Docker is the industry standard software for packaging and deploying applications in containers. Docker images are the cornerstone upon which you can build and run your applications.
To unlock Docker’s full potential, you need to optimize your images for resource efficiency, security, and performance. This will ensure your applications function seamlessly within the Docker ecosystem.
Learn how to do this with a real-world example showing how to containerize a Python calculator app.
Starting With a Minimal Base Image
One of the factors that affect a Docker image’s efficiency is the choice of the base image. You should start with a minimal image that includes only the essential components required for running your application.
The image you use should also be from a reputable source that provides security updates and patches. It should have an active community and good documentation. This is helpful when troubleshooting issues or seeking assistance.
For the calculator application, choosing python:3.11-slim-bookworm, which is a minimal image, reduces the image size. This, in turn, minimizes resource consumption and speeds up image downloads and deployments.
# Starting With a Minimal Base Image
FROM python:3.11-slim-bookworm AS builder You can use an even smaller Alpine Linux image, by opting for python:3.11-alpine. However, this image does not include a Python interpreter, a package manager, and common Python libraries.
Running Applications as Non-Root Users
Running Docker containers as a root user can pose significant security risks. If a malicious actor gains access to a container running as root, they may exploit vulnerabilities in the container's software to escalate their privileges. They can then use these privileges to execute commands with full control over the host system.
The solution is running your applications as a non-root user. The calculator example creates and configures the user calculator.
# Set non-root user for security
RUN adduser calculator --system
# Add the user to the calculator group
RUN addgroup calculator && adduser calculator calculator
Creating a dedicated user for your application limits the permissions available to potential attackers. This makes it more difficult to exploit vulnerabilities.
Copying Necessary Files and Creating a Virtual Environment
Creating a virtual environment within a Docker container isolates dependencies. This prevents conflicts with system-wide packages and other applications. It also ensures version compatibility as you can install the exact versions of dependencies your application needs, without affecting the rest of the system.
Copy the necessary files into the container. Then, create a virtual environment for the calculator application using Python's built-in venv module.
# Set working directory and copy necessary files
WORKDIR /app
COPY app.py .
COPY requirements.txt .
COPY config.json ./
# Copy config.json from the local directory
# Create a virtual environment and install dependencies
RUN python -m venv /venv
ENV PATH="/venv/bin:$PATH"
RUN /venv/bin/pip install --upgrade pip --no-cache-dir --requirement requirements.txt Virtual environments are lightweight and efficient, as they do not duplicate system-wide packages. This helps keep the Docker image size smaller and reduces resource consumption when the container is running.
Minimizing Layers for Efficiency
Each instruction in a Dockerfile creates a new layer in the resulting image. Docker uses a copy-on-write mechanism to manage these layers. Reducing the number of layers in the Docker image significantly improves image size and build performance. One way to reduce layers is by consolidating multiple commands into a single RUN instruction.
# Minimizing Layers for Efficiency
# Combine commands to reduce the number of layers
RUN echo "Build process goes here" && \
/venv/bin/python -m compileall . && \
rm -rf __pycache__ Combining the above commands reduces the number of intermediate layers created during the image build process.
Securing Configuration Handling
Handling sensitive information within a Docker image poses a security risk. To enhance security, you should use environmental variables and external configuration files. In the calculator application example, you can create a directory named /config to store your configuration file and set the appropriate ownership.
# Securing Configuration Handling
RUN mkdir /config && chown calculator:calculator /config
Then copy the config.json file into this directory, ensuring it remains separate from the application code.
# Copy the config.json file into the container
RUN cp config.json /config/config.json
ENV CONFIG_PATH=/config/config.json Segregating configuration data from the code and applying appropriate permissions enhances the overall security of your Docker image. It ensures that only authorized processes or users have access to critical configuration data.
Using Multi-Stage Builds
Multi-stage builds allow you to separate the build environment from the final image. This results in smaller, more focused production images. It also enhances security by excluding build-related tools and files from the final image. This reduces the attack surface and minimizes potential security risks associated with unnecessary components.
# Leveraging Multi-Stage Builds
FROM python:3.11-slim-bookworm
COPY --from=builder /etc/passwd /etc/passwd
COPY --from=builder /etc/group /etc/group
COPY --from=builder /venv /venv
COPY --from=builder /config /config
COPY --from=builder /app /app
# Copy the application code
The above code only copies the necessary artifacts from the build stage (builder) into the final image. This reduces the image size by excluding build-related tools and files that are not needed for running the calculator application.
Enhancing Security With Image Scanning
To further enhance the security of your Docker images, use image scanning tools like Trivy or Clair. These tools are designed to identify vulnerabilities in your image layers and dependencies. Use Trivy for the calculator app, to conduct vulnerability scanning.
# Install Trivy for Debian/Ubuntu
RUN apt-get update && \
apt-get install -y wget apt-transport-https gnupg lsb-release && \
wget -qO - https://aquasecurity.github.io/trivy-repo/deb/public.key | apt-key add - && \
echo "deb https://aquasecurity.github.io/trivy-repo/deb bookworm main" \
| tee -a /etc/apt/sources.list.d/trivy.list && \
apt-get update && \
apt-get install -y trivy Adding Trivy vulnerability scanning to your Docker image is crucial. This is because it uses the Common Vulnerabilities and Exposures (CVE) database, which is regularly updated with information about known vulnerabilities. This helps you keep your images up-to-date with the latest security patches and protect your applications from known exploits.
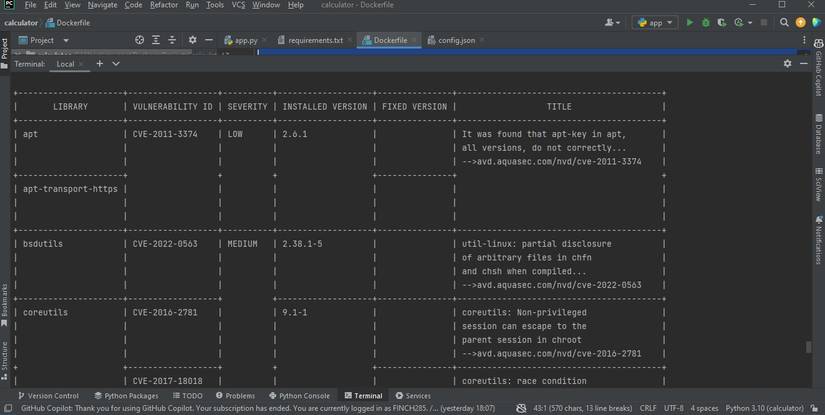
To get a vulnerability report on your image use the following command.
docker run --rm `
-v /var/run/docker.sock:/var/run/docker.sock `
-v $HOME/Library/Caches:/root/.cache/ `
aquasec/trivy:0.18.3 `
<your image name> The above command will take some time to run. Once it’s finished, it will generate a report like the one below.
The higher the severity the faster you should address the identified vulnerability.
Running Applications as Non-Root Users
To enhance security run the application as the calculator user to limit potential vulnerabilities.
# Running Applications as Non-Root Users
WORKDIR /app
USER calculator
# Activate the virtual environment and run the application
CMD ["/bin/bash", "-c", "source /venv/bin/activate && python app.py"]
Switching to a non-root user minimizes the attack surface.
Containerizing Non-Python Applications
Docker containerization of applications powered by other languages is a bit different. You should get familiar with how to containerize different types of applications. This will help you decide the best strategy to adopt based on the type of language your application is using.