- Notifications
You must be signed in to change notification settings - Fork 19
Add ransomware alert schema #96
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Conversation
 magermark left a comment
magermark left a comment
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Looks pretty good, just need to update some descriptions and change metrics to an array of keywords
custom_schemas/custom_ransomware.yml Outdated
| - name: version | ||
| level: custom | ||
| type: keyword | ||
| description: Ransomware detection version. |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
description: Ransomware artifact version
custom_schemas/custom_ransomware.yml Outdated
| - name: files | ||
| level: custom | ||
| type: object | ||
| description: Information about each file targeted by the ransomware. Expected to be an array. |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
description: Information about each file event attributed to the ransomware. Expected to be an array.
custom_schemas/custom_ransomware.yml Outdated
| - name: files.entropy | ||
| level: custom | ||
| type: double | ||
| description: TODO write description and check that type is indeed double |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
description: "Entropy of file contents"
custom_schemas/custom_ransomware.yml Outdated
| - name: files.data | ||
| level: custom | ||
| type: binary | ||
| description: Combined header_string + data buffer field |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
description: File header or MBR bytes
| - name: files.operation | ||
| level: custom | ||
| type: keyword | ||
| description: Operation applied to file. |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
@wburgess1 Operation is string-based here. So I take it we'll need to map the file operation dword values to their string equivalents before forming the alert?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
@magermark operation is only ever one int value right? So this is fine just being a keyword and not say an array?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Yes, that's correct
custom_schemas/custom_ransomware.yml Outdated
| - name: files.metrics | ||
| level: custom | ||
| type: double | ||
| description: TODO idk what this is |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
metrics should be an array of strings (keywords?), so something like this:
name: files.metrics level: custom type: keyword description: Characteristics that describe uniqueness of file event normalize: - array There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I would be tempted to go with a description like:
description: Suspicious ransomware behaviours associated with the file event. custom_schemas/custom_ransomware.yml Outdated
| - name: files.score | ||
| level: custom | ||
| type: double | ||
| description: Ransomware score for this particular file. No newline at end of file |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
description: Ransomware score for this particular file event
| fields: | ||
| id: | ||
| exceptionable: true | ||
| rule: |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Would rule apply for a ransomware alert? This seems out of place here but I see it's being used for malware alerts so maybe it's safe just to leave it in just in case it's needed: https://github.com/elastic/endpoint-package/blob/master/custom_subsets/elastic_endpoint/alerts/malware_event.yaml
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Initially when making the malware schema I thought we might use rule to capture high level information about the malware module and make it easily accessible - basically treating the malware detection routine as one large rule. That hasn't happened so the fields are unused afaik. It's a core ECS fieldset though so maintaining them is free for us.
custom_schemas/custom_ransomware.yml Outdated
| - name: files.path | ||
| level: custom | ||
| type: keyword | ||
| description: File path after being ransomed |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I feel like this description (and ones above) might be slightly misleading. It's mainly the before/being ransomed that I'm uncomfortable with (and may be misleading in some circumstances).
I would be tempted to put these descriptions in more neutral language e.g. File path for suspicious file activity / File path before suspicious file activity etc.. or maybe even just File path?
Thoughts @magermark ?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I think File path is sufficient. There are circumstances (ransom notes, benign activity) where a file path isn't necessarily being encrypted, so the description should be more general.
custom_schemas/custom_ransomware.yml Outdated
| - name: feature | ||
| level: custom | ||
| type: keyword | ||
| description: Specific ransomware feature, e.g. MBR/Lua/Canaries. |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
description: Ransomware feature which triggered the alert. custom_schemas/custom_ransomware.yml Outdated
| - name: score | ||
| level: custom | ||
| type: double | ||
| description: Total score of all files ransomed. |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
description: Total ransomware score for aggregated file events. custom_schemas/custom_ransomware.yml Outdated
| - name: child_pids | ||
| level: custom | ||
| type: long | ||
| description: Array of PIDs for cases where ransomware spawns numerous child processes (e.g. lockergoga) |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
description: Array of child PIDs for ransomware which spawns numerous processes to handle encryption.  jonathan-buttner left a comment
jonathan-buttner left a comment
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Just did a quick look over, need to review more in depth.
| type: long | ||
| description: Array of PIDs for cases where ransomware spawns numerous child processes (e.g. lockergoga) | ||
| normalize: | ||
| - array |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
What does the normalize do here?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
It doesn't do anything for elasticsearch right now, but it's used in some ECS core fields as well for documentation that a field is expected to be an array.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Ah thanks!
| @@ -0,0 +1,383 @@ | |||
| --- | |||
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Could you add these:
# these fields are needed in the mapping so the maps page of the security app does not throw a bunch of errors source: fields: geo: fields: "*" destination: fields: geo: fields: "*" It's a bit of a hack to get around this issue: elastic/kibana#73304
#87
| | ||
| - name: score | ||
| level: custom | ||
| type: double |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
does this need to be a double or could it be a smaller float? In your example @wburgess1 they only had one decimal places I think. Will that always be the case?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
@jonathan-buttner We typically require up to three decimal places at the moment
| normalize: | ||
| - array | ||
| | ||
| - name: files |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Do we imagine the user searching across these files? Would we need to switch it to type: nested?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
@jonathan-buttner Yes, users would likely be interested in searching / scanning through this list to determine the extent of the breach. type: nested seems like it would be appropriate in this use case
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
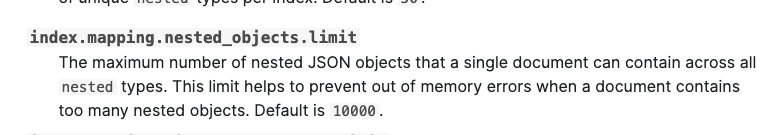
I feel like if we can make it searchable it sounds like a good idea but not sure if that comes at a performance cost. Note that max number of objects will be 200, on average though its probs around ~50. @jonathan-buttner how would these numbers affect nested limitations ?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Yeah so the advantage of nested is being able to query the objects in the array independently of each other, which is probably what we'd want to do. At endgame we ran into issues with nested objects because they have these limits by default:
https://www.elastic.co/guide/en/elasticsearch/reference/current/index-modules.html
If worst case is 200, I think we'll be fine.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
@magermark Would users want to query for a specific alert based on files that are breached? Or would they only need be able to scan through the list of files after picking a specific alert based on other criteria? Even without nested they'll be able to see all the information in files once they are looking at a specific alert document.
The use case that nested enables is a query like "find ransomware alerts where a certain ransomed file had (property 1 AND property 2)".
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
@jared-day Do you have any opinion on the above? Is it desirable for users to be able to query for a specific file that may have been encrypted/affected?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
@marshallmain that was the main use case @magermark and I were thinking about - a user may want to search for a specific file that may have been affected by this kind of incident (e.g. for incident response).
Is it easy to change this in the future? My view is still the same, if we can do it and it's fine performance wise then it makes sense to gives users as much flexibility as possible.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
It's not easy to change the type of a field in the future so I went ahead and changed it to nested.
| | ||
| - name: files.score | ||
| level: custom | ||
| type: double |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Same question here does this need to be a full double?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Up to three decimal places should suffice
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Gotcha, if we wanted to save some space we could probably switch it to like a float or maybe even half_float I think:
https://www.elastic.co/guide/en/elasticsearch/reference/current/number.html#number
| @@ -0,0 +1,392 @@ | |||
| --- | |||
| name: ransomware_event | |||
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Just double checking but we don't need any of the core file fields right?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Entries in the files array (Ransomware.files) here will greatly differ from typical core file entries, so we do not need to inherit any fields from file.
custom_schemas/custom_ransomware.yml Outdated
| - name: files.previous_extension | ||
| level: custom | ||
| type: keyword | ||
| description: Previous file extension. |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Another nitpick and feel free to ignore but I noticed in the file fields schema (
endpoint-package/schemas/v1/file/file.yaml
Line 793 in 9ca1713
| description: Original file path prior to a modification event |
description: Original file path prior to a modification event To remain consistent we could also use something like (basing the below on descriptions taken from that schema):
description: Previous file extension prior to a ransomware file event. description: Previous file path prior to a ransomware file event. description: Full path to the file, including the file name. It should include the drive letter, when appropriate There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
We might also want to use files.original.path to remain consistent with the custom file fieldset. Thoughts? Would that mean the same thing?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I think files.path is still fine for this. If anything previous_path / previous_extension could be renamed to original.path / original.extension to be more consistent with ECS 👍
| This LGTM now. The only possible change which I will defer to you @marshallmain is changing the description of As an FYI, I sanity checked |
No description provided.