- Notifications
You must be signed in to change notification settings - Fork 19
Add ransomware alert schema #96
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Changes from all commits
008f672 b645f8d 441d18d f67a5fc 350a23c 1b647bc 546de84 0a3134d 656a032 a851b4d 961b4a6 c8b4972 File filter
Filter by extension
Conversations
Jump to
Diff view
Diff view
There are no files selected for viewing
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,84 @@ | ||
| --- | ||
| - name: Ransomware | ||
| title: Ransomware | ||
| group: 2 | ||
| short: These fields contain information specific to ransomware alerts. | ||
| description: > | ||
| These fields contain information specific to ransomware alerts. | ||
| type: group | ||
| fields: | ||
| - name: feature | ||
| level: custom | ||
| type: keyword | ||
| description: Ransomware feature which triggered the alert. | ||
| | ||
| - name: score | ||
| level: custom | ||
| type: double | ||
| description: Total ransomware score for aggregated file events. | ||
| | ||
| - name: version | ||
| level: custom | ||
| type: keyword | ||
| description: Ransomware artifact version. | ||
| | ||
| - name: child_pids | ||
| level: custom | ||
| type: long | ||
| description: Array of child PIDs for ransomware which spawns numerous processes to handle encryption. | ||
| normalize: | ||
| - array | ||
| Collaborator There was a problem hiding this comment. Choose a reason for hiding this commentThe reason will be displayed to describe this comment to others. Learn more. What does the Collaborator Author There was a problem hiding this comment. Choose a reason for hiding this commentThe reason will be displayed to describe this comment to others. Learn more. It doesn't do anything for elasticsearch right now, but it's used in some ECS core fields as well for documentation that a field is expected to be an array. Collaborator There was a problem hiding this comment. Choose a reason for hiding this commentThe reason will be displayed to describe this comment to others. Learn more. Ah thanks! | ||
| | ||
| - name: files | ||
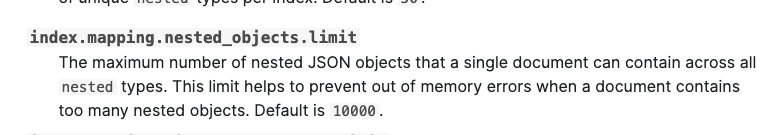
| Collaborator There was a problem hiding this comment. Choose a reason for hiding this commentThe reason will be displayed to describe this comment to others. Learn more. Do we imagine the user searching across these files? Would we need to switch it to Contributor There was a problem hiding this comment. Choose a reason for hiding this commentThe reason will be displayed to describe this comment to others. Learn more. @jonathan-buttner Yes, users would likely be interested in searching / scanning through this list to determine the extent of the breach. There was a problem hiding this comment. Choose a reason for hiding this commentThe reason will be displayed to describe this comment to others. Learn more. I feel like if we can make it searchable it sounds like a good idea but not sure if that comes at a performance cost. Note that max number of objects will be 200, on average though its probs around ~50. @jonathan-buttner how would these numbers affect Collaborator There was a problem hiding this comment. Choose a reason for hiding this commentThe reason will be displayed to describe this comment to others. Learn more. Yeah so the advantage of https://www.elastic.co/guide/en/elasticsearch/reference/current/index-modules.html If worst case is 200, I think we'll be fine. Collaborator Author There was a problem hiding this comment. Choose a reason for hiding this commentThe reason will be displayed to describe this comment to others. Learn more. @magermark Would users want to query for a specific alert based on files that are breached? Or would they only need be able to scan through the list of files after picking a specific alert based on other criteria? Even without The use case that There was a problem hiding this comment. Choose a reason for hiding this commentThe reason will be displayed to describe this comment to others. Learn more. @jared-day Do you have any opinion on the above? Is it desirable for users to be able to query for a specific file that may have been encrypted/affected? There was a problem hiding this comment. Choose a reason for hiding this commentThe reason will be displayed to describe this comment to others. Learn more. @marshallmain that was the main use case @magermark and I were thinking about - a user may want to search for a specific file that may have been affected by this kind of incident (e.g. for incident response). Is it easy to change this in the future? My view is still the same, if we can do it and it's fine performance wise then it makes sense to gives users as much flexibility as possible. Collaborator Author There was a problem hiding this comment. Choose a reason for hiding this commentThe reason will be displayed to describe this comment to others. Learn more. It's not easy to change the type of a field in the future so I went ahead and changed it to | ||
| level: custom | ||
| type: nested | ||
| description: Information about each file event attributed to the ransomware. Expected to be an array. | ||
| normalize: | ||
| - array | ||
| | ||
| - name: files.operation | ||
| level: custom | ||
| type: keyword | ||
| description: Operation applied to file. | ||
| Contributor There was a problem hiding this comment. Choose a reason for hiding this commentThe reason will be displayed to describe this comment to others. Learn more. @wburgess1 Operation is string-based here. So I take it we'll need to map the file operation dword values to their string equivalents before forming the alert? There was a problem hiding this comment. Choose a reason for hiding this commentThe reason will be displayed to describe this comment to others. Learn more. @magermark operation is only ever one int value right? So this is fine just being a Contributor There was a problem hiding this comment. Choose a reason for hiding this commentThe reason will be displayed to describe this comment to others. Learn more. Yes, that's correct | ||
| | ||
| - name: files.entropy | ||
| level: custom | ||
| type: double | ||
| description: Entropy of file contents. | ||
| | ||
| - name: files.metrics | ||
| level: custom | ||
| type: keyword | ||
| description: Suspicious ransomware behaviours associated with the file event. | ||
| normalize: | ||
| - array | ||
| | ||
| - name: files.extension | ||
| level: custom | ||
| type: keyword | ||
| description: File extension, excluding the leading dot. | ||
| | ||
| - name: files.original.path | ||
| level: custom | ||
| type: keyword | ||
| description: Original file path prior to the file event. | ||
| | ||
| - name: files.original.extension | ||
| level: custom | ||
| type: keyword | ||
| description: Original file extension prior to the file event. | ||
| | ||
| - name: files.path | ||
| level: custom | ||
| type: keyword | ||
| description: Full path to the file, including the file name. | ||
| | ||
| - name: files.data | ||
| level: custom | ||
| type: binary | ||
| description: File header or MBR bytes. | ||
| | ||
| - name: files.score | ||
| level: custom | ||
| type: double | ||
| Collaborator There was a problem hiding this comment. Choose a reason for hiding this commentThe reason will be displayed to describe this comment to others. Learn more. Same question here does this need to be a full Contributor There was a problem hiding this comment. Choose a reason for hiding this commentThe reason will be displayed to describe this comment to others. Learn more. Up to three decimal places should suffice Collaborator There was a problem hiding this comment. Choose a reason for hiding this commentThe reason will be displayed to describe this comment to others. Learn more. Gotcha, if we wanted to save some space we could probably switch it to like a https://www.elastic.co/guide/en/elasticsearch/reference/current/number.html#number | ||
| description: Ransomware score for this particular file event. | ||
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
does this need to be a
doubleor could it be a smaller float? In your example @wburgess1 they only had one decimal places I think. Will that always be the case?There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
@jonathan-buttner We typically require up to three decimal places at the moment