 digit PIN. Your PIN is necessary to decrypt your VESkey, which is stored in the 3rd party app or in the browser local storage if the 3rd party product is browser based instead of an app. Don't forget your PIN, but especially don't lose your VESkey.
You'll then have the opportunity to create multiple key redundancies to protect you from losing your VESkey.
Post VES setup
There may be additional setup steps specific to the 3rd party app. With a crypto wallet, this may include securing a wallet seed. With VESmail, this pertains to configuring the email app with the VESmail settings that are single-click copied from your VESmail Account Manager page and pasted into the exactly matching fields in your email app.
Simple to add a device
You essentially repeat the above process when you want to add another device for your VES enabled app, but with one step swaped out for another. Instead of receiving an email with a link, you will enter your PIN on the device that already has your VES account connected to it to enable the same VESkey on the new device. Very simple, very fast.
Another way
You can also add your VES account to another device without including the 3rd party app in the process, by using the drop down menu on the upper left on this page. But, it's faster, easier and better if you do it through the 3rd part app so that you can immediately use the app on the new device.
Using VES - simply invisible
Generally, VES works invisibly behind the scenes and your never need to think about it. For full cryptographic grade access security, some VES enabled apps, such as crypto wallets, may require you to enter your PIN every time you access this app. Other apps, such as VESmail, may not require this to use the app.
Level 1: the VES enabled 3rd party app
You may have multiple VES enabled apps. Each app has its own dedicated app encryption key, which enables the app to function. You have a single VESkey, which is the master encryption. Your VESkey is always stored locally on your device - it may be in the app itself or it may be in the browser local storage. The app itself, or the browser with which it may be connected, is the primary location for your keys. Should the key(s) at this location become inaccessible, you will need to retrieve a copy from another key redundancy location.
Level 2: VES browser extension
When a 3rd party service uses a browser instead of an app, your VESkey is stored in the browser local storage. In this case the VES browser extension becomes the next level redundancy. The VES extension guards against the VESkey being inadvertantly erased by the user from the browser local storage. For privacy reasons, most browsers have an option to erase the local memory and this will also delete the VESkey. The VES extension prevents this from happening as there is no user option to clear the memory in the VES extension.
3rd party services that are app based and not browser based store the key in the app itself and subsequently not at risk from clearing the browser local storage. The VES browser extenstion is not applicable for direct use with these apps. However, users of these apps can still benefit from the VES browser extension when used with the Add Another Browser/App redundancy listed below.
Level 3: Add Another Browser/App
An additional copy of the VESkey is stored in each Browser/App that is added. This can be done on the same device itself by adding the browser in addition to the 3rd party app, but even better it can be done accross multiple devices. The more devices added, the better as this protects against key loss resulting from losing the device itself. Having two or more devices with your VESkey very significantly protects against the risk of key loss. It also allows you to use your app on all your devices.
In addition to having multiple devices, you can have more than one key redundancy on the same device if a brower is added even if the VESkey is stored in a 3rd party app. In this case, while the VES browser extension is not applicable with the 3rd party app, it can be used to add additional redundancy to the browser.
Level 3+: PIN/VESkey
Having a browser with the VES extension enabled on all your devices even with 3rd party apps provides another dimension of level 3 redundancy. In such a case, even if the app itsel becomes unusable for some reason, for instance in the unlikely event there is some sort of global hack to the app that destroys the 3rd party app on all your devices, you can still use the browser to retrieve a copy of your app key. Simply select the View My Keys option, enter your PIN and retrieve a copy of the app key.
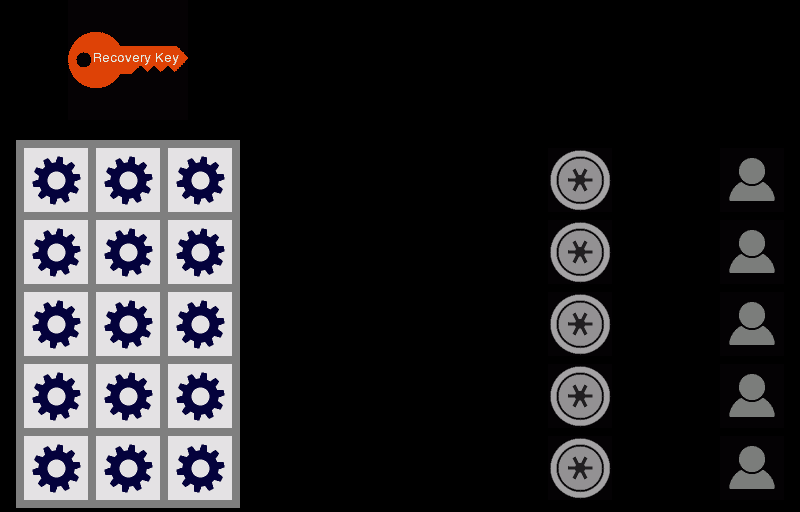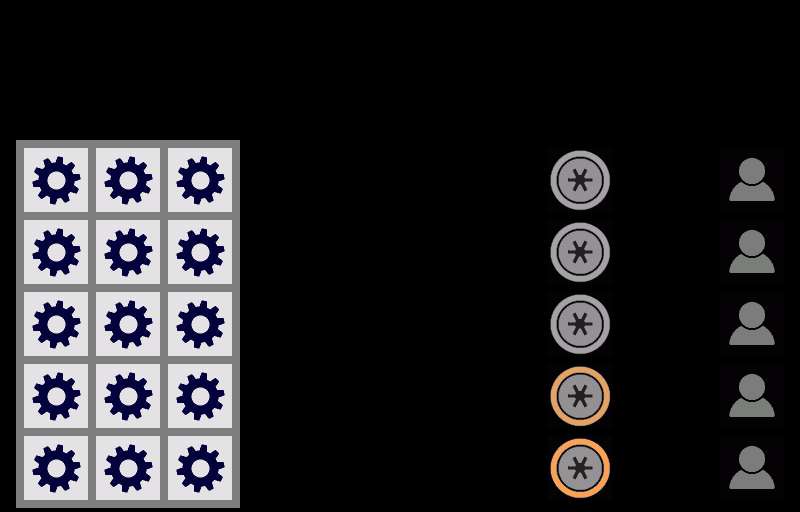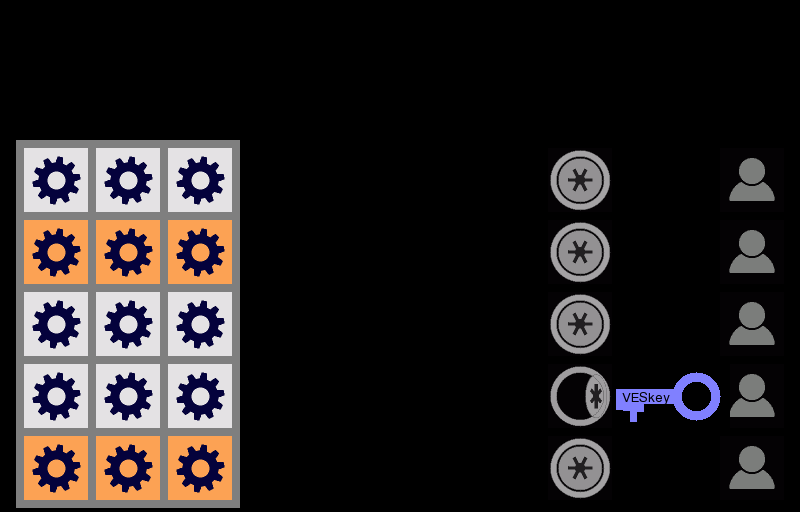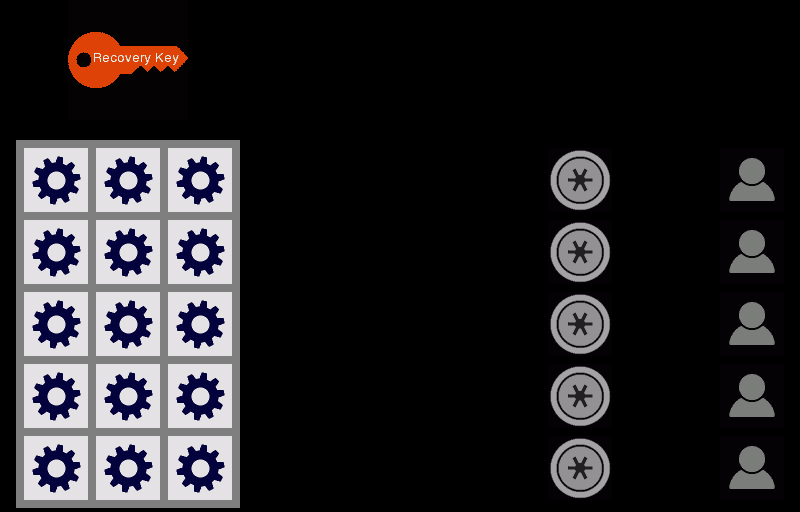
Level 4: VESrecovery
1 in 14 trillion...VESrecovery can become that safe, and even safer, from key loss. When your VESrecovery network is just being set up, it may not provide much protection from key loss. But, that will change very quickly as your network grows just a little and eventually, VESrecovery should become the safest, most robust key redundancy of all the options.
The 1 in 14 trillion estimation is based on a network of only 7 friends, each having more than one device with their connected VES accounts, and any 2 of the 7 being able to assist you by entering their PINs on one of their devices. What are the odds that any single person - you or your friends - either forgets their PIN or all the VESkey locations on all their devices becomes inaccessible simultaneously? Do people forget their PINs once every 100 days, or 1%? Do they lose all their devices simultaneously once every hundred days, again 1%? Probably not. So we went with 1% to be conservative. Using that 1%, and needing 2 of the 7 of your friends to be operational results in the 1 in 14 trillion.
And, if your seven friends each have seven unique friends of their own, the cascading effect of this viral network dramatically lowers the odds even more. And, there's no limit to the depth of your VES network.
Use the The Math VESrecovery interative calulator to recreate these odds, or change the inputs to estimate risk scenarios for your personal situation.
Level 5: VESkey/app key paper copies
When it comes to encryption, you should ALWAYS have paper copies of your VESkey and app keys stored safely in one or more separate locations. Write them down on paper and put them some place safe. Or, copy them to a USB thumb drive that does NOT bet backed up to the cloud.
Never store an electronic version of your encryption keys on your devices because your computer, phone or tablet might get backed up to the cloud. If it does, there will be a readable copy or your keys in the cloud.
Level 6: 3rd party app redundancy
The 3rd party app may have an additional redundancy that can be used outside of VESvault to retrieve your content. In the case of crypto wallets that are secured by VESvault, the 3rd party may provide a wallet seed that can regenerate the wallet encryption key. If that's the case, you will be able to use the seed to retrieve your crypto wallet contents.
As with the hardcopy of your VESkey and app key, you should store a hardcopy of the wallet seed in a safe place. NEVER store it electronically on a device that gets backed up to the cloud.
Encryption algorithms
VES uses open source, industry standard encryption alogorithms, which have never been known to have been hacked.
No shared master key
Your VESkey is the master key required to decrypt all of your encrypted content in your primary VESvault. The only place your VESkey resides is the local storage of the browsers on each of your devices that have been enabled with your VES account. There are no other copies of your VESkey, anywhere. It is not shared with anyone, including VESvault Corp.
Your VESkey is stored similarly to how your passwords to various websites are stored in your browser, but it is also encrypted with your PIN for extra security. Without your PIN, your VESkey is inaccessible. For added security to guard against multiple PIN hacking attempts, your PIN works with a special component that resides in our innovative VESlocker in the cloud. By itself, this component is useless in decrypting your VESkey.
All encryption and decryption occurs on the same local device on which the VESkey is stored, achieving full end-to-end encryption.
No collusion risk
VESrecovery is a breakthrough innovation of a highly reliable way to recover encrypted content if the master key is lost or inaccessible, without creating the risk of collusion from friends who have tokens that can be combined to construct an encryption key. It eliminates the collusion backdoor that otherwise dilutes the security of end-to-end encryption.
The cornerstone the enables VESrecovery to mitigate collusion risk is the use of a shadow vault and shadow key.
Shadow vault & shadow key
The shadow vault is a mirror image of the content in the primary vault, but with the critical distinction that it is not encrypted by the VESkey but rather by the shadow key. The VESkey cannot decrypt the shadow vault and the shadow key cannot decrypt the primary vault. The shadow key is encrypted by the recovery key. Using a process similar to Shamir's, the recovery key is converted into a series of tokens, each of which is useless by themselves in reconstructing the recovery key. A pre-defined number of these tokens must be used collectively to reconstruct the recovery key.
The improbability of collusion
The best way to show that the collusion risk is neutralized is to walk through the path a collusion hack would have to take to be successful.
The first barrier is that this risk is limited to the small number of people the you personally know and selected as friends to help you in VESrecovery. What are the odds that two or more of the ten or so of these trusted friends actually have nefarious intentions towards you?
The second barrier is that if you've set up VESrecovery properly, it takes tokens from multiple friends to recreate the recovery key. How would one nefarious person mistakenly selected by you, identify who your other friends are because that information is not available to them through VESvault. Then that person risks reaching out to sway your other friends to partake in this plot against you because it can't be a pre-arrange team.
The third barrier is that even if they were technically competent enough to reconstruct your recovery key, it is useless to them. Your recovery key is different from your VESkey, so it is useless in decrypting any of the contents of your primary vault. It's also useless in decrypting your shadow vault because the shadow key is needed for that. Thus, they need your encrypted shadow key along with your encrypted shadow vault and the only way to do that is a backend hack into the VESvault system. That backend hack is the third barrier to this collusion risk path. For security reasons, we don't disclose our internal security measures, so let's just say that we use state-of-the-art security measures in terms of protecting the encrypted content in VESvault.
VESlocker
Even if a hacker were to get access to one of your devices, they could not gain access to your primary vault without your PIN. Assuming they don't know it, they only way to get it would be brute force multiple attempts.
VESlocker ensures this can't happen. VESlocker shuts down access after multiple failed PIN entries. Since VESlocker holds a critical piece that is necessary in use with your PIN to decrypt your VESkey, the hacker cannot gain access to your VESkey without VESlocker approval. Thus, a front door hack of using your PIN on your VES enabled device is mitigated.
VESlocker essentially creates hardward level PIN access security for software. So, we made it open source so that other SAAS providers can benefit from this technoloy.
Security Time Delay
Security Time Delay is a breakthrough innovation that acutally gives you the ability to stop any front door hack in progress, before the attack can be completed. You don't have to rely on technology to stop the hack. It puts you control!
Security Time Delay was an essential design aspect in the creation of the shadow vault. It is complementary to VESlocker in that while VESlocker blocks a front door hack by a bad actor attempting to gain access to your primary vault via your PIN, Security Time Delay blocks the end around approach of a hacker who may or may not have access to one of your devices but is bypassing the PIN process by initiating VESrecovery on behalf of your account.
When you setup your VESrecovery settings you specify the duration of your Security Time Delay. This safeguard delays transmitting the encrypted contents of your shadow vault until the time duration expires. Whenever VESrecovery is initiated for your account, an email alert is sent to your email address notifying you and giving you the option to stop the process by entering your PIN if you did not initiate it. As long as you have access to one of your devices that is both VES enabled and receives email, you will get the alert and be able to stop the hack.
You should set the time delaay a little longer than the worse case scenario time duration between occurrences of accessing your email account. For instance, 12 hours may be sufficient since it more than covers the amount of time you're asleep. Or, perhaps a day or two or even a week or so would be better if you're off grid for a number of days. Since it's user adjustable, you can set the ideal duration for you.
Connected apps
VESmail VESencrypt (Docker container)
For SAAS providers
If you're interested in connecting your SAAS to VES, go to ves.host
| Level 0 | Odds Of Losing Your Data |
|---|---|
| Just You total people in your network. | 1 in |
| Level 1 | Odds Of Losing Your Data |
|---|---|
| + Your Friends total people in your network. | 1 in |
| Level 2 | Odds Of Losing Your Data |
|---|---|
| + Your Friends' Friends total people in your network. | 1 in |
| Level 3 | Odds Of Losing Your Data |
|---|---|
| + Your Friends' Friends' Friends total people in your network. | 1 in |
| Level 4 | Odds Of Losing Your Data |
|---|---|
| + Your Friends' Friends' Friends' Friends total people in your network. | 1 in |
| Level 5 | Odds Of Losing Your Data |
|---|---|
| + Your Friends' Friends' Friends' Friends' Friends total people in your network. | 1 in |